10 Critical TPRM Mistakes That Could Cost Your Healthcare Organization Millions
Post Summary
Healthcare organizations rely on third-party vendors for critical operations, but poorly managed Third-Party Risk Management (TPRM) can lead to breaches, financial losses, and disrupted patient care. Here's a quick summary of the most common TPRM mistakes and how to avoid them:
- One-Time Vendor Checks: Risks evolve; annual reviews leave gaps. Use continuous monitoring.
- Poor Vendor Prioritization: Focus on high-risk vendors handling sensitive data.
- Generic Questionnaires: Tailor assessments to healthcare-specific risks like HIPAA compliance.
- Siloed Processes: Integrate risk management into procurement and contracting.
- Ignoring Subcontractors: Evaluate fourth-party risks and cloud dependencies.
- No Financial Quantification: Assign dollar values to risks for better decision-making.
- Overlooking Medical Devices: Include connected devices in risk assessments.
- Inconsistent Documentation: Standardize and track all risk decisions.
- Manual Workflows: Automate processes to handle large vendor networks efficiently.
- Neglecting AI Risks: Evaluate AI-powered vendor solutions for data security and bias.
Modernizing TPRM with automated tools like Censinet RiskOps™ can centralize vendor risk management, reduce inefficiencies, and safeguard patient safety and finances. These strategies help healthcare organizations address today’s complex risk landscape effectively.
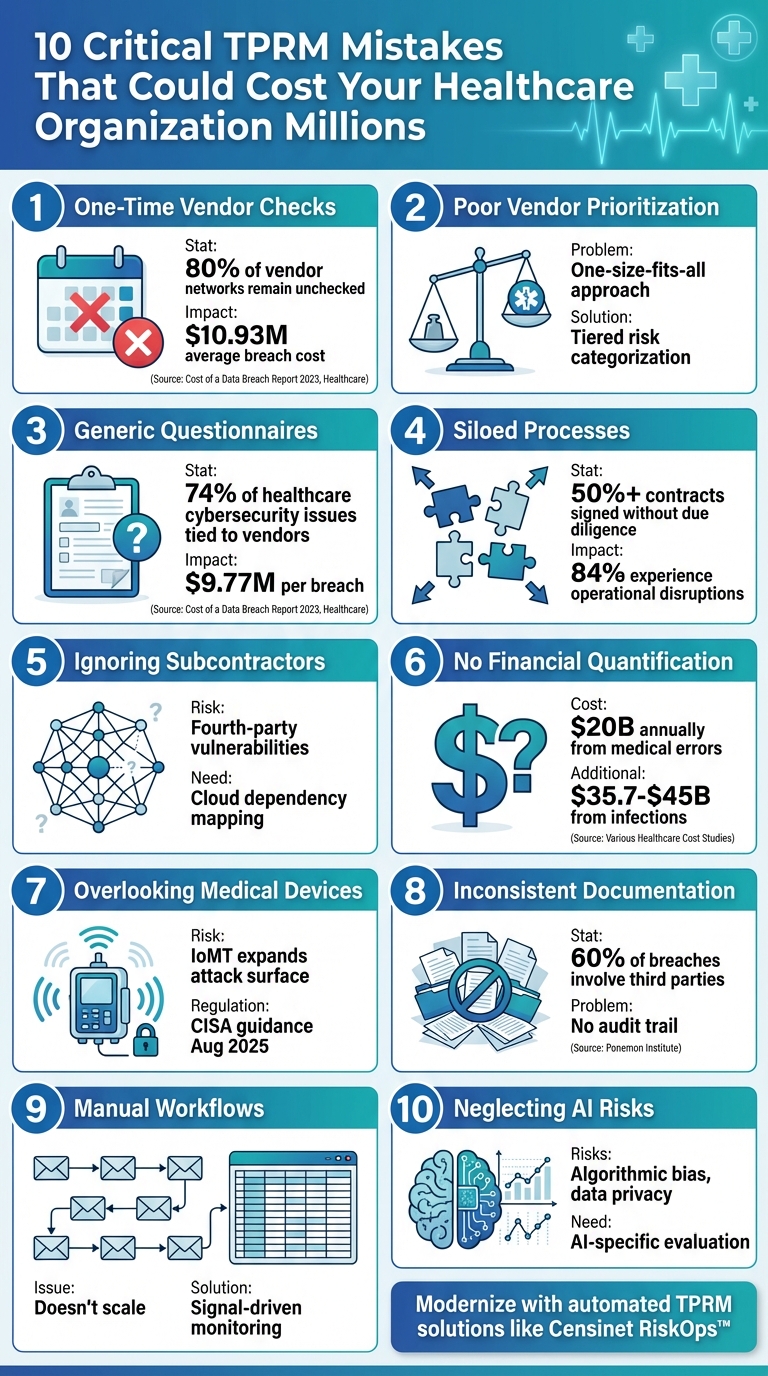
10 Critical TPRM Mistakes Healthcare Organizations Must Avoid
1. Treating TPRM as a One-Time Vendor Check
In the healthcare world, many organizations make the mistake of assessing their vendors just once during onboarding. This "set it and forget it" approach leaves them exposed to risks for years. Vendor security postures can shift 3–4 times a year due to emerging vulnerabilities, stolen credentials, or leadership changes [3]. Yet, with manual processes, most health systems can only review 40 to 60 vendors annually, meaning 80% of their vendor network remains unchecked - a big problem when managing 300+ vendors [3].
"Annual assessments capture last quarter's posture, not today's reality. The 8 to 11 month gap between reviews is where your risk lives." - Atlas Systems [3]
The risks of this oversight are massive. Take Change Healthcare's February 2024 ransomware attack, for example. A missed vulnerability led to the exposure of 192.7 million patient records. Similarly, Concentra Health Services suffered a breach that went unnoticed for nine months - all because their assessments were done annually [3].
