Cybersecurity Vendor Risk Assessment: Protecting Healthcare from Third-Party Breaches
Post Summary
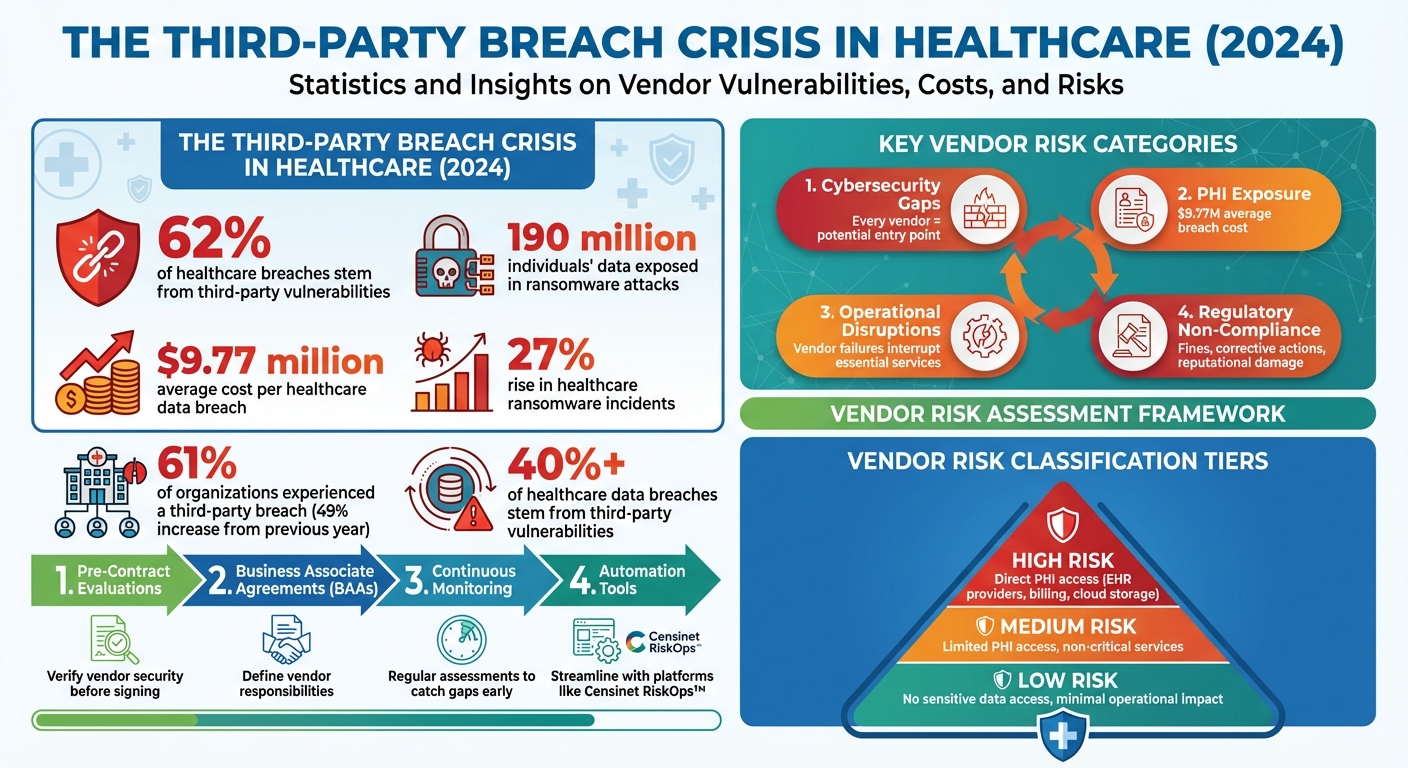
Healthcare organizations rely heavily on third-party vendors, but these partnerships come with risks. In 2024, 62% of healthcare breaches stemmed from third-party vulnerabilities, costing an average of $9.77 million per breach. Weak encryption, poor patching, and excessive access permissions are common issues that leave sensitive patient data exposed. To address these risks, healthcare providers must implement structured vendor risk assessment programs, focusing on:
- Pre-contract evaluations: Verify vendor security before signing agreements.
