Top 7 Encryption in Transit Best Practices for HDOs
Post Summary
It protects ePHI from interception and helps HDOs maintain HIPAA compliance.
TLS 1.3, due to stronger ciphers, forward secrecy, and faster performance.
For secure messaging, patient portals, telehealth, and any PHI leaving internal networks.
VPNs encrypt all traffic between external devices and HDO systems to prevent ePHI exposure.
It provides industry‑standard protection backed by strong key management and HIPAA‑aligned controls.
It centralizes encryption assessments, monitors vendor compliance, and supports continuous risk management.
When healthcare data moves between systems - like EHRs, patient portals, or telehealth platforms - it’s vulnerable to interception. Encryption in transit protects this sensitive information, ensuring compliance with HIPAA and safeguarding patient privacy. Here’s a quick guide to the 7 best practices for securing electronic protected health information (ePHI) during transmission:
Encryption isn’t optional - it’s a critical step to secure patient data, comply with regulations, and maintain trust. These practices reduce risks, prevent breaches, and demonstrate a commitment to privacy.
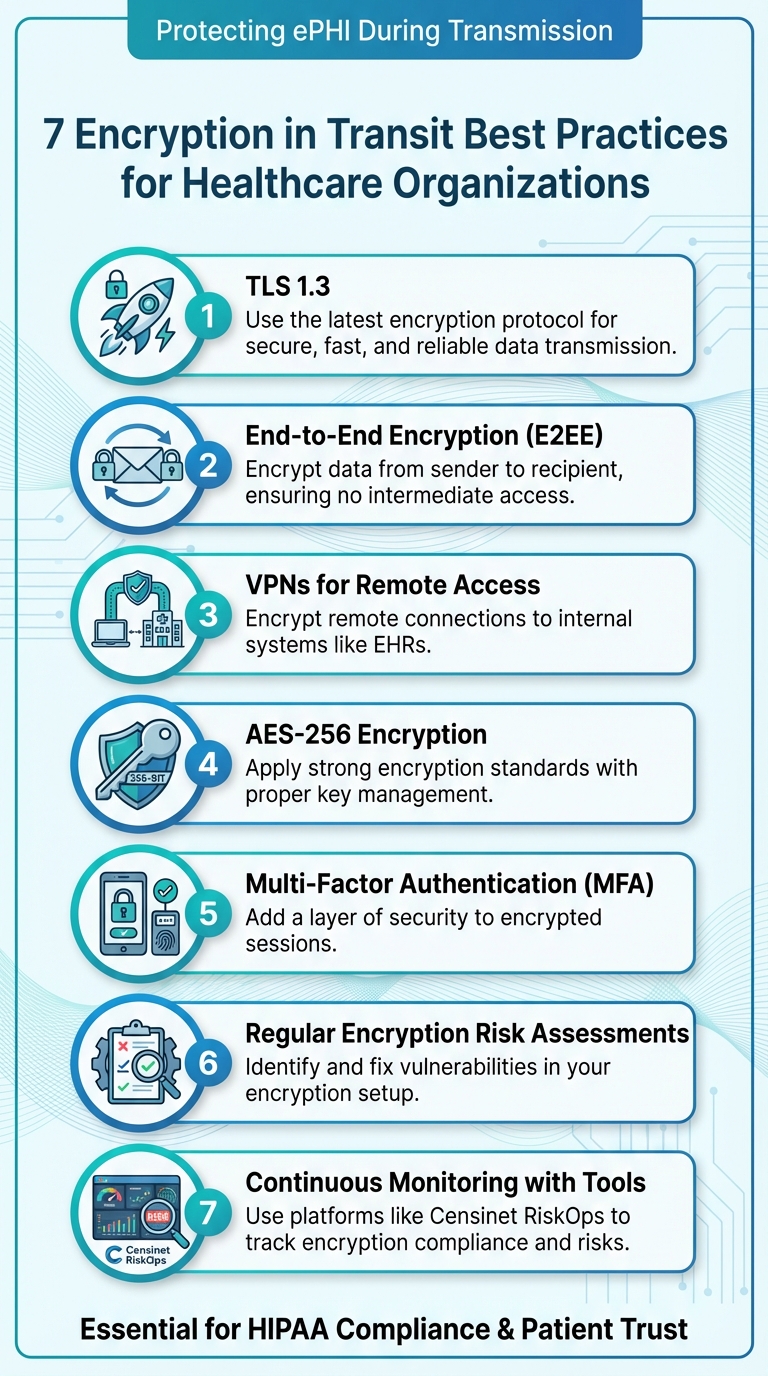
7 Essential Encryption in Transit Best Practices for Healthcare Organizations
1. Use TLS 1.3 for All Data Transmissions
Transport Layer Security (TLS) 1.3 is the go-to protocol for encrypting data in transit. It delivers stronger encryption, ensures forward secrecy by default, and eliminates outdated algorithms that could leave sensitive health information vulnerable to interception [3][4]. This protocol is a critical foundation for safeguarding patient data across healthcare systems.