The financial toll is just as alarming. Healthcare data breaches now average $10.93 million, making them the most expensive across industries [5]. Third-party vendors play a role in nearly 60% of these breaches, and over half of healthcare organizations - 55% - reported a third-party breach in the past year [4][5].
What’s the solution? Signal-driven monitoring. This approach triggers action when key changes occur, like expiring evidence, security incidents, or shifts in vendor ownership [2]. Automated alerts can assign tasks with owners and deadlines, ensuring issues are promptly addressed [3]. For high-risk vendors, supplement annual reviews with quarterly assessments and continuous monitoring to stay ahead of threats [7].
Next, we’ll explore how failing to prioritize vendor risks can lead to even greater vulnerabilities.
2. Ignoring Criticality and Inherent Risk in Vendor Prioritization
Not all vendors carry the same level of risk, yet many healthcare organizations treat them as if they do. This "one-size-fits-all" mindset drains resources on low-risk vendors while leaving high-risk partnerships - like those with access to Protected Health Information (PHI) or critical clinical systems - without enough scrutiny [2]. This mismanagement sets the stage for further third-party risk management (TPRM) issues.
The root of the problem lies in how inherent risk is assessed. Inherent risk reflects whether a vendor has access to sensitive, non-public personal information [11]. Using generic questionnaires for all vendors leads to wasted time on low-risk providers, while high-risk ones often slip through the cracks [2].
To prioritize vendors effectively, organizations need to evaluate two key factors: business impact (criticality) and inherent risk. Criticality focuses on how a vendor's failure could disrupt operations, harm patient care, or delay recovery beyond a single business day [8][10]. Inherent risk, on the other hand, examines elements like access to PHI, adherence to HIPAA, cybersecurity measures, operational reliability, and business continuity plans [9].
A tiered categorization system is the solution. Vendors handling PHI or supporting patient care should be classified as critical and high-risk, requiring annual reassessments. Moderate-risk vendors may need reviews every 18 to 24 months, while low-risk vendors can be assessed every three years or at contract renewal [12]. This structured approach ensures resources are directed where they’re needed most, rather than treating a payroll vendor the same as an electronic health record system provider. By implementing this tiered system, organizations lay the groundwork for addressing more specific assessment challenges down the line.
