Third-Party Risk Management vs. Vendor Management: What Healthcare Leaders Need to Know
Post Summary
TPRM identifies and mitigates risks across all external partnerships, including vendors, subcontractors, and other third parties interacting with healthcare data or systems.
Vendor management focuses on managing direct contractual relationships with vendors, ensuring performance, compliance, and service quality.
TPRM addresses risks from all external entities, including indirect relationships, while vendor management focuses exclusively on direct vendors with contractual obligations.
Both practices protect patient data, ensure compliance with regulations like HIPAA, and reduce vulnerabilities in the healthcare ecosystem.
Automated platforms, centralized vendor inventories, and continuous monitoring tools streamline risk assessments and compliance tracking.
By aligning risk assessments, streamlining oversight processes, and using tools like Censinet RiskOps to manage both effectively.
Healthcare organizations face growing challenges in protecting patient data while relying on external vendors. Third-Party Risk Management (TPRM) and Vendor Management (VM) are two approaches that address this issue, but they focus on different aspects:
- Vendor Management (VM): Focuses on managing direct vendor relationships, contracts, and performance metrics. It's about ensuring vendors deliver quality services on time and within budget.
- Third-Party Risk Management (TPRM): Takes a broader view, assessing risks across the entire network of vendors, subcontractors, and affiliates. TPRM prioritizes cybersecurity, operational risks, and compliance.
Why it matters: With 60% of healthcare breaches linked to third-party vendors and the average breach cost reaching $10.93 million, healthcare leaders must understand these approaches to protect patient data, maintain compliance, and prevent disruptions.
Quick takeaway: VM ensures smooth vendor operations, while TPRM focuses on identifying and mitigating risks across the broader ecosystem. Both are essential, but TPRM is increasingly critical as threats grow in complexity.
What Is Vendor Management in Healthcare?
Vendor Management (VM) in healthcare refers to the structured process of managing relationships with external service providers and suppliers. It ensures that goods and services are delivered on time, meet quality standards, comply with regulations, and stay within budget limits [2][6].
VM plays a vital role in managing suppliers efficiently. It helps healthcare organizations control expenses, reduce risks, and get the most value from their external partners [3][5]. But it’s not just about signing contracts and making payments - it’s about ensuring vendors deliver exactly what they promised, on schedule, and at the agreed price.
The range of vendors in healthcare is extensive. Organizations rely on software providers for systems like electronic health records (EHR) and enterprise resource planning (ERP). They also engage outsourcing partners for tasks such as contact center operations, professional consultants, health risk assessments, staffing, and accounting services [3]. Another critical category includes medical devices and surgical implants, where delays in procurement can have life-threatening consequences [6].
Effective vendor management is essential to maintaining smooth operations, keeping costs under control, meeting regulatory requirements, and ensuring high-quality care. The framework relies on several core elements that drive consistent vendor performance.
Core Elements of Vendor Management
Vendor management involves a series of interconnected processes that ensure seamless collaboration with external partners. Vendor selection is the first step, focusing on finding suppliers that meet the unique needs of the healthcare industry. Contract negotiation follows, setting terms, pricing, and service level agreements (SLAs) to define the relationship.
After onboarding, performance monitoring becomes key. This involves tracking critical metrics such as system uptime, security updates, maintenance schedules, and response times to confirm vendors meet their obligations. Risk assessment identifies potential vulnerabilities in vendor operations, while compliance verification ensures adherence to healthcare regulations [2][3][6].
Centralizing vendor data - such as contracts, performance metrics, and compliance statuses - improves efficiency. Automating tasks like order processing, inventory management, and delivery tracking minimizes manual errors and saves staff time. Regular meetings with vendors promote transparency and strengthen trust [6].
These practices are not only operationally essential but also critical in addressing cybersecurity risks in healthcare.
How Vendor Management Supports PHI Compliance
A strong vendor management framework also ensures the security and compliance of Protected Health Information (PHI). When vendors handle PHI, healthcare organizations must verify that their partners meet regulations like HIPAA and HITECH through strict security protocols and credentialing [3][4][5][6].