Meeting Healthcare Compliance Standards
Under HIPAA's Security Rule, healthcare entities must secure electronic protected health information (ePHI) during transmission. Both the Department of Health and Human Services (HHS) and the National Institute of Standards and Technology (NIST) emphasize strong encryption, like TLS 1.3, as a key measure. Proper encryption can even qualify for HITECH breach safe-harbor, meaning intercepted encrypted data that’s unreadable won’t trigger breach notifications [2][5][7]. This reduces both regulatory risks and the burden of reporting when encrypted network traffic is compromised [5][7].
Strengthening Patient Data Security
TLS 1.3 takes encryption to another level by minimizing risks like interception and downgrade attacks. It achieves this through a faster handshake process and by removing outdated features such as RSA key exchange and weak ciphers. Instead, it defaults to secure, forward-secret key exchanges, ensuring that even if attackers later get access to server keys, they can’t decrypt past sessions [3][4]. This not only protects sensitive technical systems but also reinforces patient trust by prioritizing their privacy. Plus, its improved performance is ideal for latency-sensitive tasks like telehealth and accessing cloud-based electronic health records (EHRs) [3][4].
Simplifying Implementation for Healthcare IT
To protect ePHI effectively, focus on securing all network paths that traverse untrusted or semi-trusted environments [3][4][7]. Start by enforcing TLS 1.3 or a combination of TLS 1.2 and 1.3 (with a preference for 1.3). Disable outdated protocols and require strong, authenticated cipher suites [3][4]. For certificates, stick to trusted Certificate Authorities (CAs), consider enabling certificate pinning when appropriate, and automate certificate renewals to avoid service disruptions [3][4].
Enabling Continuous Monitoring and Risk Management
A solid TLS 1.3 setup is just the beginning; continuous monitoring is key to maintaining compliance and mitigating risks. Use automated TLS scans to spot endpoints that allow weak protocols or ciphers, and deploy network monitoring tools to flag any use of plaintext protocols or outdated TLS versions [3][4]. Healthcare-specific risk management platforms, like Censinet RiskOps™, can centralize data on third-party and internal risks. These tools help healthcare delivery organizations (HDOs) track encryption compliance, identify gaps, and improve TLS implementation across clinical applications and medical devices [2][5].
2. Apply End-to-End Encryption Protocols
Compliance with Healthcare Regulations
End-to-end encryption (E2EE) adds another layer of security to data transmission by ensuring that decryption happens only at the final endpoint. This means data stays encrypted from the moment it leaves the sender until it reaches its intended recipient, blocking any intermediate systems from accessing plaintext information [4]. While HIPAA's Security Rule considers encryption "addressable" rather than mandatory, guidance from the Department of Health and Human Services (HHS) and proposed updates treat strong encryption during transmission as an essential practice for protecting electronic protected health information (ePHI) [2][7]. E2EE helps healthcare delivery organizations (HDOs) meet these expectations by minimizing the exposure of sensitive information during transit [9][5]. When paired with TLS protocols, E2EE offers a layered defense. Even if encrypted data is intercepted, it remains unreadable, reducing the likelihood of such incidents being classified as reportable breaches by the Office for Civil Rights (OCR). This can significantly lower regulatory and financial risks [5][7].
Effectiveness in Securing Patient Data During Transmission
The strength of E2EE lies in its ability to keep data secure, even if attackers intercept network traffic or compromise third-party servers. Any intercepted data remains encrypted and unreadable, offering robust protection for sensitive information such as secure messaging between patients and clinicians [4][5]. When E2EE is combined with TLS 1.2+ or TLS 1.3 protocols and encryption algorithms like AES-256, it creates a powerful defense that makes it extremely difficult for attackers to exploit protected health information (PHI) during transmission [12][4].