"A High risk rating is not a bad thing – some people feel like if a company is deemed to be a high risk overall, perhaps we shouldn't be doing business with them. And that's not the case at all! In fact, you would reasonably expect a company that has extensive access to your customers' data to be a high risk – think of your core processor or your outsourced call center… I've literally had hundreds of discussions with managers on why High risk ratings does not, at all, mean it's a bad thing." - Stephanie DellaCamera, Client Support Operations Manager, Venminder [8]
3. Using Generic Questionnaires Not Tailored to Healthcare
Generic security questionnaires create a major blind spot for healthcare organizations. While standard IT security questions might work for industries like retail or finance, they fall short when it comes to the unique challenges of healthcare - especially in areas like HIPAA compliance, medical device security, and protecting clinical data. For example, the Verizon Cybersecurity Report highlighted that in 2023, 74% of healthcare cybersecurity issues were tied to third-party vendors[15]. Overlooking these specific risks can lead to severe operational and financial fallout.
The numbers tell a grim story. In 2024, healthcare made up 41.2% of all third-party breaches[6]. Even worse, the average cost of a breach in this sector hit $9.77 million per incident[4], more than double the cross-industry average of $4.88 million. These costly breaches often happen because vendors pass generic security reviews that fail to address the rigorous data protection standards required in healthcare.
Adding to the problem is the sheer volume of vendors many organizations need to manage. With hundreds or even thousands of vendors, audit fatigue becomes a real issue. This overload can lead to rushed or incomplete evaluations, leaving critical vulnerabilities unaddressed[13]. Without healthcare-specific questions and documented evidence, organizations face challenges proving their risk management decisions during audits or regulatory reviews[2].
The urgency for tailored assessments is underscored by the upcoming HIPAA Security Rule update, set to take effect in January 2025. This update demands that third parties implement stricter security measures, enforce clear contractual obligations, engage in continuous monitoring, and promptly report incidents involving PHI[4]. Generic assessments often miss vital concerns, such as network segmentation for medical devices or patient-centered risk evaluations[14].
"One of the greatest challenges in TPRM is protecting data even as companies adopt new systems and approaches." – Haibei Wang, CTO, Audiboard[16]
To address these challenges, healthcare organizations need to rethink their approach to vendor assessments. Focus on HIPAA compliance, ensure PHI encryption, and rely on validated assurances from qualified assessors instead of self-attested questionnaires. These steps can help target vulnerabilities that could otherwise lead to multimillion-dollar risks.
4. Failing to Link TPRM to Contracting and Procurement
When risk assessment teams and procurement departments work independently, it opens the door for high-risk vendors to bypass proper scrutiny. The numbers are concerning: over 50% of vendor contracts are signed without conducting adequate pre-contract due diligence to uncover potential risks[21]. This lack of coordination often means vendors can access sensitive patient data before security teams have a chance to evaluate their risk profiles. The result? Operational and legal challenges that could have been avoided.
The impact of these silos is staggering. 84% of businesses have experienced operational disruptions due to overlooked third-party risks, and 33% have faced regulatory action stemming from issues in their third-party risk management (TPRM) programs[20]. Without collaboration, critical security measures - such as breach notification clauses, data handling requirements, and business associate agreements (BAAs) - are frequently left out of contracts, leaving organizations vulnerable[18][19][7]. Shockingly, only 14% of procurement professionals use continuous monitoring tools to evaluate suppliers, even though 41% of organizations consider it a vital TPRM strategy[16].
As ZenGRC aptly points out:
"Manual vendor management creates critical vulnerabilities through fragmented documentation and inconsistent security assessments."[7]
The problem is compounded by data silos, which 86% of professionals believe harm risk management efforts[16]. Security teams often find themselves reacting to risks after the fact - scrambling to assess vendors who are already handling protected health information (PHI). By then, it’s too late to negotiate safeguards like cybersecurity responsibilities, service-level agreements, or proper data handling terms.
To address these challenges, healthcare organizations need to integrate risk management into the contracting process from the start. Standardizing vendor assessments based on their risk levels and the type of PHI they access ensures that evaluations occur before contracts are signed[7][19]. When procurement and security teams collaborate early, they can build contracts that include essential protections - such as obligations for vendors to manage risks and clear exit strategies for data destruction or return if the relationship ends[22]. This proactive approach not only strengthens security but also reduces the likelihood of costly disruptions.
