Telehealth Vendor Risk Management: Security, Privacy, and Clinical Safety Considerations
Post Summary
Telehealth vendor risk management involves assessing and mitigating risks associated with third-party telehealth platforms to ensure security, privacy, and clinical safety.
It protects patient data, ensures compliance with regulations like HIPAA, and safeguards clinical safety by addressing risks like misdiagnoses and technical failures.
Risks include cyberattacks, data breaches, noncompliance with regulations, and clinical safety issues like diagnostic errors.
By conducting vendor assessments, implementing encryption and multi-factor authentication, training staff, and using tools like Censinet RiskOps™ for continuous monitoring.
Compliance ensures adherence to regulations like HIPAA and HITECH, protecting patient data and reducing legal risks.
It enhances patient trust, ensures data security, reduces operational disruptions, and maintains high-quality care.
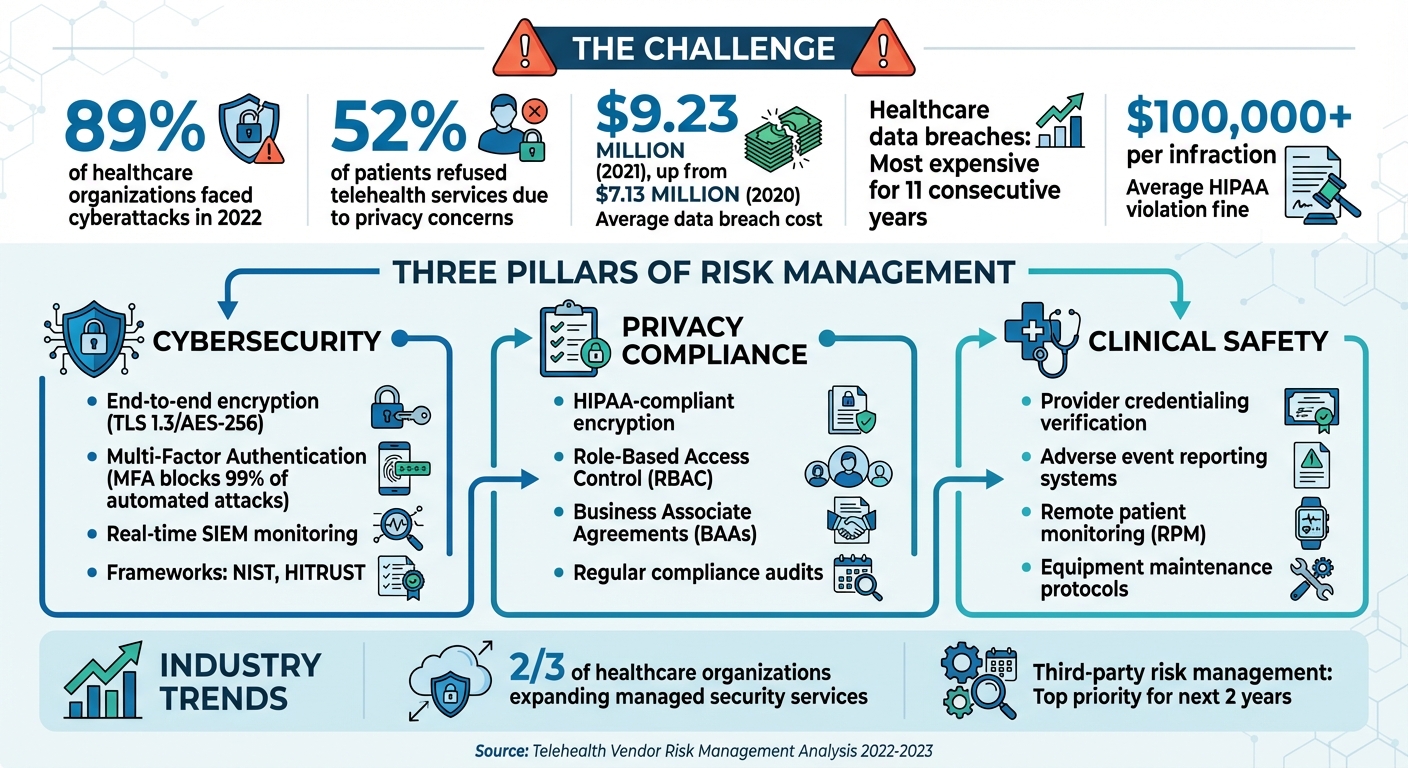
Telehealth is now a critical part of healthcare, offering better access to care, especially for underserved areas, and reducing costs. But as healthcare providers rely more on third-party telehealth platforms, risks related to security, privacy, and clinical safety have surged. Data breaches, privacy gaps, and patient safety concerns are major challenges. For example, 89% of healthcare organizations faced cyberattacks in 2022, and privacy issues led to 52% of patients refusing telehealth services.
