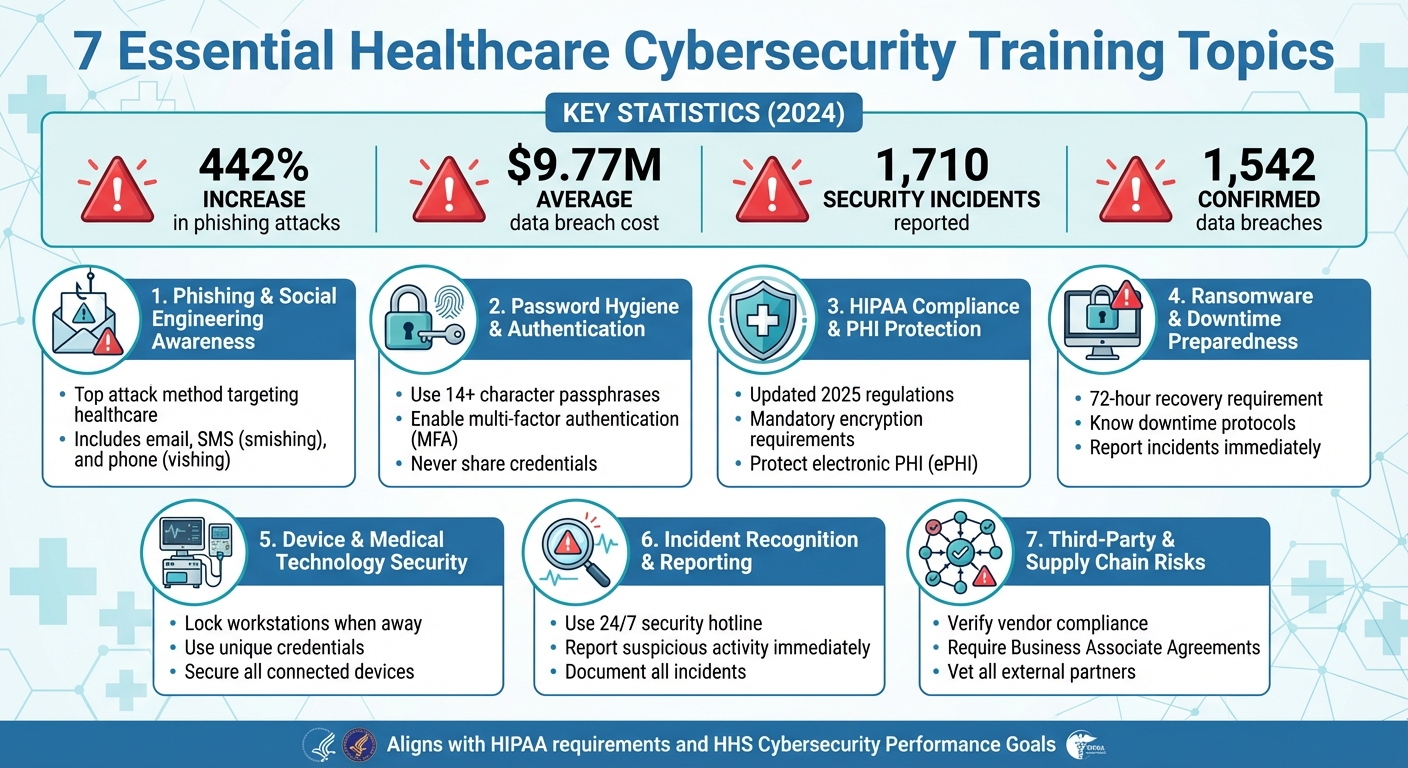
Top 7 Topics for Healthcare Cybersecurity Training
Post Summary
Healthcare organizations face mounting cyber threats, with phishing attacks up 442% in 2024 and the average data breach costing $9.77 million. Cyberattacks disrupt clinical operations, compromise patient safety, and expose sensitive health data. Effective training is essential to mitigate these risks, comply with updated 2025 HIPAA regulations, and safeguard patient care. Here are the 7 key areas every healthcare organization must address in cybersecurity training:
- Phishing Awareness: Spot phishing emails, smishing, and vishing attempts to prevent credential theft and ransomware.
- Password Hygiene: Use strong passphrases, avoid reuse, and implement multi-factor authentication (MFA).
- HIPAA Compliance: Understand updated rules for protecting electronic protected health information (ePHI).