Business Associate Agreements (BAAs) are a cornerstone of PHI compliance in vendor relationships. These agreements specify how vendors can handle PHI, define security requirements, outline breach notification procedures, and establish liability terms [7]. Vendor management ensures these agreements are actively monitored and enforced.
Using vendor scoring systems, organizations can track compliance-related metrics, such as the implementation of security patches, access controls, audit results, and incident response times. This data-driven approach transforms compliance from a one-time task into a continuous operational focus.
The risks of poor vendor management go far beyond financial penalties. A vendor’s failure to secure PHI or a data breach can damage patient trust, lead to regulatory violations, and potentially harm individuals whose sensitive information is compromised. By prioritizing robust vendor management, healthcare organizations can safeguard both their operations and their patients.
What Is Third-Party Risk Management in Healthcare?
Third-Party Risk Management (TPRM) in healthcare is all about keeping a close eye on external partners - whether that's supply chains, subcontractors (also called fourth parties), or affiliated organizations. Here's why it matters: nearly 60% of healthcare breaches involve third-party vendors, according to the Ponemon Institute [8].
TPRM involves identifying, categorizing, and prioritizing the risks that come with every external entity interacting with your organization's systems or data. These risks include cybersecurity threats, operational disruptions, and even reputational harm. Healthcare data breaches don’t come cheap either - the average cost has climbed to $10.93 million, making it the most expensive across all industries [8]. In 2023 alone, a staggering 133 million health records were exposed due to data breaches, with an average of two incidents daily in the U.S. involving at least 500 records [9].
Unlike traditional vendor management, which focuses mainly on contracts, TPRM digs deeper into the entire chain of dependencies. Cybercriminals are increasingly targeting third-party service providers because of their connections to multiple healthcare organizations. A breach in one vendor can ripple through the system, impacting numerous organizations and millions of patients [14][15]. This interconnected web of dependencies makes it critical to understand and address vulnerabilities across the board.
The Scope of TPRM in Healthcare
TPRM goes well beyond managing direct vendors. It takes into account the entire network of external relationships, including the subcontractors and service providers - referred to as fourth parties - that your vendors depend on [10][13]. Each of these connections increases the risk exposure, creating a broader attack surface [12].
Take this example: an electronic health record (EHR) vendor might rely on a cloud hosting provider, which in turn depends on data centers and security firms. This chain of reliance adds layers of potential vulnerabilities. A strong TPRM program ensures that cybersecurity measures are integrated into every third-party relationship - not just during the contract phase but throughout the entire partnership lifecycle [10][11][12].
The stakes are high. In 2023, many large-scale healthcare breaches were linked to third-party vendors handling essential services like billing or mailing [9]. When one of these vendors is compromised, the fallout can affect every healthcare organization they serve, exposing millions of patient records at once [14][15]. This interconnectedness amplifies risks across cybersecurity, operations, and reputation.
Cybersecurity and Operational Risks in TPRM
TPRM zeroes in on three main areas of risk: cybersecurity, operational, and reputational. Cybersecurity risks include data breaches, ransomware attacks, and unauthorized access to protected health information (PHI). Operational risks involve service interruptions, supply chain issues, or other disruptions that could impact patient care. Then there’s reputational risk - when a third-party incident shakes patient trust or damages the organization's public image.
To tackle these challenges, TPRM programs continuously monitor the security posture of third parties, identify vulnerabilities, and implement controls to reduce exposure across the entire network of external partnerships.
Healthcare organizations face a tough balancing act: they need to collaborate with external partners while safeguarding sensitive patient data. TPRM provides a structured approach to manage this balance, ensuring every external connection is evaluated for its benefits and potential risks.