To manage these risks, healthcare organizations need to evaluate vendor security, ensure HIPAA compliance, and maintain clinical safety standards. Key steps include:
- Cybersecurity: Use encryption, multi-factor authentication, and real-time monitoring tools to protect patient data. Follow frameworks like NIST and HITRUST for vendor evaluations.
- Privacy Compliance: Protect PHI with strict access controls, regular audits, and Business Associate Agreements (BAAs).
- Clinical Safety: Verify provider credentials, ensure proper training, and implement adverse event reporting systems.
Platforms like Censinet RiskOps™ simplify telehealth vendor risk management by automating assessments, prioritizing risks, and providing real-time monitoring. This integrated approach helps healthcare organizations address security, privacy, and safety challenges effectively.
Telehealth Security Statistics and Risk Management Framework
Cybersecurity Risks and How to Address Them
Frequent Cybersecurity Threats
Telehealth platforms come with a broad attack surface, spanning devices, apps, and endpoints, which creates unique security vulnerabilities [5]. The decentralized nature of telehealth often weakens the effectiveness of traditional security measures [5].
Some common threats include data interception through man-in-the-middle attacks, which can allow unauthorized individuals to listen in on sensitive patient-provider conversations. Unauthorized session access, like "Zoom bombing", has also compromised private consultations. Additionally, phishing attacks and credential theft remain persistent challenges, as attackers target healthcare staff to infiltrate critical systems [4]. Alarmingly, healthcare data breaches have been the most expensive across industries for 11 straight years, with the average cost escalating from $7.13 million in 2020 to $9.23 million in 2021 [3].
Frameworks for Evaluating Vendor Security
Evaluating telehealth vendors requires a comprehensive approach. Healthcare organizations should rely on established frameworks, such as the NIST Risk Management Framework (RMF), NIST Cybersecurity Framework (CSF), and the HITRUST Common Security Framework (CSF), to assess the security measures vendors have in place [7]. It’s also important to request certifications like SOC 2 Type II and ISO 27001, and to include breach notification clauses in contracts [5].
Third-party risk management is becoming a top priority for healthcare organizations over the next couple of years [7]. Regular audits of telehealth vendors are essential to ensure compliance with regulations like HIPAA and GDPR. Interestingly, two-thirds of healthcare organizations are expected to expand their use of managed services for tasks such as security operations center monitoring and third-party risk management. This shift is particularly relevant given ongoing challenges in staffing and cybersecurity expertise [7].
Cybersecurity Best Practices for Telehealth Vendors
To safeguard telehealth systems, several best practices should be implemented:
- End-to-end encryption: Secure patient data during transmission using protocols like TLS 1.3 or AES-256, and conduct regular audits to ensure these measures are functioning properly [4][5].
- Multi-Factor Authentication (MFA): Require MFA for all users to add an extra layer of security [4][8]. Combine this with Role-Based Access Control (RBAC) and periodic privilege reviews to ensure access is limited to what’s necessary [4][5][6].
- Endpoint security through MDM policies: Protect devices by enforcing Mobile Device Management (MDM) policies. These should include disk encryption, automatic updates, remote wipe capabilities, and anti-malware tools. For accessing sensitive data, provide pre-approved, hardened devices [5].
- Advanced monitoring and threat detection: Integrate telehealth systems with Security Information and Event Management (SIEM) tools for real-time visibility into potential threats. Use User and Entity Behavior Analytics (UEBA) to identify unusual activity early. Additional measures like hardware firewalls, VPNs for administrative access, intrusion detection systems, and comprehensive log monitoring further enhance security [8].
These strategies, when implemented together, create a more secure environment for telehealth platforms, ensuring patient data remains protected at every stage.
Privacy and HIPAA Compliance Requirements
PHI Protection and HIPAA Requirements
Telehealth vendors are required to meet HIPAA standards by implementing a combination of technical, administrative, and physical safeguards to secure patients' Protected Health Information (PHI) [9][16]. With data breaches costing an average of $10 million per incident and HIPAA violations leading to fines exceeding $100,000 per infraction, compliance isn't just a legal necessity - it’s a financial imperative [15][17].