Ease of Implementation Within Healthcare IT Systems
E2EE can be seamlessly integrated into existing healthcare IT systems without disrupting daily workflows. For example, secure messaging platforms and patient portals with built-in E2EE can connect directly to electronic health record (EHR) systems, ensuring that messages and attachments remain encrypted while appearing as standard inbox items for clinicians [9][5]. Email platforms can also be configured to automatically encrypt communications involving PHI [5]. Additionally, secure APIs and SDKs from vendors that support E2EE can be used for mobile apps and telehealth solutions, allowing encryption and key management to operate behind the scenes without manual intervention [12][4]. Training efforts should emphasize when secure communication channels are necessary - such as any time PHI leaves the internal network - while the technology itself ensures encryption is applied consistently, eliminating extra steps for clinicians [9][2]. This streamlined approach not only simplifies implementation but also enhances ongoing monitoring.
Support for Continuous Monitoring and Risk Management
By limiting the number of systems that handle PHI in plaintext, E2EE significantly reduces the risk of interception [9][2]. Healthcare organizations can document that E2EE-secured channels mitigate these risks, offering strong evidence for compliance [9][2][7]. Platforms with E2EE capabilities often include centralized logging features, such as audit logs that track message access, key usage, and failed decryption attempts. These logs can be integrated into Security Information and Event Management (SIEM) tools to monitor for unusual activity in real time [9][4]. Solutions like Censinet RiskOps™ further enhance risk management by evaluating vendor support for E2EE, verifying key management practices, and ensuring alignment with organizational policies. This continuous oversight strengthens encryption strategies and provides comprehensive protection for PHI during transit [5].
3. Require VPN Usage for Remote Access
Compliance with Healthcare Regulations
The HIPAA Security Rule requires healthcare organizations to implement safeguards for remote access to electronic protected health information (ePHI). To meet these requirements, healthcare delivery organizations (HDOs) should enforce the use of HIPAA-compliant VPNs for all remote access. Whether clinicians, coders, or administrative staff are connecting to systems like electronic health records (EHRs), imaging platforms, or billing software from outside the organization’s trusted network, VPN tunnels ensure that traffic is encrypted using secure protocols like TLS or IPsec. This encryption meets HIPAA’s standards, protecting sensitive data during transit. By routing all remote connections involving ePHI through encrypted VPNs, HDOs can demonstrate they’ve implemented "reasonable and appropriate" safeguards, which is crucial during audits or breach investigations by the Office for Civil Rights (OCR). Since ePHI can be intercepted at various points during transmission, robust encryption ensures that any captured data remains inaccessible and unreadable to unauthorized parties [7]. This approach not only ensures regulatory compliance but also strengthens the overall security framework for remote access.
Effectiveness in Securing Patient Data During Transmission
VPNs play a critical role in safeguarding patient data by encrypting the connection between remote devices and the HDO network, preventing the interception of sensitive credentials and information. To maximize security, HDOs should configure VPNs to use AES-256 encryption along with secure key exchange methods like ECDHE, while disabling outdated protocols such as SSL and older versions of TLS (1.0/1.1) [1][3]. Adding mutual authentication - using digital certificates alongside user credentials - further reduces the risk of man-in-the-middle attacks. For workflows involving highly sensitive data, such as transmitting complete medical histories or large imaging files, combining VPN tunnels with application-level TLS 1.3 offers an additional layer of protection [1][4][7]. This multi-layered approach ensures that patient data remains secure during transmission, even in complex scenarios.
Ease of Implementation Within Healthcare IT Systems
Deploying VPNs within healthcare IT environments can be streamlined through role-based access controls, ensuring that users like clinicians, telehealth staff, and billing personnel can only access the specific applications and network segments required for their roles. Managed devices equipped with pre-configured VPN clients and single sign-on (SSO) capabilities allow for seamless and secure access. Always-on VPN configurations ensure that encryption remains active for remote work, providing continuous protection. To further enhance security, organizations should enforce policies restricting VPN access from personal or unmanaged devices unless they are equipped with robust endpoint controls like disk encryption, antivirus software, and regular updates, managed through tools like mobile device management (MDM) or endpoint detection and response (EDR) systems. Additionally, regular staff training is essential to clarify when VPN use is mandatory - such as when working from home or using public Wi-Fi - and to provide guidance on resolving connection issues without resorting to insecure alternatives [2][5][8].
