HIPAA Standards for Digital Identity
Post Summary
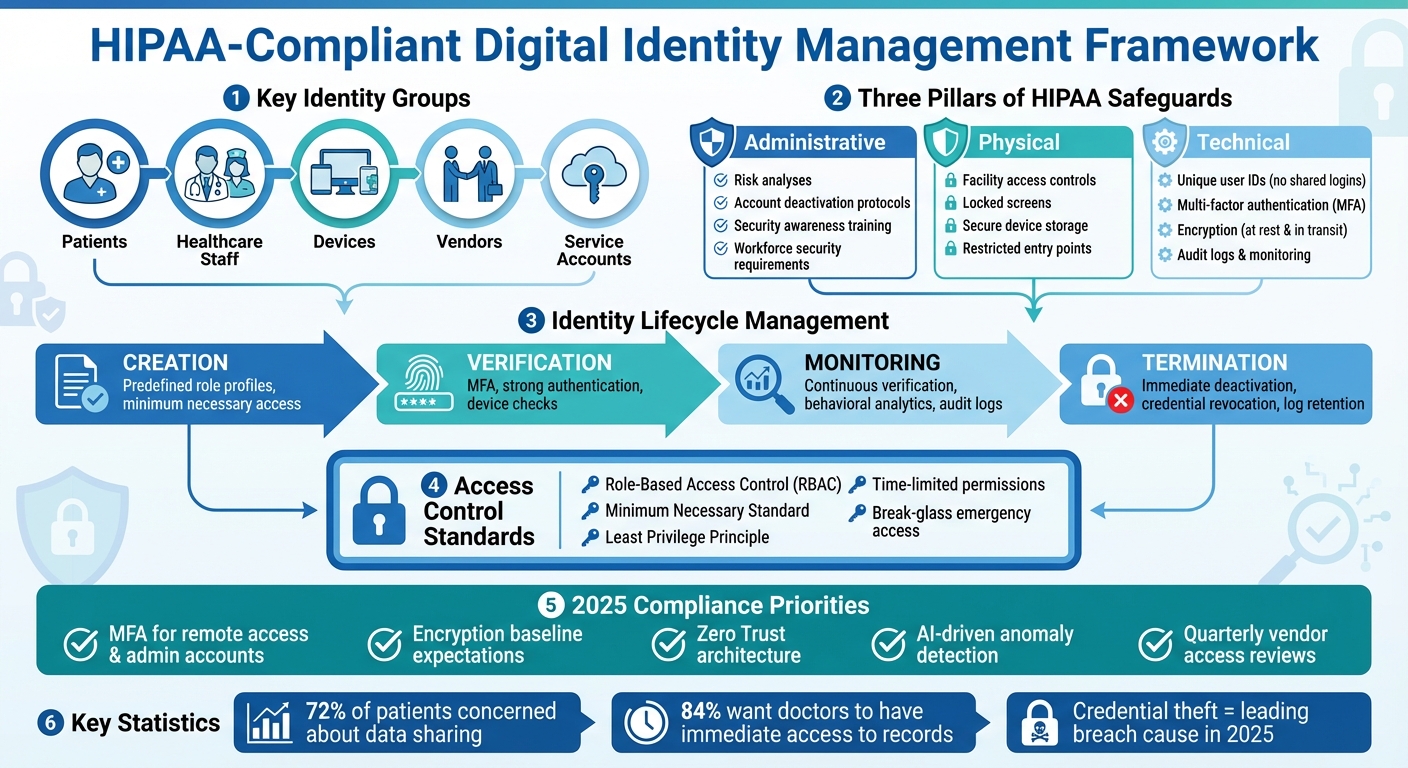
HIPAA Standards for Digital Identity focus on managing secure access to electronic protected health information (ePHI) by defining how digital identities - like user accounts, devices, and third-party vendors - are created, verified, and monitored. Here's a quick breakdown:
- Key Groups: Patients, healthcare staff, devices, vendors, and service accounts all require tailored access controls.
- HIPAA Rules: Privacy and Security Rules enforce safeguards like unique user IDs, multi-factor authentication (MFA), encryption, and audit logs.
- 2025 Trends: Breaches are increasingly caused by stolen credentials, making robust identity management critical.
- Access Controls: Role-based permissions and the "minimum necessary" standard limit ePHI access to what's essential for specific tasks.
- Third-Party Risks: Vendors handling ePHI must meet strict identity and access standards through Business Associate Agreements (BAAs).
- Zero Trust: Continuous verification and granular permissions reduce risks of credential misuse and data breaches.
To ensure compliance, organizations should implement MFA, automate account management, conduct regular audits, and train staff on secure practices. These measures not only meet regulatory requirements but also protect patient privacy and data integrity.
HIPAA-Compliant Digital Identity Management Framework
HIPAA Standards That Affect Digital Identity
HIPAA Rules for Digital Identity
The HIPAA Security Rule serves as the backbone for how healthcare organizations manage digital identities tied to electronic protected health information (ePHI). It outlines requirements under three key categories - administrative, physical, and technical safeguards - that collectively shape how identities are created, verified, and monitored [3].
Administrative safeguards require organizations to conduct formal risk analyses and promptly deactivate accounts when roles change. These measures ensure that access is only granted to authorized individuals and that ongoing activity is properly monitored. Additionally, security awareness training equips employees to use credentials securely and recognize threats like phishing [3].
Physical safeguards focus on protecting access to systems and devices that handle ePHI. Measures like facility access controls, locked screens, secure storage for devices, and restricted entry points are designed to prevent unauthorized access to authenticated sessions or physical systems [3].