- Ransomware Preparedness: Follow downtime protocols and report incidents promptly to minimize disruptions.
- Device Security: Secure medical devices and workstations to prevent unauthorized access and disruptions.
- Incident Reporting: Recognize and report suspicious activity to stop breaches early.
- Third-Party Risks: Manage vendor relationships and ensure compliance with security standards.
These focus areas align with HIPAA requirements and the HHS Cybersecurity Performance Goals, emphasizing practical steps staff can take to protect systems, data, and patient safety.
Healthcare Cybersecurity Training: 7 Essential Topics and Key Statistics
1. Phishing and Social Engineering Awareness
Relevance to Healthcare-Specific Cybersecurity Threats
Phishing continues to be the top method hackers use to breach healthcare systems, paving the way for ransomware attacks, credential theft, and the theft of protected health information (PHI) [2]. The problem is growing fast - CrowdStrike reported a staggering 442% increase in phishing attacks targeting healthcare between the first and second halves of 2024. This surge is fueled by attackers using advanced tools like AI and deepfakes [6]. Healthcare organizations are particularly at risk because attackers exploit the fast-paced, high-pressure nature of clinical workflows, relationships with vendors, and the urgency tied to patient care. Common tactics include phishing emails that mimic electronic health record (EHR) vendors, insurance portals, or internal IT teams asking for credential verification. Business email compromise (BEC) schemes are also rampant, where scammers pose as executives or physicians to request wire transfers or changes to vendor banking details [2]. Beyond email, attackers use smishing (fake SMS alerts) and vishing (phone calls from impostors pretending to be IT staff or regulators) to trick clinicians into revealing sensitive information [2].
Impact on Protecting Patient Safety and PHI
Phishing attacks don’t just leak data - they can bring critical systems to a standstill, forcing hospitals to rely on manual processes. This shift increases the risk of medication errors, patient misidentification, and delayed diagnoses [2]. When ransomware locks down systems like EHRs, imaging platforms, or lab interfaces, the consequences are severe: surgeries get delayed, ambulances are rerouted, and clinicians lose access to the real-time information they need to make safe treatment decisions [2]. On top of that, the financial toll is massive - the average cost of a healthcare data breach hit $9.77 million per incident in 2024 [6]. Training staff to spot phishing attempts early isn’t just about protecting data; it’s about preserving patient safety and ensuring PHI remains secure.
Alignment with U.S. Regulations Like HIPAA
Under HIPAA, organizations are required to provide security awareness training to prevent, detect, and correct violations. Updated guidance emphasizes the importance of continuous, scenario-based training [1][3][8]. Since phishing and social engineering are leading causes of unauthorized access, effective training directly supports these compliance efforts. The HHS Cybersecurity Performance Goals prioritize defenses against phishing and credential theft, placing them alongside critical actions like patching software vulnerabilities [8]. Healthcare organizations must document that their staff understand how to avoid sharing credentials or PHI with impostors and know how to report suspicious incidents quickly [1][3]. A well-structured phishing awareness program not only helps meet these regulatory requirements but also demonstrates that reasonable safeguards were in place during OCR investigations or audits after a breach.
Practicality for Day-to-Day Clinical and Administrative Workflows
For training to be effective, it has to fit into the busy workflows of clinical and administrative staff. Employees need to learn how to spot red flags like display name spoofing, mismatched email addresses, misspelled vendor names, unfamiliar file types, and urgent language - especially in messages related to payroll or benefits [2]. Training should reinforce that IT will never ask for passwords via email, text, or phone. Any request to share PHI, change banking details, or provide credentials should always be verified through a second, trusted channel, such as calling an internal extension or using the vendor’s official phone number [2].
To make training stick, organizations can embed phishing tips directly into tools staff use daily, like EHR login screens, intranets, or scheduling systems. Pop-up reminders before sending emails containing PHI can also be helpful [7]. Simulated phishing campaigns are another effective tool, as they provide immediate feedback and help staff recognize patterns. These simulations should be timed carefully - avoiding shift changes or high-demand periods - to minimize disruptions [3]. Platforms like Censinet RiskOps™ take this a step further by identifying how phishing and social engineering risks extend to vendors, clinical applications, and supply chain partners, ensuring a broader layer of protection.