Support for Continuous Monitoring and Risk Management
Effective VPN security doesn’t stop at deployment - it requires ongoing monitoring and management to maintain encryption integrity. HDOs should track VPN usage by logging details such as user identity, device type, location, session duration, and accessed resources. These logs can be integrated into a Security Information and Event Management (SIEM) system or a risk management platform to correlate with other security events [2][5][11]. Multi-factor authentication (MFA) adds another critical layer of protection, ensuring that a single compromised password cannot grant access to systems containing ePHI. By analyzing VPN and MFA logs together, HDOs can identify suspicious activity, such as repeated login failures or connections from unusual locations. Tools like Censinet RiskOps™ can centralize data on VPN configurations, encryption standards, MFA implementation, and remote access policies, offering a comprehensive view of the organization’s VPN security posture. This centralized approach not only simplifies compliance but also helps identify noncompliant vendors, contributing to a stronger risk management strategy [2][7].
4. Use AES-256 Standards with Strong Key Management
Compliance with Healthcare Regulations
AES-256 encryption aligns with the NIST-recommended controls outlined in the HIPAA Security Rule. It ensures that electronic protected health information (ePHI) remains "unreadable, indecipherable, and unusable" if intercepted during transmission [7]. While HIPAA treats encryption as "addressable", regulators increasingly view it as essential, especially with proposed updates that would mandate encryption for all ePHI, whether at rest or in transit [2][11].
Strong key management is equally critical. It provides the documentation needed to demonstrate due diligence. This involves using unique keys stored securely in hardware security modules (HSMs) or key-management services, with regular rotation and tightly controlled access [2][5]. These measures not only reduce the risk of reportable breaches but also help healthcare delivery organizations (HDOs) avoid penalties by showing encryption is implemented as a structured, controlled process - not merely as a one-off configuration.
Effectiveness in Securing Patient Data During Transmission
AES-256 encryption goes beyond compliance - it’s a powerful tool for protecting sensitive data. With its 256-bit key, AES-256 offers robust security that makes cracking it extremely challenging [3]. When paired with modern TLS cipher suites like TLS_ECDHE_RSA_WITH_AES_256_GCM, it ensures both confidentiality and integrity, shielding patient data from eavesdropping and tampering as it traverses networks and routers [4][7]. Older algorithms like 3DES and shorter keys no longer meet current HIPAA and HITECH standards, leaving organizations vulnerable to advanced attacks.
For instance, a regional hospital upgraded its EHR web portals and APIs from outdated TLS 1.0/1.1 setups to TLS 1.2+ with AES-256-GCM encryption. They also centralized key management using a cloud-based key-management system (KMS). Post-upgrade penetration tests revealed that weak ciphers and misconfigured endpoints were eliminated, which the hospital documented as a significant improvement in its HIPAA risk analysis [11]. Similarly, a multi-clinic practice replaced a legacy VPN utilizing 3DES with an IPsec VPN configured for AES-256, certificate-based authentication, and automated key rotation. This upgrade reduced the risk of credential theft and aligned the practice with modern standards for protecting remote access to ePHI [3][5].
Ease of Implementation Within Healthcare IT Systems
Implementing AES-256 encryption with strong key management enhances protection for data in transit. HDOs should use TLS 1.2 or 1.3 with AES-256 (preferably in GCM mode) while disabling outdated ciphers [4][3]. For VPNs, configurations should enforce AES-256 for IPsec or SSL tunnels, alongside certificate-based authentication and secure key exchange. Secure email gateways and messaging platforms should also rely on AES-256-backed TLS for SMTP and support end-to-end encryption for communications involving ePHI [5]. Telehealth and mobile apps should use platform TLS libraries configured for AES-256, enforce certificate pinning, and block fallback to deprecated algorithms.
Advancements like AES-NI hardware acceleration and optimized TLS implementations mitigate any performance concerns, ensuring AES-256 can handle high-volume workloads efficiently [4][3]. To further reduce latency, HDOs can adopt TLS session resumption, HTTP/2 or HTTP/3, and load balancing. For bandwidth-heavy tasks like transmitting medical imaging, encrypting data with AES-256 while compressing it beforehand can maintain user experience without compromising security [1].
Support for Continuous Monitoring and Risk Management
Effective key management involves several best practices: unique keys per environment, centralized generation and storage via HSMs or cloud KMS, strict role-based access, regular rotation (every 90 days or after a suspected breach), and detailed logging of all key lifecycle events [3]. Larger HDOs often integrate enterprise HSMs or cloud KMS with their EHRs, data warehouses, and VPNs. Smaller practices, meanwhile, tend to use managed services that simplify HSM/KMS operations while still providing AES-256 encryption and compliant key rotation policies [2][5].