Vendor Management vs. Third-Party Risk Management: Key Differences
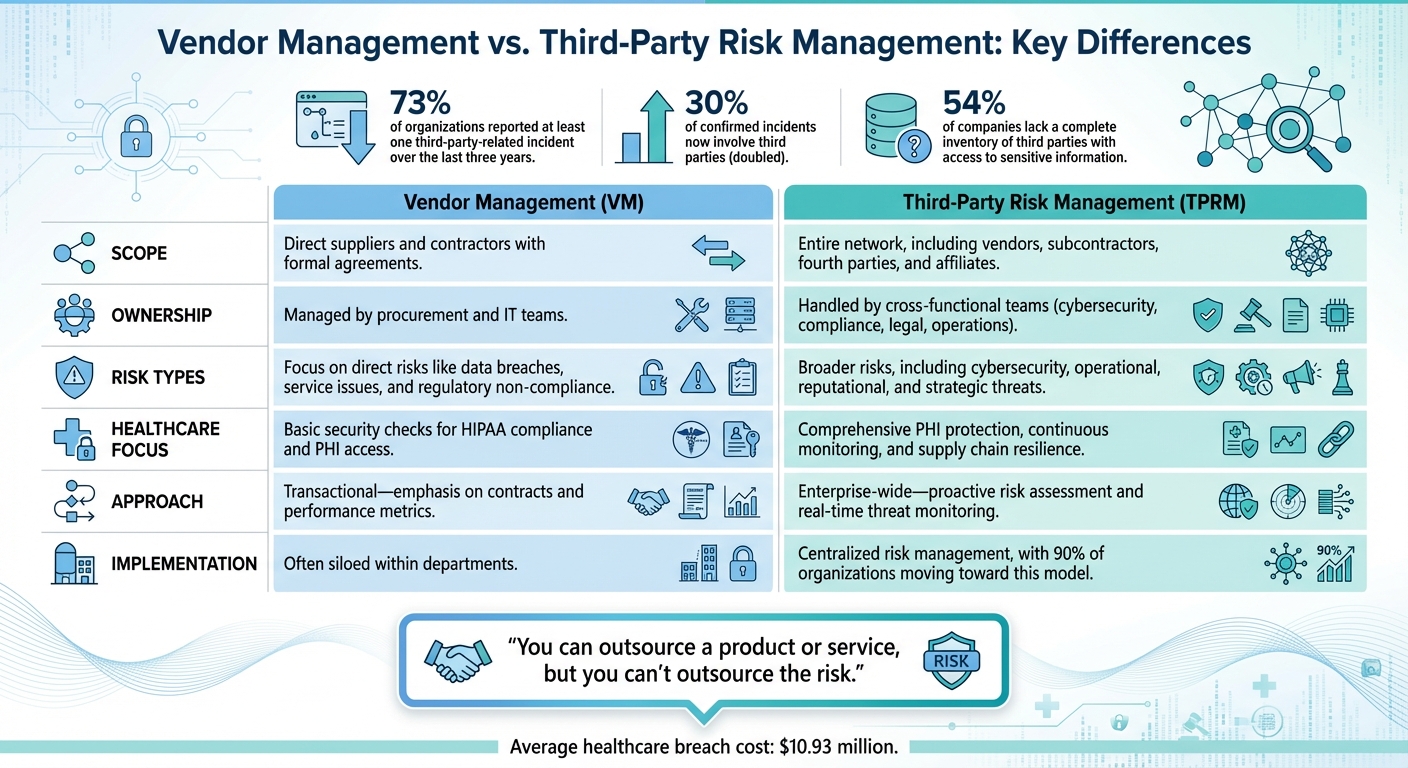
Vendor Management vs Third-Party Risk Management in Healthcare: Key Differences
While their names might suggest similarities, vendor management and third-party risk management (TPRM) serve very different purposes in healthcare organizations. The main distinction lies in their scope: vendor management zeroes in on the suppliers you directly contract with, whereas TPRM takes a broader view, analyzing risks across the entire web of external relationships, including subcontractors and service providers. This distinction is critical, as highlighted by recent data and real-world scenarios.
Consider this: 73% of organizations reported at least one third-party-related incident over the last three years [16]. Even more alarming, breaches involving third parties have doubled, now making up 30% of confirmed incidents [16]. Yet, despite these risks, more than half (54%) of companies lack a complete inventory of third parties with access to sensitive information [16]. These numbers underline the importance of distinguishing between vendor management and TPRM.