2. Password Hygiene and Authentication Practices
Relevance to Healthcare-Specific Cybersecurity Threats
Phishing often sets the stage for breaches, but compromised credentials escalate the danger significantly. Weak or stolen passwords remain one of the most common ways attackers infiltrate healthcare systems, with many breaches starting from this vulnerability [2]. The U.S. healthcare sector is particularly enticing to attackers, as they can profit from stolen PHI and operational disruptions. Breach costs in this sector far exceed those in other industries [6]. Weak or reused passwords on systems like EHRs, patient portals, radiology platforms, or vendor accounts not only expose sensitive data but can also disrupt life-critical operations. Imagine surgeries being delayed, ambulances rerouted, or medication orders inaccessible - all due to compromised credentials [2]. Recognizing this, the HHS Cybersecurity Performance Goals emphasize protecting against stolen credentials, ranking this threat alongside phishing as a top priority for hospitals and their partners [8]. This ongoing risk highlights the urgent need for stronger authentication practices.
Practicality for Day-to-Day Clinical and Administrative Workflows
Healthcare professionals juggle access to multiple systems during a single shift - EHRs, PACS, pharmacy platforms, lab systems, telehealth, and scheduling tools. This constant switching often leads to password reuse, short passwords, or even shared credentials, which weaken security [3]. Shared workstations, like those at nursing stations or registration desks, are frequently left logged in under one user to save time. While convenient, this practice creates accountability gaps and opens the door for unauthorized access to PHI by insiders or even visitors. Remote work introduces additional risks, particularly when staff use personal devices without secure VPNs or multifactor authentication (MFA) [2].
To address these challenges, training should encourage long, unique passphrases - 14 characters or more, using multiple words. These are easier to remember and much harder to crack [3]. Enterprise password managers can help staff securely generate and store complex passwords for non-EHR accounts, such as payer portals or vendor dashboards, reducing reliance on insecure methods like sticky notes. To streamline workflows, IT teams can implement single sign-on (SSO) and fast re-authentication methods, such as badge taps or biometrics, for shared workstations. This minimizes the need to repeatedly enter passwords during busy shifts. Real-world scenarios - like handling an unlocked workstation in a patient room or responding to a suspicious password request - should be part of training to reinforce secure behaviors [2][7].
Alignment with U.S. Regulations Like HIPAA
HIPAA mandates secure authentication and unique user IDs for accessing ePHI, with MFA required for systems handling sensitive data [1][3]. The HHS Cybersecurity Performance Goals also emphasize strong access controls and continuous monitoring to guard against stolen credentials and phishing [8][9]. Training should draw clear connections between everyday actions - like avoiding password sharing, logging out of shared workstations, and reporting lost badges - and these legal and industry standards. Framing these practices as both regulatory requirements and practical measures to protect patients and the organization can drive compliance [1][3][8].
MFA is essential for remote access to VPNs, telehealth platforms, cloud-based EHRs, and privileged accounts like domain administrators or database managers. Healthcare organizations should prioritize low-friction MFA options, such as push notifications, hardware security keys for high-risk users, or badge-plus-PIN setups for quick workstation access. SMS-based MFA should generally be avoided due to its security weaknesses. Training should also prepare staff to recognize and report "MFA fatigue" attacks, where attackers exploit repeated push notifications to trick users into approving unauthorized access [6][8].
Impact on Protecting Patient Safety and PHI
Credential compromises can lock clinicians out of EHRs and critical systems, forcing a switch to paper backups that delay care and increase the risk of errors [2]. Ransomware attacks often begin with stolen or phished credentials, leading to encrypted systems, canceled procedures, delayed lab results, and even ambulance diversions. These incidents have been described as a growing crisis in healthcare cybersecurity [2][6]. Beyond operational disruptions, compromised passwords can expose vast amounts of PHI, resulting in identity theft, fraud, and long-term damage to patient trust. Training can use anonymized case examples - like a shared workstation being exploited to alter medication orders or access celebrity health records - to underscore the connection between secure authentication, patient privacy, and clinical safety [2][6].
To ease password management while enhancing security, healthcare organizations can adopt SSO integrated with EHRs and other major systems. This allows clinicians to log in once per shift and use badge taps or biometrics for quick re-authentication on shared workstations. Advanced identity and access management (IAM) tools can automate role-based access, ensuring that new hires, role changes, and terminations are promptly reflected in system privileges. This reduces the risk of stale or orphaned accounts being misused [3][5]. Tools like Censinet RiskOps™, designed for healthcare cybersecurity, can evaluate third-party applications for their authentication features - such as MFA support and password storage methods - while benchmarking an organization’s controls against peers. By addressing password practices as part of a broader cybersecurity strategy, healthcare organizations can strengthen defenses across incident response, device security, and vendor risk management.