- Business Associate Agreements (BAAs): Clearly outline vendor responsibilities for protecting patient data.
- Continuous monitoring: Regularly assess vendors to catch security gaps early.
- Automation tools: Streamline assessments and improve efficiency with platforms like Censinet RiskOps™.
The stakes are high - not just for compliance, but for patient safety and trust. A proactive approach to vendor risk management ensures healthcare providers can minimize disruptions, safeguard sensitive data, and maintain operational integrity.
Healthcare Third-Party Breach Statistics and Vendor Risk Assessment Framework 2024
Third-Party Cybersecurity Risks in Healthcare
Common Third-Party Threats
Hospitals, on average, work with over 1,300 vendors, and every one of these partnerships could be a potential vulnerability for cyberattacks [7]. From cloud-based EHR providers to telehealth platforms, medical device manufacturers, and billing services, each connection opens the door to possible exploitation. Cybercriminals have shifted their focus, increasingly targeting third-party vendors that support healthcare organizations instead of attacking hospitals directly [4]. This centralized approach allows hackers to compromise a single vendor and, in turn, gain access to multiple healthcare entities [3].
Research highlights the severity of the issue: over 40% of healthcare data breaches stem from third-party vulnerabilities. A 2024 study on Third-Party Risk Management revealed that 61% of organizations experienced a third-party data breach or cybersecurity incident - a staggering 49% increase from the previous year [4][5][6]. In the same year, ransomware attacks exposed data belonging to 190 million individuals, with a 27% rise in healthcare-related ransomware incidents compared to the prior year [4].
When vendor systems are breached, the consequences can significantly disrupt patient care - sometimes more so than direct attacks on hospitals [3]. Common weak points include devices that lack encryption, outdated software with poor patch management, and vendors who fail to adhere to strict security standards [6]. Such breaches can ripple across healthcare networks, halting clinical operations and exposing sensitive patient information. These vulnerabilities fall into several key categories that require focused attention.
Key Risk Categories
Third-party cybersecurity risks in healthcare can be grouped into several major categories, each with the potential to impact clinical operations and patient safety. The most pressing concern is cybersecurity gaps. Every vendor represents a possible entry point for attackers [6]. Limited insight into a vendor’s security practices makes it difficult to ensure adequate protection, while excessive remote access permissions often grant vendors more network access than necessary [6].
Another critical risk is the exposure of private health information (PHI), which carries steep financial penalties. In 2024, the average cost of a data breach in healthcare reached $9.77 million, making even small incidents financially devastating [4][5]. Operational disruptions also pose significant risks, as vendor system failures can interrupt essential services, jeopardizing patient care and safety [6]. Regulatory non-compliance adds another layer of risk, with potential fines, corrective action plans, and reputational damage that can erode patient trust and harm an organization’s standing in the community [6].
Regulatory Requirements and Business Associate Agreements
To address these risks, compliance with regulatory frameworks is essential. Under HIPAA, any vendor handling electronic protected health information (ePHI) on behalf of a healthcare organization is considered a business associate. To manage these risks, healthcare organizations rely on Business Associate Agreements (BAAs), which outline the cybersecurity standards vendors must follow. These agreements specify how vendors will protect ePHI, the security measures they will implement, and the steps they’ll take in the event of a breach.
A well-crafted BAA includes clear, actionable requirements, often using "if-then" language to define responsibilities and consequences for non-compliance [2][7]. For example, contracts might mandate data encryption and detail remediation steps if those encryption standards aren’t met. Beyond HIPAA’s requirements, many organizations are turning to established frameworks like the NIST Cybersecurity Framework (CSF) and ISO 27001. These frameworks provide a structured approach for assessing vendor security, conducting risk evaluations, and ensuring ongoing compliance.