Different Teams, Different Focus
Vendor management is typically managed by procurement or IT teams, with a focus on contracts, service-level agreements, and performance metrics. On the other hand, TPRM demands a collaborative, cross-functional approach. Teams from cybersecurity, compliance, legal, and operations must work together to evaluate risks across the broader ecosystem. As Hilary Jewhurst from Venminder aptly puts it:
"You can outsource a product or service, but you can't outsource the risk" [17].
Why This Distinction Matters
The difference between these two approaches becomes starkly clear during critical incidents. Take the 2023 Change Healthcare cyberattack as an example. A single vendor compromise led to widespread disruptions in U.S. medical billing systems, delayed patient treatments, and significant financial fallout [16]. A traditional vendor management strategy might have focused solely on the vendor’s contract terms and performance. However, a TPRM approach would have proactively assessed vulnerabilities not just in Change Healthcare but also in their subcontractors and other connected entities, potentially preventing the cascading impact across the healthcare supply chain.
Vendor Management vs. TPRM: A Side-by-Side Look
Here’s a quick breakdown of how these two approaches differ:
| Feature | Vendor Management (VM) | Third-Party Risk Management (TPRM) |
|---|---|---|
| Scope | Direct suppliers and contractors with formal agreements | Entire network, including vendors, subcontractors, fourth parties, and affiliates |
| Ownership | Managed by procurement and IT teams | Handled by cross-functional teams (cybersecurity, compliance, legal, operations) |
| Risk Types | Focus on direct risks like data breaches, service issues, and regulatory non-compliance | Broader risks, including cybersecurity, operational, reputational, and strategic threats |
| Healthcare Focus | Basic security checks for HIPAA compliance and PHI access | Comprehensive PHI protection, continuous monitoring, and supply chain resilience |
| Approach | Transactional - emphasis on contracts and performance metrics | Enterprise-wide - proactive risk assessment and real-time threat monitoring |
| Implementation | Often siloed within departments | Centralized risk management, with 90% of organizations moving toward this model [16] |
sbb-itb-535baee
When to Move from Vendor Management to Third-Party Risk Management
Shifting from vendor management to third-party risk management (TPRM) isn't just a procedural upgrade - it's a necessary response to growing threats and the increasing complexity of interconnected networks. Understanding where your organization falls on this maturity spectrum is key to deciding when to expand your risk management strategy.
A staggering 61% of organizations have reported breaches involving third parties, marking a 49% increase from the previous year [12]. This sharp rise underscores the need to move beyond basic vendor oversight and adopt a more dynamic risk management approach.
Risk Management Maturity Stages
Healthcare organizations often begin with Basic Vendor Management (VM). This stage is typically reactive, relying on manual tools like spreadsheets and email to track vendors. Alarmingly, 40% of vendor contracts at this level are finalized without a security risk assessment [18]. Considering that 35% of cyberattacks in healthcare stem from third-party vendors [18], these gaps pose significant risks.
The next step is Maturing VM, where organizations start implementing structured processes and standardized questionnaires. Security assessments are conducted before contracts are signed, which is an improvement - but the scope remains narrow, focusing primarily on direct vendors. This limited perspective often overlooks risks from subcontractors or even fourth-party vendors.
Early TPRM marks a pivotal transition. At this stage, organizations broaden their focus to include the entire third-party ecosystem. Continuous monitoring replaces point-in-time assessments, offering a more comprehensive view. This shift is critical, especially in healthcare, where 55% of organizations reported third-party breaches in the past year [14]. As Ann Lyndon Duckworth from Crowe Cyber Watch explains:
"Third-party risk is a complex topic that organizations generally cannot fully establish in a short period of time. Evaluating the maturity of a third-party risk program and determining how to continually improve takes time" [14].