3. HIPAA Compliance and PHI Protection
Relevance to Healthcare-Specific Cybersecurity Threats
HIPAA establishes baseline standards to safeguard protected health information (PHI) and electronic PHI (ePHI) from breaches, unauthorized access, and misuse [3]. The healthcare industry is a prime target for cyberattacks because PHI has high monetary value on the black market, and operational disruptions in care settings can be exploited for financial gain [2][3]. Reports of breaches are alarmingly frequent, highlighting the ongoing exposure of sensitive patient data [2]. Proper training on HIPAA equips employees with the knowledge to recognize how cyber threats like phishing, ransomware, and unauthorized access can lead to violations, potentially resulting in civil penalties, regulatory scrutiny, and damage to the organization’s reputation [2][3]. Healthcare breaches are among the most expensive, often costing millions due to fines, recovery efforts, and the erosion of patient trust [6]. These realities directly affect clinical and administrative operations every day.
Practicality for Day-to-Day Clinical and Administrative Workflows
HIPAA violations often stem from everyday actions, such as leaving electronic health record (EHR) sessions open, improperly discarding printed PHI, discussing patient information in public spaces, using personal email to send PHI, or relying on unapproved communication tools [2][3]. Training programs should incorporate real-life examples from U.S. hospitals, like a case where forwarding a patient spreadsheet to a personal email account led to a reportable breach involving thousands of records and triggered an investigation by the Office for Civil Rights. By pairing each risk with straightforward alternatives - such as using secure remote access portals instead of personal email or HIPAA-compliant messaging platforms instead of SMS - staff can adopt safer practices without feeling hindered in their work [2][3].
For secure communication, employees must use approved, encrypted email services and avoid sending PHI through personal accounts [1]. HIPAA-compliant messaging platforms with built-in security features, such as audit logs and access controls, should replace consumer-grade texting apps. Remote access should always go through secure VPNs or zero-trust tools with multi-factor authentication (MFA), and staff should refrain from downloading PHI onto personal devices [1][3]. Short, scenario-based exercises - like “Can I text a lab result to a referring physician?” or “What steps should I take if PHI is sent to the wrong recipient?” - can help turn abstract rules into practical, repeatable actions [1][3].
Alignment with U.S. Regulations Like HIPAA
The 2025 updates to the HIPAA Security Rule eliminate the distinction between "addressable" and "required" safeguards, effectively making most technical and administrative controls mandatory. This raises the stakes for workforce training and accountability [1]. These updates emphasize stronger measures, including encryption, MFA, network segmentation, regular audits, and incident response planning [1]. Training should clearly connect these legal requirements with everyday actions, such as always using encrypted messaging, adhering to VPN policies for remote access, and immediately reporting any suspected PHI exposure [1][3].
The HHS Cybersecurity Performance Goals further advocate for practices like timely software patching, phishing defenses, and robust authentication methods - all of which support HIPAA compliance and PHI security. Staff training plays a critical role in implementing these measures [8].
Additionally, risks associated with third-party vendors must be addressed through strict adherence to approved business associate agreements [3]. Employees should be trained to verify vendors’ authorization, understand permissible PHI-sharing practices, and avoid uploading PHI to unapproved tools. Platforms like Censinet RiskOps™ can help healthcare organizations continuously monitor vendor compliance by evaluating their controls over PHI, medical devices, and supply chains [4]. Incorporating these practices into daily routines not only meets regulatory requirements but also strengthens patient care.
Impact on Protecting Patient Safety and PHI
Strong HIPAA compliance minimizes the risk of cyber incidents that can disrupt care, delay treatment, or compromise clinical decision-making [2][5]. For example, ransomware attacks or system intrusions that lock EHRs or imaging systems can prevent clinicians from accessing critical information like medication histories, allergies, or lab results. This forces care teams to make decisions without complete data, delay procedures, or divert patients altogether [2][5]. By enforcing access controls, encryption, and robust incident response plans as mandated by HIPAA, healthcare organizations can better preserve the availability and integrity of PHI and clinical systems during and after cyberattacks [1][3].