5. Underestimating Fourth-Party and Cloud Dependencies
Relying solely on your primary vendor's security measures might seem sufficient, but it often leaves a significant gap: their subcontractors. These so-called fourth-party risks - arising from your vendors’ subcontractors, cloud providers, and other partners - can bring unforeseen vulnerabilities. Many healthcare organizations fail to account for this extended network, focusing only on the risks posed by direct vendors. However, ignoring these hidden dependencies can leave patient data exposed and compliance efforts incomplete[17]. Addressing these risks is just as important as evaluating your primary vendors.
Cloud service providers add another layer of complexity. For instance, if your electronic health record (EHR) vendor depends on a cloud infrastructure provider, or your billing partner uses a third-party payment processor, you’re indirectly tied to those companies’ security practices. These relationships can lead to vulnerabilities in data handling, compliance gaps, or security lapses that often remain unnoticed until a breach occurs[2]. A security incident at a subcontractor can disrupt operations just as much as an issue with your primary vendor. This interconnected web of risks demands thorough oversight.
The first step in tackling this challenge is gaining clear visibility. Maintain an up-to-date inventory that not only tracks your direct vendors but also includes their subcontractors and technologies[1][17]. Make sure every fourth-party relationship is documented in contracts and audits[17]. If a vendor introduces a new sub-processor, immediately assess what types of data they’ll handle, where it will be stored, and whether your existing agreements offer sufficient protection[2].
When it comes to cloud providers, start by reviewing existing evidence like SOC 2 reports, ISO certifications, and penetration test summaries instead of jumping straight to lengthy questionnaires[2]. Set up continuous monitoring to catch updates in policies, the addition of new sub-processors, security incidents, or changes in data hosting locations[2]. Any of these changes should trigger a deeper review to confirm that the fourth party still meets your security and compliance standards.
Finally, ensure your risk management efforts are well-documented. Keep detailed records of the types of data involved, access levels, volumes, and the overall importance of each fourth-party relationship[2]. If a fourth-party risk becomes an issue, you’ll need evidence showing that you identified the dependency, evaluated the risks, and took appropriate actions - whether that meant accepting the risk, requiring additional safeguards, or switching to a different vendor. This proactive approach can make all the difference in maintaining security and trust.
6. Not Quantifying Business Impact and Financial Exposure
When it comes to third-party risk management (TPRM), identifying risks is just the starting point. The real game-changer is quantifying the financial impact of those risks. Unfortunately, many healthcare organizations stop short of this step. They recognize that a vendor poses a risk but rarely assign a dollar value to it. Without these numbers, leadership is left making decisions without the full picture. Adding financial context turns TPRM from a simple compliance task into an essential business function [23].
In healthcare, the stakes couldn’t be higher. Consider this: medical errors are the third leading cause of death in the U.S., leading to approximately 100,000 preventable deaths each year [24][25]. These errors cost around $20 billion annually, while hospital-acquired infections add another $35.7–$45 billion to the tab [24]. Now imagine a vendor failure disrupting electronic health record (EHR) systems, compromising medical devices, or exposing patient data. The financial and reputational fallout from such incidents can be devastating [7].
A breach or outage involving a critical vendor can result in lost revenue, increased operational costs, and hefty HIPAA penalties. It’s not just about money - it’s about the survival of operations and reputation. If you haven’t pre-quantified these scenarios, it’s nearly impossible to prioritize vendor relationships or secure the necessary funding to address these risks [1].
"Going outside approved corporate policies exposes your organization to unnecessary risk and could result in your project not receiving the funding it needs to be successful" [1].
To address this, start by identifying metrics that truly reflect the business impact. Track vendor compliance rates, calculate the costs of downtime for critical services, and estimate financial exposure from breaches of protected health information (PHI) or other vendor-related disruptions [1]. With 29% of data breaches stemming from third parties [26], these metrics provide leadership with a roadmap for prioritizing investments and mitigating risks effectively.