Finally, Mature TPRM is where organizations achieve resilience. This stage involves using centralized platforms, automated workflows, and collaborative teams to proactively identify, predict, and prevent risks. With the average cost of breaches in healthcare reaching $9.77 million [14], a robust TPRM program not only protects financial resources but also ensures uninterrupted patient care.
The urgency to advance through these stages has never been more pressing. Cyberattacks now target healthcare at an alarming rate - 23% of all attacks globally [18]. If your organization is grappling with frequent third-party incidents, limited visibility into your vendor network, or disruptions caused by vendor failures, these are clear indicators that it's time to evolve from traditional vendor management to a comprehensive TPRM framework.
How Censinet RiskOps™ Supports Third-Party Risk Management

Managing third-party risks in healthcare requires tools specifically crafted for the industry's unique challenges. As threats continue to grow in complexity, platforms like Censinet RiskOps™ are becoming indispensable. By automating processes, offering real-time insights, and fostering collaboration with vendors, Censinet RiskOps™ simplifies third-party risk management (TPRM) for healthcare organizations.
Censinet RiskOps™ Features
Censinet RiskOps™ brings efficiency and clarity to risk management. One standout feature is 1-Click Sharing, which allows vendors to complete security questionnaires, upload evidence just once, and instantly share this information with an unlimited number of customers. This feature significantly speeds up onboarding, benefiting over 100 provider and payer facilities within the Censinet Risk Network [19][20].
The platform also employs automated risk scoring to provide real-time residual risk ratings [19]. Through Delta-Based Reassessments, only changes to questionnaires are reviewed, cutting reassessment times to less than a day [19]. Additionally, its Risk Tiering and Reassessment Scheduling tools automatically sort third parties based on factors like business and clinical impact or exposure to protected health information (PHI), while scheduling regular reassessments for high-risk vendors [19].
For comprehensive oversight, the Digital Risk Catalog™ and continuous monitoring features include breach alerts and active portfolio management. With data on over 40,000 vendors and products, users can apply portfolio-wide filters to identify vulnerabilities tied to known exploits [19]. Furthermore, Censinet RiskOps™ enables organizations to benchmark their cybersecurity efforts against frameworks like NIST CSF 2.0 and HICP [21][22].
Benefits of Censinet RiskOps™ for Healthcare Organizations
Brian Sterud, CIO at Faith Regional Health, highlighted the platform's strategic value in a 2025 statement:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters" [21].
Conclusion
Healthcare organizations are under growing pressure to protect patient data while juggling a growing web of third-party vendors. Traditional vendor management often focuses on contracts and service delivery but tends to overlook deeper cybersecurity risks. Shifting to a thorough third-party risk management (TPRM) approach is now critical for ensuring patient safety and complying with regulations like HIPAA.
"Third-party risk management is crucial in today's interconnected healthcare landscape, especially amid developments in artificial intelligence, which can empower bad actors while further complicating data protection in healthcare." – HealthTech Magazine [1]
To move beyond basic vendor management, healthcare leaders need to conduct detailed evaluations of vendors' security measures and implement strict security protocols aligned with established industry standards [1].
Tools like Censinet RiskOps™ make this transition more manageable by automating risk assessments and enabling continuous monitoring. This allows healthcare organizations to strengthen their security posture, allocate resources effectively, and protect both patient care and sensitive data. With advanced cybersecurity benchmarking, organizations can demonstrate their dedication to safeguarding patient well-being.
FAQs
What is the difference between Third-Party Risk Management (TPRM) and Vendor Management (VM) in healthcare?
Third-Party Risk Management (TPRM) is all about identifying, evaluating, and addressing risks from any external entity connected to a healthcare organization. This includes not just direct partners but also indirect connections, like subcontractors. The goal? To ensure the entire network stays secure and follows compliance rules.
Vendor Management (VM), on the other hand, has a narrower focus. It’s centered on managing direct vendor relationships - making sure they meet contract terms, deliver on performance expectations, and adhere to required regulations.
To put it simply: TPRM casts a wide net, tackling risks from all external players, while VM zooms in on the direct vendors an organization works with.