During HIPAA-mandated risk assessments, HDOs should review all data flows involving ePHI to confirm consistent use of AES-256 for in-transit protection. Any outdated protocols, misconfigurations, or unencrypted channels should be flagged as risks requiring immediate attention [2][11]. Automated tools and scanners can assist by identifying endpoints that lack AES-256-capable TLS, use weak cipher suites, or show unusual activity in key-access logs [3]. Platforms like Censinet RiskOps™ streamline this process by centralizing risk assessments, including encryption standards, key management practices, and TLS configurations used by third-party vendors handling PHI [2]. By aggregating this information, HDOs can identify partners that fall short on encryption or key management and take steps to address these gaps, whether through remediation or updated contracts, while maintaining a clear view of their encryption posture across the vendor ecosystem.
sbb-itb-535baee
5. Require Multi-Factor Authentication for Encrypted Sessions
Compliance with Healthcare Regulations
Multi-factor authentication (MFA) is a critical step in strengthening access control, a key aspect of the HIPAA Security Rule. By requiring more than just a password, MFA ensures that systems handling electronic protected health information (ePHI) are better secured [2][5][7]. The Office for Civil Rights (OCR) has increasingly emphasized the importance of "modern authentication", such as MFA, for systems containing ePHI. Proposed updates to HIPAA further push for stronger safeguards to protect sensitive data [2][5].
Implementing MFA for systems like VPNs, EHRs, email platforms, and encryption key management tools demonstrates that an organization is taking "reasonable and appropriate" steps to secure ePHI. This also reduces liability in cases of credential theft or phishing attacks [2][5]. HIPAA designates encryption and related controls as "addressable", meaning if a healthcare delivery organization (HDO) opts not to implement equivalent measures, it must document and justify that decision - a task that becomes harder as cyber threats evolve [7]. The regulatory push for MFA highlights its importance, especially as a safeguard for securing patient data during transmission.
Effectiveness in Securing Patient Data During Transmission
Encryption protects data during transmission, but it doesn’t eliminate risks from stolen credentials [3][4][6]. MFA addresses this vulnerability by requiring a second authentication factor - like a one-time passcode, an authenticator app, or a hardware token - to prevent unauthorized access even if a password is compromised [2][3][5]. This added layer of security is particularly crucial for remote access systems, such as VPNs, browser-based EHR portals, and secure email or file-transfer tools, which are frequent targets for phishing and credential reuse [2][3][5].
In real-world attacks, stolen credentials can be used to log into VPNs or web-based EHR portals, enabling attackers to extract large volumes of ePHI without breaking encryption [2][5][7]. Enforcing MFA at all critical access points significantly reduces the risk of such breaches, protecting not only patient data but also the organization’s reputation and financial standing.
Ease of Implementation Within Healthcare IT Systems
Healthcare organizations need to enforce MFA across all encrypted access points, including VPNs, EHR systems, key management consoles, secure email platforms, and cloud-based patient portals [2][3][5]. Effective MFA methods include app-based one-time passwords (TOTP), push-based authenticators, and FIDO2/WebAuthn security keys, all of which offer strong protection against phishing [3][5]. However, SMS-based codes should be avoided for high-risk ePHI access due to their vulnerabilities [3].
Integrating MFA with existing single sign-on (SSO) platforms can make the process smoother for users. This approach allows clinicians to authenticate once for secure access to multiple encrypted applications, reducing disruptions. Push notifications and biometric verification methods are particularly well-suited to fast-paced clinical environments, where ease and speed are essential [5][6].
Support for Continuous Monitoring and Risk Management
To maintain MFA effectiveness, access to critical systems like key management consoles, hardware security modules (HSMs), and certificate management tools must also be tightly controlled with MFA [3][6]. Security teams should regularly monitor logs from VPNs, identity providers, and secure messaging platforms to identify suspicious activity, such as repeated MFA denials or unusual device registrations [2][5][6].
A centralized risk management platform tailored for healthcare, such as Censinet RiskOps, can help HDOs stay on top of MFA enforcement. These platforms allow organizations to assess MFA coverage across encrypted systems like TLS-based portals, VPNs, and secure messaging tools [2][5]. They also simplify documentation of MFA requirements in vendor contracts, track remediation efforts, and benchmark adoption rates across the organization. By integrating MFA status into overall cybersecurity and compliance risk scores, HDOs can ensure they’re meeting both regulatory and operational demands [2][5].
6. Perform Regular Encryption Risk Assessments
Regular encryption risk assessments help ensure that patient data remains protected as systems and technologies evolve.