Without clear financial insights, your TPRM reports risk falling flat, failing to communicate their importance to executives who control budgets and strategic decisions. Quantifiable risk assessments are the key to driving action and securing the resources your organization needs to bolster its security posture. These insights lay the groundwork for deeper evaluations of vendor-related disruptions in future assessments.
sbb-itb-535baee
7. Overlooking Operational Technology and Connected Medical Devices
When it comes to third-party risk management (TPRM), healthcare organizations often zero in on traditional IT systems but neglect a major vulnerability: operational technology (OT) and connected medical devices. These include imaging systems, infusion pumps, ventilators, HVAC systems, elevators, and medical fluid systems. Increasingly, these devices are network-connected and frequently managed by third-party vendors, creating a unique set of risks. The stakes here are incredibly high - not just data breaches, but potential threats to patient care and safety [32][34].
The issue starts with connectivity. Many medical devices, originally designed to operate in isolation, are now part of intricate networks. This shift exposes them to vulnerabilities they weren’t built to handle [29]. For instance, suppliers may introduce firmware flaws, while the Internet of Medical Things (IoMT) expands the attack surface. A compromised network can leave devices vulnerable, disrupt operations, or even delay critical care [5][27][28]. Adding to the complexity, these devices are often maintained by manufacturers or local biomedical engineers, creating additional exposure points that demand specialized risk management [32].
The regulatory environment is also evolving quickly. On August 13, 2025, the Cybersecurity and Infrastructure Security Agency (CISA), in collaboration with the EPA, NSA, FBI, and international partners, issued guidance for OT operators to develop comprehensive asset inventories [31]. Similarly, in September 2023, NIST released SP 800-82 Rev. 3, titled "Guide to Operational Technology (OT) Security," offering detailed strategies for securing OT systems while balancing their performance, reliability, and safety requirements [35]. Excluding these devices from your TPRM program could leave your organization exposed to HIPAA violations, financial penalties, and reputational harm. Addressing these challenges requires a focused approach to OT risk management.
Just as traditional IT risks demand proactive management, OT and connected medical devices require the same level of attention. Consider these devices a core part of your TPRM strategy. Ensure your risk assessments cover medical devices, imaging systems, and clinical technologies [30][31]. To strengthen security, implement network segmentation to isolate essential systems, enforce strict access controls for third-party vendors, and deploy continuous monitoring tools designed specifically for OT environments [30][32][33]. By prioritizing OT in your TPRM efforts, you can better protect patient care and enhance overall safety.
8. Lacking Standardized, Documented Risk Decisions
When healthcare organizations make risk decisions without proper documentation or consistent criteria, they weaken their risk management efforts. Without a clear record, it becomes nearly impossible to explain or justify why certain decisions were made. This lack of transparency can expose the organization to penalties and legal risks during regulatory reviews and audits.[2]
Here's a concerning statistic: nearly 60% of healthcare breaches involve third-party vendors.[5] When agencies like the Office for Civil Rights (OCR) investigate, poor third-party due diligence - especially when driven by inconsistent criteria - can lead to class-action lawsuits, hefty fines, and thorough audits.
"During audits, customer reviews, or board reporting, you scramble to reconstruct lineage. 'We remember' isn't an acceptable control." - Whistic[2]
The core issue often lies in how decisions are made and tracked. Scattered documentation and unclear risk ratings leave many findings unresolved. As one expert put it:
"TPRM teams don't get credit for effort; they're measured on outcomes, evidence, and defensibility." - Whistic[2]
To tackle these issues, organizations need to adopt a consistent approach. Start by creating a clear rubric for risk tiering based on inherent risk and impact. Ensure findings are tracked through every stage with supporting evidence. Develop an audit pack that includes key details like vendor tier, reviewed evidence, residual risk, unresolved findings, and renewal dates. This pack should be easy to export and share. Incorporating standardized, documented risk decisions into your Third-Party Risk Management (TPRM) process strengthens the overall system. It also lays the groundwork for transitioning to automated and continuous risk evaluation, which will be discussed in the next section.[2]
9. Manual, Email-Driven TPRM Workflows That Don't Scale
Relying on manual tools to handle vendor assessments can lead healthcare organizations into a logistical nightmare. Teams often spend weeks chasing down vendors for documentation, untangling duplicate entries, and digging through endless email threads for approvals. This slows down onboarding processes and makes it nearly impossible to assess risks accurately as the number of vendors grows. The result? A system that struggles to maintain a reliable risk management framework.