Why is managing third-party risks so important for healthcare organizations?
Healthcare organizations rely heavily on third-party vendors to provide critical services such as electronic health records, telehealth solutions, and medical devices. While this partnership enhances operational efficiency, it also brings potential vulnerabilities. These include cybersecurity threats, the risk of vendor service interruptions, and compliance challenges, particularly with increasingly stringent regulations.
Taking a proactive approach to managing these risks is essential. It helps safeguard sensitive patient information, ensures continuous care delivery, and supports adherence to regulatory requirements in a constantly changing environment.
What are the main benefits of a robust Third-Party Risk Management (TPRM) program in healthcare?
A thoughtfully crafted TPRM program in healthcare brings multiple advantages. One of the most critical is reducing risk exposure by pinpointing and addressing vulnerabilities tied to third-party vendors. This proactive approach helps protect against potential threats.
Another major benefit is bolstered data security. With sensitive patient information at stake, a solid TPRM program ensures data is safeguarded from breaches or unauthorized access, keeping trust intact.
On top of that, TPRM helps organizations stay compliant with healthcare regulations like HIPAA. This not only shields your organization from hefty fines and legal troubles but also reinforces ethical practices. By promoting vendor accountability and ensuring smooth operations, a strong TPRM framework supports the delivery of consistent, high-quality care while keeping disruptions to a minimum.
Related Blog Posts
Key Points:
What is third-party risk management (TPRM) in healthcare?
- TPRM focuses on identifying and mitigating risks across all external partnerships, including vendors, subcontractors, and other third parties interacting with healthcare data or systems.
- It ensures that all third parties handling Protected Health Information (PHI) adhere to strict security measures, such as encryption and access controls.
- TPRM also addresses risks from indirect relationships, such as subcontractors hired by vendors, to prevent vulnerabilities in the healthcare ecosystem.
What is vendor management in healthcare?
- Vendor management focuses on managing direct contractual relationships with vendors that provide products or services to healthcare organizations.
- It involves negotiating contracts, setting performance metrics, and ensuring compliance with healthcare regulations like HIPAA.
- Vendor management spans the entire lifecycle of a vendor relationship, from onboarding to offboarding, ensuring service quality and cost control.
How does TPRM differ from vendor management?
- Scope: TPRM addresses risks from all external entities, including indirect relationships like subcontractors, while vendor management focuses exclusively on direct vendors with contractual obligations.
- Focus: TPRM emphasizes risk identification and mitigation, while vendor management prioritizes performance, compliance, and service quality.
- Regulations: TPRM must address broader regulatory requirements, such as HIPAA, HITECH, and FDA standards, while vendor management focuses on BAAs, performance metrics, and compliance with healthcare standards.
Why are TPRM and vendor management important in healthcare?
- Protect patient data: Both practices safeguard sensitive patient information from breaches and misuse.
- Ensure compliance: They help healthcare organizations meet regulatory requirements, such as HIPAA and HITECH.
- Reduce vulnerabilities: By addressing risks and ensuring vendor accountability, TPRM and vendor management minimize operational disruptions and cybersecurity threats.
- Support operational resilience: These practices ensure that vendors and third parties can sustain critical services during emergencies or cyberattacks.
What tools can healthcare organizations use for TPRM and vendor management?
- Automated platforms: Streamline risk assessments, contract management, and compliance tracking.
- Centralized vendor inventories: Manage vendor data, track compliance, and streamline audits.
- Continuous monitoring tools: Provide real-time alerts for security issues and compliance changes.
- AI-driven solutions: Enable predictive risk analysis and proactive mitigation strategies.
How can healthcare organizations integrate TPRM and vendor management?
- Align risk assessments: Use a unified framework to evaluate risks across all external partnerships.
- Streamline oversight processes: Centralize vendor and third-party data to improve efficiency and visibility.
- Leverage technology: Use tools like Censinet RiskOps to automate workflows, monitor risks, and ensure compliance.
- Foster collaboration: Engage IT, legal, and compliance teams to strengthen risk management efforts.