To stay ahead of evolving regulations, healthcare organizations must regularly update their BAAs and vendor assessment practices. This proactive approach helps avoid costly penalties and ensures the protection of sensitive patient data.
Building a Vendor Risk Assessment Program
Setting Scope, Governance, and Roles
The backbone of any strong vendor risk assessment program lies in solid governance. For healthcare organizations, this starts with securing executive sponsorship. When leadership prioritizes third-party risk management, it sets the tone for accountability and continuous improvement. A dedicated vendor risk management team or professional should be in place, working closely with key representatives from executive leadership, IT, legal, compliance, and procurement teams to ensure a coordinated effort [7][8][2].
Assigning clear roles is essential. For example, the Chief Information Security Officer (CISO) can oversee technical assessments, the Chief Information Officer (CIO) can align vendor technology with organizational goals, and privacy officers can focus on HIPAA compliance. Once these roles are defined, the next step is to document all vendor relationships thoroughly.
Vendor Inventory and Risk Classification
A complete vendor inventory is the foundation for understanding risk exposure. This inventory should extend beyond direct vendors to include subcontractors and service providers - often referred to as fourth- and fifth-party relationships. Each vendor needs to be cataloged based on their access to sensitive data, such as protected health information (PHI), their level of access to critical systems, and their overall role in clinical operations.
Using a tiered risk model can help classify vendors into low, medium, or high-risk categories [2]. For instance:
- High-risk vendors: Those with direct access to PHI, such as EHR providers, billing companies, or cloud storage services.
- Medium-risk vendors: Those with limited PHI access or who provide non-critical services.
- Low-risk vendors: Vendors with no access to sensitive data and minimal impact on operations.
This classification process should also take into account potential financial costs, patient safety risks, and operational disruptions. Once vendors are categorized, organizations can define their risk appetite, which helps prioritize which risks to address first.
Defining Risk Appetite and Scoring Models
To set a proper risk appetite, organizations must determine how much risk they are willing to tolerate before additional safeguards are needed or a vendor relationship needs reevaluation. HIPAA provides a framework for this by requiring healthcare organizations to conduct "an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information" [9][10][12]. However, HIPAA allows flexibility in how this is done, depending on the organization's size, complexity, and resources.
Risk is essentially a combination of the likelihood of a threat exploiting a vulnerability and the potential impact of that event. For each identified risk, organizations should estimate both the probability of occurrence and the magnitude of harm, categorizing them as low, medium, or high. Factors to consider include PHI exposure, operational disruptions, financial losses, regulatory penalties, reputational harm, and impacts on patient trust and care [12].
A vendor scoring system can help prioritize risks more effectively. Metrics like HIPAA compliance, the severity of past violations, and the completion of corrective actions can guide decision-making. A risk matrix - where likelihood and impact ratings are combined (e.g., "High likelihood + High impact = Critical risk") - offers a straightforward way to prioritize assessments and remediation efforts [9][12].
This scoring model also informs the implementation of safeguards - whether administrative, physical, or technical - in line with HIPAA’s "reasonable and appropriate" standard [9][10]. Regular, comprehensive risk assessments should be conducted at least annually or whenever there are significant changes, such as the adoption of new technologies, security incidents, or updates to regulatory requirements [9][11][12].
Conducting Vendor Cybersecurity Assessments
Vendor Risk Assessment Workflow
Start cybersecurity risk assessments before signing any contracts. The process kicks off with tailored security questionnaires that delve into key areas like encryption, access controls, incident response plans, and disaster recovery protocols. These responses are then evaluated against established cybersecurity frameworks, which focus on five key areas: identification, protection, detection, response, and recovery.
Once the responses are collected, organizations score and validate the vendor's risk level. This involves comparing the answers to the organization's defined risk tolerance and scoring criteria. If concerning issues arise - like missing encryption protocols or weak access controls - it may require further investigation or corrective measures before proceeding with the contract. To make the process smoother and faster, many organizations now use automation tools to handle these assessments.