The real issue lies in what gets overlooked. Without a centralized system, critical evidence is scattered across multiple locations. Risk ratings may fluctuate from year to year without any clear explanation, and important findings discussed in meetings may never be tracked to resolution. This fragmented approach highlights the dangers of disorganized documentation.
Such manual workflows also make teams reactive rather than proactive. Certifications often expire unnoticed until audits uncover the problem. There's no streamlined way to track which vendors have updated policies, added sub-processors, or reported incidents. This leaves high-risk relationships under-monitored and exposes organizations to avoidable vulnerabilities.
The problem worsens with a one-size-fits-all approach to vendor questionnaires. Sending massive spreadsheets to every vendor, regardless of their risk level, creates unnecessary delays. Strategic vendors grow frustrated, while teams drown in low-value tasks, diverting attention from more critical issues.
To address these challenges, healthcare organizations need to rethink their approach. Shifting from calendar-based reviews to signal-driven monitoring is a start. Centralizing vendor documentation, maintaining a comprehensive inventory, and leveraging existing attestations and certifications instead of relying solely on generic questionnaires are essential steps. Without these changes, manual workflows will continue to expose organizations to growing risks and inefficiencies.
10. Treating AI and Emerging Technologies as an Afterthought in TPRM
Emerging AI technologies bring unique challenges to Third-Party Risk Management (TPRM), requiring a more tailored approach. Healthcare organizations are increasingly partnering with vendors that leverage AI-powered diagnostics, machine learning algorithms, and advanced analytics to improve patient care and operational efficiency. However, many TPRM programs still rely on outdated evaluation methods that fail to address the specific risks tied to these technologies. This oversight can jeopardize data privacy, patient safety, and equitable treatment.
AI systems often rely on large volumes of sensitive patient data to function effectively. Without robust safeguards, this opens the door to potential misuse and cyberattacks. Questions around data ownership further complicate matters, leaving patients unsure of how their personal information is being handled.
Another major issue is algorithmic bias. AI models trained on incomplete or biased datasets can reinforce existing disparities in healthcare. These flaws can lead to diagnostic mistakes, inappropriate treatments, and regulatory scrutiny. To effectively manage these risks, your TPRM framework must include measures specifically designed for AI, ensuring a thorough and well-rounded assessment process.
Patient safety is also at stake when AI-driven decisions lack human oversight. Errors can go unnoticed, and the complexity of AI-related mistakes makes accountability difficult. Regulators are increasingly holding healthcare organizations accountable for failures linked to vendor technologies, adding another layer of responsibility.
To mitigate these risks, your TPRM program should adopt AI-specific evaluation practices. Start by identifying which vendors use AI or machine learning, the types of patient data they access, and how their algorithms are developed and validated. Use signal-driven monitoring to track when vendors introduce new AI features, change their data handling practices, or add sub-processors. Build detailed vendor profiles that include information on fourth-party technologies, breach history, and regulatory actions. This ensures that your assessments avoid approving opaque, "black-box" systems that could lead to financial losses, regulatory penalties, and erosion of patient trust. These AI-focused strategies align with the broader signal-driven monitoring approaches already discussed.
How to Modernize TPRM with Censinet
Healthcare organizations face mounting challenges with outdated and clunky third-party risk management (TPRM) processes. These legacy methods often struggle to keep pace with the fast-moving vendor landscape. That’s where Censinet steps in, offering a streamlined, automated solution to modernize TPRM.
Censinet RiskOps™ acts as a centralized platform for managing all third-party risk activities. Instead of relying on fragmented spreadsheets and endless email threads, it introduces automated workflows that eliminate delays caused by a lack of visibility into vendor risks. Censinet AITM takes vendor assessments to the next level, allowing vendors to complete security questionnaires in seconds. It automatically compiles evidence, summarizes documentation, and generates risk summary reports using all relevant data. This approach solves the scalability issue that plagues manual TPRM, where security teams often get bogged down in paperwork while critical risks go unnoticed.