Compliance with Healthcare Regulations
HIPAA's Security Rule mandates ongoing analysis to uncover potential encryption gaps in protecting electronic protected health information (ePHI) [2][7]. Since encryption is an "addressable" safeguard under 45 CFR §164.312, healthcare organizations that choose not to encrypt ePHI must perform a thorough risk analysis and implement alternative protective measures. In reality, this makes regular encryption-focused assessments almost unavoidable.
Healthcare delivery organizations (HDOs) should conduct formal encryption risk assessments at least once a year or whenever there are changes to systems, networks, or data flows [2][5]. These assessments should document decisions, remediation plans, and timelines to ensure compliance during audits by the Office for Civil Rights (OCR). Additionally, if encrypted ePHI is lost or stolen, organizations may avoid HIPAA breach notification requirements - provided their assessments confirm that encryption was implemented correctly and keys were safeguarded [7]. These evaluations serve as the foundation for verifying encryption policies and planning future security updates.
Effectiveness in Securing Patient Data During Transmission
A comprehensive encryption risk assessment goes beyond simply confirming that TLS is enabled. It involves verifying that encryption protocols are functioning correctly, testing for vulnerabilities like downgrade attacks, and ensuring end-to-end data protection across all network segments - not just between a browser and a gateway [4][6]. Because healthcare data often passes through multiple routers and intermediaries that may temporarily store or process information, each point introduces potential risks of interception [7].
These assessments should inventory all systems transmitting ePHI, including electronic health records (EHRs), patient portals, telehealth platforms, email systems, SFTP servers, mobile apps, medical devices, and third-party connections [2][5][11]. For each data flow, verify encryption protocols, ensure secure certificate and key management, and identify any weak points where traffic might revert to unencrypted or outdated methods. Validated encryption practices should then inform ongoing monitoring efforts. Penetration testing and packet capture analysis can confirm that intercepted data remains unreadable [4][6].
Support for Continuous Monitoring and Risk Management
Encryption risk assessments should be part of an ongoing risk management cycle rather than a one-time task. Findings such as outdated TLS versions, unencrypted interfaces, or poor key management should be logged in a centralized risk register, prioritized based on their potential impact on patient safety and privacy, and tracked through remediation efforts [2][5]. Continuous monitoring tools like network sensors and vulnerability scanners can help detect deviations from the established encryption baseline, such as newly exposed unencrypted services or expiring certificates [4][6].
A healthcare-specific risk management platform, such as Censinet RiskOps, can simplify this process by providing standardized questionnaires, evidence collection workflows, and centralized risk scoring tied to patient data, clinical applications, and medical devices [2][8]. HDOs can incorporate encryption requirements into vendor assessments, compare their encryption practices to industry peers, and collaborate with vendors to address vulnerabilities [2][8].
At Tower Health, CISO Terry Grogan shared, "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
7. Use Censinet RiskOps for Continuous Monitoring and Compliance

Compliance with Healthcare Regulations
Censinet RiskOps simplifies the process of managing risk assessments by centralizing key details such as ePHI flows, transmission systems, and encryption controls like TLS, VPNs, and key management [2][7]. This centralized approach ensures alignment with the HIPAA Security Rule's requirements for risk analysis and safeguards.
The platform also provides detailed documentation of controls, remediation efforts, and reviews, which are essential for HIPAA/HITECH audits. By benchmarking vendor and internal controls against healthcare-specific standards, RiskOps helps pinpoint areas where ePHI transmission may not meet current encryption best practices. This not only lowers regulatory risks but also reduces the likelihood of breach notifications [2][5][7]. Additionally, maintaining a thorough record of risk assessments and remediation actions gives auditors clear evidence that the healthcare delivery organization (HDO) has conducted necessary risk analyses and implemented safeguards deemed "reasonable and appropriate" [2][7]. When encrypted data is intercepted, the HDO can demonstrate that it was rendered "unreadable, indecipherable, and unusable", which is crucial for determining breach-notification obligations under HIPAA [5][7].
By documenting compliance in this way, RiskOps creates a strong foundation for improving data security further.
Effectiveness in Securing Patient Data During Transmission
RiskOps goes beyond compliance by actively identifying vulnerabilities in data transmission. It maps connections between HDO systems, cloud services, and vendors, enabling security teams to locate every point where PHI or ePHI is transmitted. This ensures that protocols like TLS 1.3, HTTPS, secure APIs, and VPN tunnels are consistently applied [3][10][11]. Through its assessments, the platform uncovers weaknesses such as outdated encryption protocols, missing VPN requirements for remote access, or inconsistent multi-factor authentication (MFA) on encrypted sessions. These insights allow teams to prioritize fixes that address risks like interception or man-in-the-middle attacks [3][5][10].