Training programs should emphasize that HIPAA is not just about privacy - it’s a safeguard for patient safety. For instance, properly encrypted and backed-up EHRs can be restored within hours after an attack, allowing clinicians to continue providing care without major disruptions. Framing compliance as a critical part of patient care, rather than as an administrative burden, helps healthcare professionals see its importance in fulfilling their duty of care [1][2].
4. Ransomware and Downtime Preparedness
Relevance to Healthcare-Specific Cybersecurity Threats
Ransomware poses a serious risk to hospitals and clinics across the U.S. Unlike other industries where attacks might result in financial setbacks or data leaks, ransomware in healthcare can cripple essential systems like EHR platforms, imaging tools, pharmacy applications, and scheduling systems, effectively shutting down clinical operations [2]. When these systems go offline, the consequences are immediate and far-reaching: surgeries are delayed, medication errors become more likely, diagnostic workflows grind to a halt, and emergency departments may have to send ambulances elsewhere [2][5]. Training programs should emphasize that ransomware directly threatens patient safety and operational stability, making it a concern for every employee. To address this, organizations need clear, actionable response protocols that leave no room for confusion.
Practicality for Day-to-Day Clinical and Administrative Workflows
Ransomware preparedness training should focus on practical, role-specific downtime procedures that staff can implement the moment systems fail. For instance, nurses must know how to document vital signs and administer medications using paper records when EHR systems are inaccessible. Registration staff need clear steps for manually verifying insurance and registering patients. Physicians must have protocols for ordering labs, imaging, and medications without relying on electronic systems [2]. Training should also teach employees to spot early warning signs - such as strange pop-ups, files becoming inaccessible, or mass file renaming - and stress the importance of reporting these issues immediately rather than attempting to fix them independently [2].
Scenario-based drills can be invaluable in preparing staff for EHR downtime. These exercises reinforce critical procedures and ensure everyone knows what to do in the first moments of an attack. To support this, organizations should provide simple visual aids, like runbooks or pocket cards, at key locations such as nursing stations and registration desks. These tools can outline the initial 15 minutes of response, including who to contact, which systems to disconnect, and where to access manual workflow tools [2][5].
Alignment with U.S. Regulations Like HIPAA
Under the HIPAA Security Rule, healthcare organizations are required to have security incident procedures and contingency plans in place, including robust data backup, disaster recovery, and emergency mode operation plans [1][3]. By 2025, updated guidance will require critical operations to be restored within specific timeframes - often within 72 hours following a cyberattack. This makes having well-tested ransomware response and downtime plans a necessity, not a luxury [1].
Training programs play a key role in meeting these regulatory requirements by ensuring staff understand their responsibilities under the organization’s incident reporting and contingency plans. Highlighting real-world enforcement actions and breach settlements tied to insufficient planning can drive home the point that ransomware preparedness isn’t optional - it’s a legal obligation [1][3]. Additionally, the HHS Cybersecurity Performance Goals emphasize practices like regular testing of backups, network segmentation, and incident response planning as essential safeguards [8]. These regulations make it clear that ransomware preparedness is about more than compliance - it’s a critical part of protecting patient safety.
Impact on Protecting Patient Safety and PHI
Clear response protocols are essential for safeguarding both patient safety and protected health information (PHI). When ransomware locks EHR systems and other clinical tools, healthcare providers are forced to make decisions without access to vital patient information, such as medication histories, allergy records, lab results, and imaging reports [2][5]. This lack of data significantly increases the likelihood of diagnostic errors, treatment delays, and adverse events.
Modern ransomware attacks often exfiltrate data before encrypting systems, which means even if operations are restored from backups, organizations may still face data breach obligations. This can expose patients to identity theft and other risks [2][3]. By training staff to recognize suspicious activity early, follow detailed downtime procedures, and execute recovery workflows, healthcare organizations can minimize disruptions, maintain continuity of care, and reduce the risk of PHI exposure. Framing these cybersecurity measures as critical to patient safety helps healthcare workers see how their actions directly contribute to protecting their patients [1][2][5].
sbb-itb-535baee
5. Secure Use of Devices and Medical Technology
Relevance to Healthcare-Specific Cybersecurity Threats
As healthcare systems grow increasingly interconnected, securing medical devices has become a critical aspect of cybersecurity. In the U.S., these devices and clinical technologies are major targets for cyberattacks. When compromised, they don't just expose sensitive data - they can directly endanger patients. Devices like networked infusion pumps, imaging systems, patient monitors, and electronic health record (EHR) workstations are all connected to clinical networks, creating multiple entry points for attackers. Many of these devices still operate on outdated or unsupported systems, making them especially vulnerable to ransomware and malware. Hackers could manipulate dosages, disable alarms, delay diagnostics, or even shut down entire care units. The 2025 Verizon Data Breach Investigations Report revealed 1,710 security incidents in healthcare, with 1,542 confirmed data breaches [2]. This highlights the urgent need for focused training on securing these devices.