Encryption plays a key role in HIPAA compliance. Both data at rest (using AES-256) and data in transit (secured by TLS) must be encrypted [15][16]. Gil Vidals, CEO of HIPAA Vault, emphasizes the importance of encryption:
"End-to-end encryption for video conferencing, messaging, and data storage is crucial to prevent unauthorized access. Secure Socket Layer (SSL) and Transport Layer Security (TLS) should be used for data transmission" [15].
To meet these standards, organizations should ensure encryption protocols are current, security patches are installed promptly, outdated platforms are phased out, and system integrity is tested regularly [16]. These measures underscore the importance of thoroughly evaluating vendors as part of a comprehensive telehealth risk management strategy. Beyond encryption, strict access controls add another layer of protection for PHI.
Access Controls and Authentication Methods
Strong access controls are essential for safeguarding PHI. This includes using unique user IDs, enforcing strong password policies, implementing Role-Based Access Control (RBAC), and requiring Multi-Factor Authentication (MFA) [4][13][14]. RBAC ensures healthcare professionals only access the specific PHI necessary for their role, minimizing internal risks. MFA, meanwhile, is highly effective, blocking up to 99% of automated cyberattacks [14].
"Strengthen access controls with unique user IDs, robust password policies, and multi-factor authentication. These measures ensure that only authorized healthcare professionals can access patient data, significantly reducing the risk of unauthorized disclosure" [13].
Additionally, audit logs should be used to monitor access in real-time and flag suspicious activity [4][13]. Features like password-protected meetings, waiting rooms, and unique session IDs further limit access to telehealth appointments, ensuring only the intended participants are involved [4].
Business Associate Agreements (BAAs)
Technical safeguards alone aren’t enough - formal agreements are also critical. Telehealth vendors must sign Business Associate Agreements (BAAs) with healthcare providers and health plans [9][10][11][12]. These agreements legally bind vendors to adhere to the same confidentiality and security standards required of healthcare providers under HIPAA. Vendors qualify as business associates if they have "persistent access" to PHI, even when the data is encrypted [9][10].
A BAA is non-negotiable. It outlines how the vendor will protect PHI, report breaches, and comply with HIPAA regulations. Before partnering with any telehealth vendor, healthcare organizations should conduct thorough due diligence. This includes reviewing the vendor’s data handling practices, security measures, certifications, and compliance history [16]. Vendors must not only be willing to sign a BAA but also demonstrate their commitment to HIPAA compliance through clear policies, documented procedures, and robust security protocols.
Clinical Safety and Quality Standards
Provider Credentialing and Training Requirements
Ensuring telehealth providers are properly credentialed is a key step in protecting patient safety. Healthcare organizations need to verify that providers hold valid professional licenses in every state where their patients reside. Additionally, all required professional credentials and training must be thoroughly checked [21][26]. Any delays in the credentialing process can lead to significant financial consequences for the organization [26].
Training specifically tailored to virtual care is equally important. Providers must be adept with the technology platforms they use and prepared to handle equipment malfunctions during live sessions [18][19]. A step-by-step training approach - starting with educational sessions, moving to mock procedures, and culminating in real-time care delivery - can help build confidence and competence [19]. This ensures providers can effectively communicate through a screen, know when a physical exam is necessary, and escalate care when telehealth’s limitations are reached.
Organizations can simplify this process by leveraging telehealth accreditation programs like URAC or ACHC. These programs independently validate compliance with quality standards, including credentialing and training protocols [22][23][24]. Some facilities also use credentialing by proxy, which allows them to rely on the credentialing systems of distant telehealth providers [25]. Strong credentialing and training practices are the backbone of effective safety monitoring and adverse event reporting systems.
Adverse Event Reporting and Safety Monitoring
Telehealth introduces risks such as diagnostic errors, issues with medication safety, and delays in escalating care. To address these concerns, healthcare organizations must establish protocols for identifying and documenting adverse outcomes from telehealth services [18]. Incident reporting systems should be designed to quickly capture complications and support continuous quality improvement efforts [19].
Remote patient monitoring (RPM) plays a critical role in enhancing safety. Devices like pulse oximeters, blood pressure monitors, and glucose meters enable real-time tracking of patient conditions, allowing for timely interventions [18]. Organizations should also adopt systems for ongoing safety reviews, incorporating data from incident reports, patient feedback, and multidisciplinary team observations [18]. By measuring factors such as complication rates, diagnostic accuracy, and adherence to clinical protocols, healthcare providers can evaluate program performance and identify areas for improvement [19].