During vendor evaluations, RiskOps uses detailed questionnaires to assess encryption practices. These include checks for TLS 1.2/1.3 usage, certificate management, secure APIs, secure file transfers, and VPN requirements for remote staff handling PHI [3][10]. The platform also generates comparative risk scores and control summaries, helping procurement and security teams focus on vendors with strong encryption and MFA protocols. For vendors that fall short, teams can negotiate remediation plans or include specific security clauses in contracts [2][10].
Support for Continuous Monitoring and Risk Management
RiskOps doesn’t stop at initial assessments - it provides continuous monitoring to keep risk management proactive. The platform tracks risk scores and remediation progress for both internal systems and third-party vendors over time [2]. Unlike static spreadsheets, RiskOps enables automated reassessments and flags vendors that fail to meet minimum encryption or MFA standards [2][5]. Its dashboards and automated reporting give security leaders a clear view of which interfaces, applications, or vendors pose the highest residual risks to ePHI in transit. With this information, teams can adjust controls or update contracts as necessary [2][5][10].
This constant vigilance ensures that HDOs remain prepared to address emerging risks and maintain robust security for sensitive patient data.
Conclusion
Encrypting patient data while it’s in transit isn’t just a regulatory checkbox for HIPAA compliance - it’s a critical step in safeguarding sensitive information and maintaining patient trust. The seven best practices - TLS 1.3, end-to-end encryption, VPNs, AES-256 encryption with strong key management, multi-factor authentication (MFA), regular risk assessments, and continuous monitoring through platforms like Censinet RiskOps - create a strong, multi-layered defense to ensure electronic protected health information (ePHI) remains secure, even if intercepted [7][10]. Ignoring these measures can leave healthcare delivery organizations (HDOs) exposed to serious regulatory violations and reputational harm.
Regulatory bodies are increasingly treating encryption as a baseline requirement for protecting data in transit. Healthcare organizations that neglect encryption could face investigations by the Office for Civil Rights, hefty financial penalties, mandatory breach notifications, and drawn-out corrective action plans [2][5]. Beyond legal consequences, failing to secure patient data can erode trust, damage an organization’s reputation, reduce patient retention, and strain referral relationships. Patients expect their personal information - such as diagnoses, medications, behavioral health details, and payment data - to remain private and secure when shared among healthcare providers, payers, and partners.
To make encryption efforts truly effective, continuous monitoring is key. This is where platforms like Censinet RiskOps come into play, helping healthcare organizations streamline their encryption management. By centralizing vendor assessments, tracking data flow inventories, and maintaining risk documentation in one healthcare-focused system, Censinet RiskOps ensures organizations can adapt to evolving threats and compliance demands [2][10]. The platform provides ongoing visibility, identifying vendors using outdated protocols or lacking MFA, and helps leaders understand residual risks tied to ePHI in transit. This proactive approach not only strengthens data security but also minimizes the financial and reputational fallout from breaches and penalties [11].
As Terry Grogan, CISO of Tower Health, noted, "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
This highlights how efficient encryption management can free up resources while enhancing security.
FAQs
Why is TLS 1.3 the best choice for securing healthcare data during transmission?
TLS 1.3 stands out as the go-to protocol for protecting healthcare data during transmission. It offers better encryption, improved speed, and lower latency compared to earlier versions. These upgrades make it a powerful tool for shielding sensitive patient information against today's cyber threats.
By simplifying communication and eliminating old security gaps, TLS 1.3 allows healthcare organizations to maintain safe and reliable data exchanges. This is essential for protecting patient privacy and staying compliant with regulatory standards.
How does end-to-end encryption protect patient data during transmission?
End-to-end encryption plays a crucial role in protecting patient data during transmission. It works by encrypting the data as soon as it leaves the sender and keeping it encrypted until it reaches the intended recipient. This means that only those with the correct decryption keys can access the information.
This approach prevents unauthorized access or interception, ensuring sensitive patient information stays private. It also helps healthcare organizations meet regulatory requirements, safeguarding both patients and the institutions handling their data.
How does Censinet RiskOps help healthcare organizations ensure encryption compliance?
Censinet RiskOps supports healthcare organizations in staying on top of encryption compliance by making it easier to assess, monitor, and manage cybersecurity risks. It ensures that encryption during data transmission meets both regulatory requirements and industry standards, protecting sensitive patient information effectively.