Practicality for Day-to-Day Clinical and Administrative Workflows
For cybersecurity measures to be effective, they must align with the fast-paced nature of healthcare environments. Staff should always lock or log off workstations, shared terminals, and mobile carts when stepping away. Using unique credentials ensures accountability and creates accurate audit trails. Clinicians and staff must avoid storing patient information on local drives, taking unauthorized screenshots, or using personal messaging apps to share sensitive data. All protected health information (PHI) should stay within approved, encrypted systems. When using telehealth platforms or working remotely, employees must rely on secure, approved platforms and VPNs rather than public Wi-Fi networks. Lost or stolen devices should be reported immediately so IT teams can respond by disabling or remotely wiping them. Providing staff with pocket cards that outline secure login, logout, and reporting procedures helps reinforce these habits.
Alignment with U.S. Regulations Like HIPAA
The HIPAA Security Rule requires healthcare organizations to implement administrative, physical, and technical safeguards to protect electronic PHI across all devices. These measures include using unique user IDs, enabling automatic logoff on shared workstations, and encrypting data both at rest and in transit. Simple oversights - like failing to lock a workstation or using personal apps for PHI - can lead to HIPAA violations. Additionally, the HHS Cybersecurity Performance Goals emphasize addressing known vulnerabilities and preventing credential theft. Following secure device protocols not only ensures compliance but also reduces the risk of costly breaches. In 2024, the average cost of recovering from a healthcare data breach reached $9.77 million per incident [6].
Impact on Protecting Patient Safety and PHI
Incorporating secure device practices into daily routines is crucial for maintaining patient safety and uninterrupted care. Insecure device use can have immediate and severe consequences. For instance, ransomware or malware attacks could render critical systems like EHRs, imaging platforms, or pharmacy applications inaccessible. Without access to essential patient data - such as medication histories, allergy records, or lab results - clinicians are more likely to encounter diagnostic errors, treatment delays, or adverse events. Worse yet, compromised devices could be manipulated to deliver incorrect dosages or alter settings, directly endangering patients. Beyond these immediate risks, breaches that expose PHI can damage patient trust, potentially discouraging individuals from seeking care when they need it most.
Training staff to recognize unusual device behavior - such as unexpected reboots, error messages, or performance issues - and respond swiftly is key to stopping attacks before they escalate. Tools like Censinet RiskOps™ can help organizations assess and manage risks associated with medical devices, clinical applications, and vendor access, integrating these efforts into a broader risk management framework.
As Matt Christensen, Sr. Director GRC at Intermountain Health, explains, "Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare" [10].
Secure device use goes beyond meeting compliance requirements - it ensures that every piece of technology in a healthcare setting supports safe and uninterrupted patient care.
6. Incident Recognition and Reporting Protocols
Relevance to Healthcare-Specific Cybersecurity Threats
The 2025 Verizon Data Breach Investigations Report recorded 1,710 security incidents and 1,542 confirmed data breaches within the healthcare sector [2]. Unlike other industries, a cyberattack in healthcare can have an immediate and direct impact on patient care. Systems like electronic health records (EHRs), e-prescribing tools, and connected medical devices are critical to daily operations, and any disruption can compromise clinical workflows. Recognizing early warning signs - such as unusual login prompts, unexpected EHR timeouts, or erratic device behavior - and reporting them promptly enables security teams to act before these issues spiral into ransomware attacks or large-scale breaches of protected health information (PHI). The high stakes of healthcare cybersecurity make swift recognition and well-integrated reporting systems essential.
Practicality for Day-to-Day Clinical and Administrative Workflows
To ensure timely reporting, staff should use established channels like a 24/7 security hotline, an incident-reporting portal, or EHR-integrated shortcuts [1][2]. These tools are designed to seamlessly fit into everyday workflows, building on prior training to encourage immediate action. Training programs should include role-specific scenarios that reflect real-world challenges. For example, a nurse might notice a locked medication administration system, billing staff could detect suspicious changes in invoices, or a lab technician might observe unusual behavior in imaging systems. Stressing the importance of reporting even minor anomalies helps prevent them from escalating into larger breaches.