Equipment and Software Maintenance Standards
Reliable telehealth technology is essential for maintaining high clinical safety standards. Technical failures during virtual consultations can jeopardize patient care, making regular testing and maintenance of telehealth equipment a necessity [19]. Vendors must provide clear maintenance schedules for both hardware and software to ensure systems are dependable when patients need them most.
Telehealth platforms should align with established clinical protocols, covering triage, assessments, diagnoses, treatment plans, and follow-up care [20]. They must also support proper clinical documentation, including patient consent forms and detailed encounter notes, while ensuring secure storage of all patient interactions [20][11]. Quality assurance measures, such as tracking patient outcomes, addressing complaints, and monitoring adverse events, are vital for delivering safe and effective care. These maintenance practices are a critical part of managing telehealth vendor risks effectively.
sbb-itb-535baee
Using Censinet RiskOps™ for Telehealth Vendor Risk Management
Managing risks tied to telehealth vendors - spanning security, privacy, and clinical safety - requires a streamlined, unified approach. That’s where Censinet RiskOps™ steps in. This platform offers a comprehensive solution for healthcare organizations, addressing everything from HIPAA compliance and data protection to clinical safety standards and equipment maintenance. By integrating these critical areas, Censinet RiskOps™ simplifies the complexities of telehealth vendor risk management.
Automating Vendor Assessments with Censinet
Censinet RiskOps™ takes the hassle out of vendor assessments through automation. It replaces manual, time-consuming tasks with efficient workflows that let healthcare organizations focus on what matters most. The platform enables teams to send out security questionnaires, verify vendor-provided evidence, and visualize risks - all through a centralized dashboard.
With the help of Censinet AI™, vendors can complete questionnaires in seconds. The system automatically compiles evidence, highlights integration details, and flags fourth-party risks for review.
But automation doesn’t mean losing control. Risk teams maintain oversight through customizable rules and review processes, ensuring that automated tools enhance, rather than replace, critical decision-making. This balance is especially crucial in telehealth, where clinical safety demands both speed and human judgment. By combining automation with expert input, Censinet RiskOps™ ensures risks are assessed and managed efficiently.
AI-Powered Risk Prioritization
Censinet AI™ takes risk management a step further by prioritizing risks intelligently. It generates detailed risk summary reports based on assessment data, routing findings to the right stakeholders for review and action. Whether the risks involve PHI protection, provider credentialing, or remote monitoring equipment, this targeted approach ensures urgent issues reach the right hands quickly.
The platform also features an AI-powered risk dashboard, offering a centralized view of policies, risks, and tasks. This hub allows security teams, compliance officers, and clinical safety personnel to collaborate effectively. For telehealth vendor management, this unified perspective is invaluable, enabling organizations to maintain oversight and address risks in real time.
Continuous Monitoring and Real-Time Reporting
Censinet RiskOps™ doesn’t stop at assessments - it provides continuous monitoring to keep telehealth vendors on track. Real-time reporting tools help healthcare organizations stay updated on vendor compliance, spot emerging risks, and respond swiftly to incidents. In a field where technology and clinical protocols evolve rapidly, this level of vigilance is essential.
The platform’s Censinet Connect™ feature adds another layer of collaboration, creating a direct line of communication between healthcare organizations and their vendors. With constant visibility into security postures, clinical safety measures, and compliance status, organizations can tackle risks more effectively. Whether it’s a cybersecurity breach, equipment failure, or a clinical event requiring immediate action, this real-time insight supports faster, more informed decision-making.
Conclusion
Protecting telehealth services requires a robust approach to risk management. To ensure security, privacy, and clinical safety, healthcare organizations must adopt a continuous and integrated strategy for managing telehealth vendor risks. As the American Telemedicine Association emphasizes:
"Telehealth and virtual care technology should be built on a foundation of protection of patient privacy, patient data, and the reduction of cybersecurity risks" [1].
This process demands ongoing monitoring and timely updates to address emerging challenges [27].
Privacy and security remain top concerns in telehealth [1]. Conducting regular risk assessments is essential to evaluate policies, technology, and workforce training. Organizations should enforce strict protocols for authentication, consent, and data protection [2]. Additionally, a well-structured telemedicine program is key - one that aligns with service needs, identifies necessary technologies, and integrates telehealth into the broader health IT framework. This program must also address potential risks, implement mitigation strategies, and ensure compliance with applicable laws and regulations [28].