Automation in Vendor Assessments
Managing vendor assessments manually can quickly become overwhelming, especially when dealing with numerous third-party relationships. Automation tools simplify this process by reusing validated responses from previous assessments, flagging incomplete or inconsistent answers, and scoring risks in real time. This not only saves time but also helps reduce "questionnaire fatigue" by minimizing redundant efforts.
For healthcare risk teams in particular, automation centralizes vendor-related data and risk scores, making it easier to track and manage. Automated workflows also ensure timely notifications for stakeholders, keeping reviews and approvals on schedule without unnecessary delays.
Manual vs. Automated Assessment Methods
When conducting cybersecurity assessments at scale, the contrast between manual and automated methods becomes striking. Here's a breakdown of how they compare:
| Aspect | Manual (Spreadsheet) | Automated (Censinet RiskOps™) |
|---|---|---|
| Speed | Slow due to manual data entry and follow-ups | Fast, with pre-filled responses and automated scoring |
| Auditability | Limited, with no built-in version control or tracking | Comprehensive audit trails, complete with timestamps and workflows |
| Scalability | Capped by available staff resources | Efficiently handles a large volume of assessments |
| Evidence Storage | Scattered across emails and shared drives | Centralized, searchable storage with clear documentation tracking |
| Risk Visibility | Static snapshots requiring manual updates | Real-time dashboards that reflect up-to-date risk statuses |
sbb-itb-535baee
Managing Vendor Risk Across the Lifecycle
Risk Management in the Vendor Lifecycle
Managing vendor risk isn’t a one-and-done task - it’s an ongoing process that spans the entire vendor relationship. It starts with pre-contract due diligence, where you verify certifications, review past incidents, and ensure compliance with key regulations like HIPAA.
Once a vendor is onboarded, continuous monitoring becomes critical. Many organizations make the mistake of conducting a single assessment and then assuming everything is fine. But with vendor-related attacks increasing by over 400% in just two years [2], yesterday's secure vendor could become today's vulnerability. Regular oversight helps mitigate this risk.
When it’s time to offboard a vendor, it’s essential to act decisively. Revoke all access immediately, securely return or destroy any shared data, and document the entire process for audit purposes. A cautionary example comes from the 2016 Banner Health breach, where hackers accessed 3.7 million records via a third-party payment processor for their food court [2]. This case underscores the importance of managing risk at every stage - even with vendors that seem low-risk.
Continuous Monitoring and Risk Treatment
Point-in-time assessments are no longer enough. Continuous monitoring is the only way to catch compliance lapses before they lead to breaches. Use ongoing compliance reports like HITRUST, SOC 2 Type 2, or ISO 27001 certifications [2] instead of relying on static evaluations.
A Plan of Action and Milestones (POA&M) can help track and prioritize remediation efforts systematically [7]. This ensures vulnerabilities don’t fall through the cracks. Trigger-based reviews should also be part of your strategy, automatically kicking in after events like security incidents, vendor mergers, or major updates to systems that handle protected health information (PHI). These proactive measures build on initial assessments to maintain a strong security posture.
Third-party vendors should also be integrated into your incident response plans, disaster recovery tests, and business continuity strategies [7]. Clear communication protocols are essential so everyone knows their role during emergencies. With third-party vulnerabilities accounting for 62% of breaches [1] and healthcare data breaches averaging nearly $10 million in costs [2], these steps are vital - not just for compliance, but for safeguarding patient trust and organizational stability.
Using Censinet RiskOps™ as a Central Hub
Centralizing vendor risk management can simplify oversight and improve efficiency. Censinet RiskOps™ offers real-time dashboards and a single source of truth, enabling IT, legal, procurement, and compliance teams to collaborate seamlessly [2]. This ensures everyone is working with the most up-to-date information.