The platform also shifts from outdated, calendar-based annual reviews to signal-driven monitoring. This means that when significant changes occur - like evidence expiring, policy updates, new sub-processors, or security incidents - the system instantly notifies the right stakeholders. These alerts are paired with defined service-level agreements (SLAs), ensuring that your organization’s risk posture stays up-to-date rather than relying on outdated information.
Here’s how Censinet compares to traditional TPRM methods:
| Traditional TPRM Methods | Censinet RiskOps™ |
|---|---|
| One-size-fits-all questionnaires for every vendor | Targeted, evidence-first questionnaires focused on specific gaps |
| Annual reviews that miss real-time changes | Automated workflows with SLA-driven task management |
| Disorganized documentation spread across emails and spreadsheets | Centralized vendor profiles with automated evidence tracking |
| Reactive decision-making with inconsistent risk standards | Standardized rubrics for tiering, scoring, and defensible risk decisions |
Censinet doesn’t stop at automation. Its suite includes Censinet One™, which offers on-demand risk management support, and Censinet Connect™, designed to simplify collaborative vendor assessments. These tools elevate TPRM from a mere compliance task to a strategic initiative that safeguards patient safety, minimizes financial risks, and grows alongside your organization.
Conclusion
Third-party vendors play a vital role in keeping healthcare systems running smoothly. When third-party risk management (TPRM) falls short, it can disrupt critical aspects of care - like timely diagnoses, treatments, and provider communication. These disruptions underscore the importance of having a well-structured TPRM approach.
The stakes are incredibly high. Vendor failures can lead to billions of dollars in losses annually, stemming from issues like medical errors and hospital-acquired infections. Beyond the financial impact, these failures erode patient trust. On a global scale, patient harm is estimated to reduce economic growth by 0.7% each year, with indirect costs soaring into the trillions [36].
Modern challenges demand modern solutions. Evidence-based workflows and signal-driven monitoring have become essential tools in shifting from reactive to proactive risk management. Platforms like Censinet RiskOps™ are leading the way by offering healthcare-specific solutions. These platforms centralize vendor documentation, automate evidence tracking, and provide real-time responses to significant changes - moving away from outdated annual review cycles [1][2].
FAQs
How does continuous monitoring improve third-party risk management (TPRM) for healthcare organizations?
Continuous monitoring plays a critical role in third-party risk management (TPRM) by providing real-time insights into vendor risk levels. This enables healthcare organizations to promptly spot and address potential vulnerabilities, minimizing the likelihood of security breaches and ensuring they stay compliant with regulatory requirements.
With a proactive approach, healthcare providers can safeguard sensitive patient information, maintain smooth operations, and prevent costly disruptions tied to vendor-related risks. Ongoing oversight ensures that risks are handled effectively as they emerge, protecting both the organization and its stakeholders.
What are the risks of using generic questionnaires for third-party risk management in healthcare?
Using generic questionnaires in healthcare third-party risk management (TPRM) often results in gaps in evaluating vendor security and compliance. These standardized tools are not tailored to the unique risks or regulatory demands that healthcare organizations face, leaving critical areas unaddressed.
The downside? Overlooked vulnerabilities. Generic questionnaires might miss essential controls or rely too much on vendor self-reports, which aren't always reliable. This can leave your organization exposed to cybersecurity risks, potential data breaches, and hefty regulatory fines.
Why is it important to align TPRM with procurement and contracting processes?
Integrating Third-Party Risk Management (TPRM) into procurement and contracting processes plays a crucial role in creating a unified approach to identifying and managing risks. This integration ensures that potential issues are flagged early, making vendor onboarding and offboarding more efficient while cutting down on unnecessary delays.
It also enhances communication between teams, ensures adherence to company policies, and enables proactive oversight of third-party relationships. For healthcare organizations, embedding TPRM into these workflows helps reduce exposure to risks, secure sensitive information, and protect the integrity of their operations.
Related Blog Posts
- Common Healthcare Third-Party Risk Assessment Questions
- The Complete Guide to Healthcare Third-Party Risk Management: From Basics to Advanced Strategies
- The Business Case for Healthcare TPRM: Cost Savings and Risk Reduction Statistics
- Healthcare Third-Party Risk Management Maturity Model: Where Does Your Organization Stand?