At Tower Health, the adoption of Censinet RiskOps™ highlights how purpose-built platforms can streamline incident management. This system allowed three full-time employees to refocus on their primary roles while maintaining robust risk assessments with just two dedicated staff members [10]. Such solutions demonstrate that effective incident protocols can enhance security without disrupting daily operations.
Alignment with U.S. Regulations Like HIPAA
The updated 2025 HIPAA Security expectations emphasize the need for rapid incident response, requiring critical operations to be restored within 72 hours [1]. Early recognition and reporting are not just recommended practices - they are regulatory requirements. A HIPAA-compliant reporting process should define what constitutes a "security incident" or "breach", establish clear internal reporting channels, and ensure detailed documentation of incidents. This includes noting who reported the issue, when it was reported, which systems or PHI were affected, and what containment measures were taken [1][3].
Training must reinforce that timely reporting is mandatory and that organizations are subject to audits of their incident response capabilities. Employees should also feel confident that good-faith reporting is supported and protected. This fosters a culture where anomalies are addressed immediately, reducing the risk of widespread breaches and regulatory penalties [3][5]. Regulatory compliance directly ties rapid incident reporting to the protection of patient care and data security.
Impact on Protecting Patient Safety and PHI
Quick recognition and reporting can stop a small issue from escalating into a full-blown crisis. Prompt action allows security teams to isolate affected systems, minimizing disruptions to operations and limiting PHI exposure [2][3][5]. In severe cases, ransomware attacks can force hospitals to divert ambulances, cancel surgeries, and revert to paper-based processes - transforming a cybersecurity event into a direct threat to patient safety [2]. By training staff to view anomalies - such as missing orders, malfunctioning devices, or inaccessible records - as potential security incidents rather than simple IT glitches, organizations can maintain continuity of care. This also ensures that downtime procedures are executed safely when systems need to be taken offline [2][5].
7. Third-Party and Supply Chain Risk Awareness
Relevance to Healthcare-Specific Cybersecurity Threats
Healthcare organizations depend on a wide network of external partners - EHR vendors, cloud hosting providers, billing services, transcription companies, telehealth platforms, and medical device manufacturers. These partners often handle or access PHI, making them potential entry points for cyberattacks. Recent reports reveal that many breaches stem from compromised third-party relationships rather than direct attacks on hospitals [2]. Attackers frequently target vendors with weaker security, using compromised remote access tools or stolen credentials to infiltrate hospital networks. A single breach at one vendor can expose PHI across multiple organizations [2][8]. This interconnected system highlights the need for strict protocols, which are outlined below.
Practicality for Day-to-Day Clinical and Administrative Workflows
Managing third-party and supply chain risks is just as important as securing internal operations. Staff training should focus on straightforward, role-specific practices that can be applied immediately. For example, clinicians should understand that introducing new apps, telehealth tools, or device integrations without IT approval can introduce unvetted risks into clinical workflows. Administrative teams must ensure that vendors handling PHI have completed security reviews and signed a Business Associate Agreement (BAA) before any data is shared [3]. Additionally, front-line staff should be trained to verify vendor identities before enabling remote support sessions, avoid sharing credentials with vendor personnel, and report unusual requests, such as unexpected data exports or the use of unsupported file-sharing platforms. Tools like Censinet RiskOps™ simplify this process by maintaining approved vendor lists and centralizing risk data, allowing staff to easily follow clear guidelines on safe vendor usage and data-sharing practices [10].
Alignment with U.S. Regulations Like HIPAA
Given the risks associated with third-party relationships, regulatory frameworks like HIPAA require vigilant vendor management. HIPAA mandates that covered entities ensure their business associates implement proper safeguards for PHI. This is documented through BAAs, which outline permitted uses, security measures, and breach notification responsibilities [3]. Training should emphasize that staff cannot assume a vendor is compliant simply because they offer a service. Vendors must be formally vetted and contracted before any PHI is shared. Updated HHS Cybersecurity Performance Goals specifically address security for "health care and related third parties", acknowledging that attackers often exploit vendor relationships [8]. Sharing PHI with unapproved vendors, even with the best intentions, can lead to HIPAA violations, regulatory investigations, and financial penalties [3].