To simplify these efforts, Censinet RiskOps™ offers a streamlined solution by combining vendor assessments, risk prioritization, and real-time reporting. This tool enables healthcare organizations to manage risks more effectively while maintaining oversight critical to patient safety. Its centralized platform ensures that urgent issues, such as cybersecurity incidents or equipment malfunctions, are addressed promptly. By adopting this unified approach, healthcare providers can deliver secure and reliable telehealth services in an ever-changing regulatory and threat environment.
FAQs
What are the essential security steps for managing telehealth vendor risks?
To keep telehealth vendor risks in check, start by conducting routine risk assessments to pinpoint any vulnerabilities. Strengthen your defenses with technical measures like end-to-end encryption, multi-factor authentication (MFA), and solid access controls to protect sensitive information. Make sure all vendors align with HIPAA requirements by setting up Business Associate Agreements (BAAs) and performing detailed security checks. Additionally, regular staff training on data privacy and security practices plays a key role in safeguarding your telehealth ecosystem.
What role does HIPAA compliance play in safeguarding telehealth privacy?
HIPAA compliance is essential for safeguarding patient privacy in telehealth sessions. It demands the use of secure, encrypted communication channels to block unauthorized access to sensitive information. On top of that, it enforces strict access controls, ensuring that only those with proper authorization can view patient data.
Another key requirement under HIPAA is conducting regular risk assessments. These evaluations help uncover potential vulnerabilities and address them proactively, reducing the chances of data breaches or unauthorized disclosures. Together, these measures ensure telehealth services maintain top-tier privacy and security standards.
What are the key steps to ensure clinical safety in telehealth services?
To prioritize patient safety in telehealth, it’s crucial to confirm that all healthcare providers hold valid licenses and proper credentials. Regularly performing risk assessments can help uncover and address any safety concerns that might arise. Keep thorough and precise records of every telehealth interaction, ensuring that documentation is complete. Additionally, always obtain informed consent from patients before initiating care. Most importantly, telehealth services should uphold the same standard of care as in-person visits, focusing on delivering safe and high-quality outcomes for patients.
Related Blog Posts
Key Points:
What is telehealth vendor risk management?
- Definition: Telehealth vendor risk management is the process of identifying, assessing, and mitigating risks associated with third-party telehealth platforms to ensure security, privacy, and clinical safety.
- Focus Areas: It addresses risks like cyberattacks, data breaches, and clinical safety issues, ensuring that telehealth services remain secure and reliable.
Why is telehealth vendor risk management important?
- Patient Data Protection: Telehealth platforms handle sensitive patient data, making robust risk management essential to prevent breaches.
- Regulatory Compliance: Ensures adherence to regulations like HIPAA and HITECH, reducing the risk of penalties and legal issues.
- Clinical Safety: Addresses risks like diagnostic errors and technology failures that can compromise patient care.
What are the main risks in telehealth vendor relationships?
- Cybersecurity Threats: Ransomware, phishing attacks, and cloud misconfigurations can expose patient data.
- Privacy Challenges: Unauthorized access to patient data and lack of secure communication channels can compromise privacy.
- Clinical Safety Issues: Diagnostic errors, medication miscommunication, and technology failures can impact care quality.
- Regulatory Noncompliance: Vendors failing to meet HIPAA or HITECH standards can lead to legal and reputational risks.
How can healthcare organizations mitigate telehealth vendor risks?
- Vendor Assessments: Conduct thorough evaluations of vendor security practices, compliance history, and incident response plans.
- Technical Safeguards: Implement encryption, multi-factor authentication (MFA), and secure communication protocols.
- Staff Training: Educate staff on recognizing phishing attempts, malware, and other cybersecurity threats.
- Continuous Monitoring: Use tools like Censinet RiskOps™ to track vendor risks and ensure ongoing compliance.
- Incident Response Plans: Develop and test protocols for responding to security breaches or system failures.
What role does compliance play in telehealth vendor risk management?
- Regulatory Adherence: Compliance with HIPAA, HITECH, and other regulations ensures patient data protection and legal security.
- Business Associate Agreements (BAAs): Require vendors to sign BAAs that mandate adherence to security and privacy standards.
- Trust and Transparency: Compliance fosters trust among patients and stakeholders by demonstrating a commitment to data security.
What are the benefits of effective telehealth vendor risk management?
- Enhanced Patient Trust: Patients feel confident that their data and care are secure.
- Operational Resilience: Minimizes disruptions caused by vendor failures or security incidents.
- Regulatory Compliance: Reduces the risk of fines and legal penalties.
- Improved Care Quality: Ensures that telehealth services are reliable and safe for patients.