By spotting vulnerabilities and simplifying risk management, Censinet RiskOps enables healthcare organizations to tackle potential threats head-on while adhering to essential compliance standards.
Related Blog Posts
- Best Practices for End-to-End Encryption in Healthcare
- HIPAA Encryption Rules for Data in Transit
- How to Encrypt PHI Data for Secure Transmission
- Encryption in Transit: Compliance for Healthcare IT
{"@context":"https://schema.org","@type":"FAQPage","mainEntity":[{"@type":"Question","name":"Why is TLS 1.3 the best choice for securing healthcare data during transmission?","acceptedAnswer":{"@type":"Answer","text":"<p>TLS 1.3 stands out as the go-to protocol for protecting healthcare data during transmission. It offers <strong>better encryption</strong>, improved speed, and lower latency compared to earlier versions. These upgrades make it a powerful tool for shielding sensitive patient information against today's cyber threats.</p> <p>By simplifying communication and eliminating old security gaps, TLS 1.3 allows healthcare organizations to maintain <strong>safe and reliable data exchanges</strong>. This is essential for protecting patient privacy and staying compliant with regulatory standards.</p>"}},{"@type":"Question","name":"How does end-to-end encryption protect patient data during transmission?","acceptedAnswer":{"@type":"Answer","text":"<p>End-to-end encryption plays a crucial role in protecting patient data during transmission. It works by encrypting the data as soon as it leaves the sender and keeping it encrypted until it reaches the intended recipient. This means that only those with the correct decryption keys can access the information.</p> <p>This approach prevents unauthorized access or interception, ensuring sensitive patient information stays private. It also helps healthcare organizations meet regulatory requirements, safeguarding both patients and the institutions handling their data.</p>"}},{"@type":"Question","name":"How does Censinet RiskOps help healthcare organizations ensure encryption compliance?","acceptedAnswer":{"@type":"Answer","text":"<p>Censinet RiskOps supports healthcare organizations in staying on top of encryption compliance by making it easier to assess, monitor, and manage <a href=\"https://www.censinet.com/blog/5-ways-to-reduce-3rd-party-cybersecurity-risks-per-18-experts\">cybersecurity risks</a>. It ensures that encryption during data transmission meets both regulatory requirements and industry standards, protecting sensitive patient information effectively.</p> <p>By spotting vulnerabilities and simplifying risk management, Censinet RiskOps enables healthcare organizations to tackle potential threats head-on while adhering to essential compliance standards.</p>"}}]}
Key Points:
Why is TLS 1.3 the foundation of encryption in transit for healthcare?
- Stronger, modern cipher suites with forward secrecy
- Elimination of outdated algorithms like RSA key exchange
- Faster handshakes ideal for EHRs and telehealth
- Alignment with HIPAA and NIST guidance
- Enables safe‑harbor status if encrypted data is intercepted
How does end‑to‑end encryption (E2EE) protect transmitted PHI?
- Ensures only endpoints can decrypt data
- Prevents intermediaries—including vendors—from reading plaintext
- Reduces likelihood of reportable HIPAA breaches
- Integrates with secure messaging, portals, and APIs
- Pairs with TLS for layered defense
Why should healthcare organizations require VPN usage?
- Encrypts all remote sessions involving ePHI
- Supports HIPAA‑aligned safeguards for remote work
- Protects credentials from interception and MITM attacks
- Enables secure access to EHRs, billing, imaging, and cloud apps
- Ideal for clinicians, coders, and staff working off‑site
How does AES‑256 secure ePHI during transmission?
- Widely recognized standard for strong encryption
- Used in secure TLS cipher suites like AES‑256‑GCM
- Prevents decryption even with powerful attacks
- Requires strong key management (HSMs, KMS, rotation policies)
- Eliminates risks from deprecated ciphers like 3DES
How does MFA strengthen encrypted sessions?
- Stops credential‑based attacks, even if passwords are stolen
- Required for HIPAA‑aligned modern authentication
- Ideal for VPNs, EHR portals, and cloud apps with ePHI
- Prevents misuse of encrypted channels by unauthorized users
- Supports FIDO2, biometrics, and authenticator apps
Why is continuous monitoring essential for encryption compliance?
- Tracks weak TLS versions, expired certificates, or plaintext traffic
- Flags misconfigurations and missing MFA on encrypted channels
- Provides audit‑ready documentation for HIPAA reviews
- Monitors vendors encryption practices in real time
- Platforms like Censinet RiskOps™ centralize evidence and remediation