Impact on Protecting Patient Safety and PHI
Third-party breaches can have serious consequences for clinical operations, such as delaying access to critical patient records. If an EHR hosting provider, imaging platform, or medical device service is compromised, hospitals may be forced to divert patients and rely on manual processes. This not only endangers patient safety but also undermines trust [2][5]. The financial toll is significant, with the average cost of a healthcare breach reaching approximately $9.77 million per incident in 2024. Vendor-related breaches also drain clinical and administrative resources that should be focused on patient care [6]. Training staff to recognize how vendor security directly impacts operational continuity and patient trust fosters a culture where managing third-party risks is seen as essential to delivering safe, reliable care.
Conclusion
Phishing, weak authentication, HIPAA noncompliance, ransomware, insecure devices, poor incident reporting, and third-party risks are the main avenues attackers exploit to target hospitals, clinics, and health systems. Addressing these seven areas through training helps close critical security gaps [2][3]. When every team member - from clinicians to administrative staff - understands the daily security practices needed to protect PHI and maintain system availability, organizations foster a cybersecurity culture that prioritizes patient safety over mere compliance [1][2].
Regular, scenario-based training is crucial to keeping up with evolving threats like AI-driven phishing campaigns, new ransomware strains, and vulnerabilities in medical devices. With 1,710 healthcare security incidents reported and phishing attacks surging by 442% in 2024, consistent education ensures staff can identify and respond to emerging risks [2][6]. Organizations that invest in ongoing training see tangible benefits, such as fewer phishing incidents, quicker incident reporting, and more effective recovery during system downtimes [2][3].
As cyber threats grow more sophisticated, compliance efforts must also advance to protect patient data. HIPAA mandates that covered entities provide security awareness and training for all workforce members as part of their administrative safeguards [1][3]. The 2025 HIPAA updates have made many technical and administrative controls mandatory, emphasizing the need for documented workforce education on access control, transmission security, and incident response [1]. Aligning training with HHS Cybersecurity Performance Goals ensures that staff behaviors meet regulatory standards and can be demonstrated during audits and risk assessments [1][8].
With the average healthcare data breach costing $9.77 million in 2024, investing in continuous training safeguards both financial stability and uninterrupted patient care [6]. Platforms like Censinet RiskOps™ enable organizations to turn risk assessment insights into targeted training modules, addressing areas where human behavior significantly impacts risks - such as patient data, clinical applications, medical devices, and supply chain security [4][3].
As Matt Christensen, Sr. Director GRC at Intermountain Health, explains: "Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare" [10].
FAQs
How can healthcare organizations protect against phishing attacks?
To guard against phishing attacks, healthcare organizations should prioritize security awareness training. Educating staff on how to identify suspicious emails and refrain from clicking on harmful links is a crucial first step. Incorporating simulated phishing exercises can further strengthen these skills by providing hands-on practice in spotting potential threats.
On the technical side, deploying robust email filtering tools can help block spam and phishing attempts before they reach employees' inboxes. Encouraging a mindset of vigilance within the organization is equally important, ensuring everyone stays alert to potential risks. Advanced solutions, such as AI-driven platforms, can also play a key role in monitoring and managing cybersecurity threats across the entire organization.
What steps can healthcare organizations take to ensure HIPAA compliance in cybersecurity training?
Healthcare organizations can maintain HIPAA compliance in their cybersecurity training by designing customized programs that highlight critical areas. These should include safeguarding Protected Health Information (PHI), recognizing phishing scams, and effectively responding to security breaches. Regular updates to training materials are essential to keep up with new threats and changes in regulations.
To strengthen compliance efforts, it’s important to run periodic testing and audits to evaluate how well the training is working. Using specialized risk management tools can further assist in monitoring compliance risks and simplifying the processes needed to protect sensitive patient information.
How do third-party vendors contribute to cybersecurity risks in healthcare?
Third-party vendors play a crucial role in healthcare, but they can also introduce cybersecurity risks. If a vendor's security protocols aren't strong enough, they might serve as a gateway for cyberattacks, potentially compromising sensitive patient data and disrupting essential systems.
Healthcare providers often depend on these vendors for services such as medical devices, clinical software, and supply chain operations. However, this dependency expands the potential points of attack. To safeguard patient information and ensure compliance with regulations like HIPAA, it's critical for healthcare organizations to actively evaluate and manage the risks associated with their vendors.