The platform includes features like automated HIPAA Security Rule Testing, Policy Attestation Workflows, and Vendor Tiering based on PHI access levels. These tools help keep your organization compliant and audit-ready [1]. With 41% of third-party breaches in 2024 projected to hit healthcare organizations [7], having centralized control over vendor risk isn’t just helpful - it’s essential.
Censinet AITM takes this a step further by automating security questionnaires, summarizing evidence, and generating detailed risk reports in seconds. This blend of automation and oversight allows risk teams to evaluate more vendors efficiently, without cutting corners on safety or thoroughness. It’s a practical way to scale up your risk management efforts while maintaining focus on patient protection and operational integrity.
Conclusion
For healthcare organizations, vendor risk assessment isn't just a best practice - it's a regulatory requirement and a critical element of patient safety. In 2024, a staggering 41% of third-party breaches impacted healthcare organizations [7]. With third-party vulnerabilities responsible for 62% of breaches [1] and each incident costing nearly $10 million [2], the stakes couldn't be higher. Beyond the financial burden, these breaches disrupt clinical operations and jeopardize patient care.
Given these risks, the old approach of periodic checks and vendor self-certifications is no longer sufficient. The current threat landscape demands continuous monitoring, standardized processes, and centralized oversight. This includes embedding cybersecurity clauses into Business Associate Agreements, focusing on high-risk vendors, and maintaining a structured Plan of Action and Milestones to track and address vulnerabilities.
Censinet RiskOps™ simplifies vendor risk management through real-time dashboards, automated HIPAA Security Rule Testing, and vendor tiering based on PHI access, ensuring scalable and audit-ready evaluations. Meanwhile, Censinet AI™ accelerates the process by automating security questionnaires and generating detailed risk reports in seconds, enabling teams to assess more vendors without sacrificing thoroughness. These tools not only streamline the assessment process but also foster a proactive stance on patient safety.
Adopting a lifecycle-based approach to vendor risk assessment transforms potential threats into manageable security measures. From pre-contract evaluations to secure offboarding, a proactive strategy is essential to protect patient data and maintain trust. This goes beyond mere compliance; breaches erode patient safety and confidence. By implementing structured risk assessment programs and utilizing centralized platforms, healthcare organizations can turn vendor risk into a measurable and controlled aspect of their broader security strategy.
FAQs
What are the essential steps in assessing third-party cybersecurity risks for healthcare organizations?
A strong vendor risk assessment program in healthcare involves several key steps to safeguard sensitive patient information and maintain compliance. Start by examining a vendor's security measures, including practices like patch management, vulnerability scanning, and incident response protocols. Next, review their privacy and data protection policies to ensure they align with standards for safeguarding confidentiality and managing access. It's also important to evaluate the vendor’s financial health to identify risks, such as potential bankruptcy, that could disrupt operations.
In addition, confirm the vendor's adherence to critical regulations like HIPAA and industry standards such as SOC 2 or ISO 27001. To maintain ongoing protection, establish continuous monitoring and plan for regular reassessments. This proactive approach helps address new threats and ensures your security framework remains effective.
What is the role of continuous monitoring in managing third-party cybersecurity risks?
Continuous monitoring is essential for shielding healthcare organizations from risks associated with third-party cybersecurity. It enables early detection of vulnerabilities, flags unusual activities promptly, and ensures vendors stay aligned with regulations like HIPAA in real time.
This constant oversight into vendor systems and operations empowers healthcare organizations to act swiftly against potential threats, minimizing the chances of data breaches and protecting sensitive patient information effectively.
Why is a Business Associate Agreement (BAA) necessary when working with healthcare vendors?
A Business Associate Agreement (BAA) plays a critical role when partnering with healthcare vendors. It ensures compliance with HIPAA regulations while clearly defining responsibilities for protecting protected health information (PHI). This legal document spells out the vendor's duties, like implementing security measures, safeguarding sensitive data, and providing immediate notification if a breach occurs.
With a BAA in place, healthcare organizations can better protect themselves from liability, strengthen patient confidence, and ensure that third-party vendors are committed to upholding strict data security standards.