Technical safeguards lay out specific requirements for managing identities. For instance, the access control standard mandates assigning unique identifiers to each individual accessing ePHI, banning shared logins. The authentication standard requires verifying the identity of users, often through strong passwords and multi-factor authentication (MFA). Audit controls ensure detailed logging of access events, including who accessed PHI, when, and from where, to aid in compliance checks and incident investigations [3].
Together, these safeguards inform how role-based restrictions are implemented under the "minimum necessary" standard.
Minimum Necessary Access and Role-Based Permissions
The HIPAA Privacy Rule’s "minimum necessary" standard requires organizations to limit access to PHI strictly to what’s essential for a specific task [5]. In practice, this is often achieved using role-based access control (RBAC). Roles are defined based on typical job functions - such as an emergency nurse, billing specialist, or IT administrator - and permissions are assigned accordingly to ensure each role accesses only the necessary PHI. Automating the provisioning, modification, and deactivation of user accounts as roles change helps maintain compliance with this principle [5].
Recent updates to HIPAA rules have further reinforced the need for robust identity verification measures.
2025 HIPAA Security Rule Updates
While the Security Rule itself remains technology-neutral, enforcement trends now demand stronger identity controls. Multi-factor authentication (MFA), once considered optional, is increasingly seen as a "reasonable and appropriate" safeguard for remote access, VPNs, administrative accounts, and cloud-based electronic health record (EHR) systems. Simply relying on passwords is no longer sufficient [2][4].
Encryption of ePHI, both at rest and in transit, is also becoming a baseline expectation, especially for cloud platforms, mobile devices, and remote monitoring systems. Although originally an addressable specification, encryption is now critical for protecting sensitive data [2][4]. Additionally, emerging guidance for AI-driven health tools and online tracking emphasizes the need for advanced logging, anomaly detection, and continuous monitoring to track who accesses PHI and to flag unusual activity in near real time [4][9].
To meet these growing compliance demands, organizations should prioritize MFA, modern encryption techniques, centralized logging, and behavioral monitoring as standard practices. Risk analyses should document how these controls address threats like ransomware, account takeovers, and misuse of AI-enabled tools [2][4]. Platforms like Censinet RiskOps™ can assist by benchmarking identity and encryption controls against industry standards and tracking remediation efforts across both internal systems and third-party environments.
How to Build HIPAA-Compliant Identity Controls
Identity Lifecycle Management
When managing digital identities tied to ePHI, a structured lifecycle - from creation to termination - is crucial for meeting HIPAA's administrative safeguards. Start by using predefined role profiles during onboarding. These profiles should outline the systems and data each role requires, ensuring access is limited from the beginning. This approach minimizes the risk of granting unnecessary permissions upfront.
To prevent "access creep" - where permissions gradually exceed job requirements - require HR and data owner approval for any role changes. Implement suspension processes that can swiftly disable accounts when necessary, while keeping audit logs intact for future review. When an employee leaves, their access must be disabled by the end of their final working day, and all credentials - badges, VPN tokens, mobile access, and shared-system logins - should be revoked promptly.
For clinicians, temporary access adjustments, such as granting access to specialty applications during rotations, can balance compliance with operational flexibility. These adjustments should be configured to automatically expire. Failure to manage these lifecycle stages properly can lead to orphaned accounts or excessive permissions, increasing the risk of breaches and violating HIPAA's workforce security requirements.
Once identities are effectively managed, implementing strong authentication measures becomes the next key step.
Authentication and Multi-Factor Authentication (MFA)
HIPAA mandates that covered entities authenticate individuals and entities seeking access, though it doesn’t specify which technologies to use. Organizations should select authentication measures based on a thorough risk analysis.
Multi-factor authentication (MFA) is a critical tool for securing remote access, such as VPNs, cloud-based EHRs, or administrative systems, and for high-risk activities like prescribing controlled substances or managing identity systems. Common MFA options include mobile push notifications, hardware tokens, smartcards, and biometric methods like fingerprint or facial recognition. In clinical settings, proximity badges and tap-to-sign-in methods can streamline workflows while safeguarding sensitive data. To reduce workflow disruptions, risk-based MFA can step in only when unusual access patterns are detected, like off-network logins, new devices, or attempts to access highly sensitive ePHI. Within secure environments, single sign-on (SSO) can further enhance efficiency.
Session management is another critical aspect. HIPAA’s technical safeguards require automatic logoff after inactivity. In clinical settings, shorter screen-lock timeouts (e.g., two to five minutes of inactivity) combined with quick re-authentication methods can maintain security without delaying care. For remote or high-risk access, full re-authentication, including MFA, should be required after extended inactivity or before performing sensitive actions like exporting data. Limiting concurrent sessions can also discourage account sharing and improve accountability.
Explicitly banning credential sharing and actively monitoring for shared-account activity are essential for maintaining compliance.
Access Control and Authorization
With a secure identity lifecycle and strong authentication in place, role-based access control (RBAC) ensures that ePHI access aligns with HIPAA’s strict standards. RBAC organizes permissions based on job functions, such as those for nurses, physicians, or administrative staff, ensuring that users only access what’s necessary for their roles.
HIPAA’s minimum necessary standard requires that access to ePHI be restricted according to a user’s responsibilities. Start by conducting a comprehensive inventory of permissions across systems - like EHRs, digital imaging, billing, and ancillary applications - and map these permissions to a manageable set of roles. These roles should be validated by both clinical and operational leaders.
The principle of least privilege should guide role design, granting only the rights needed for specific tasks. In emergencies, “break glass” access can provide temporary permissions, but this access must be logged and reviewed regularly. For more granular control, Attribute-Based Access Control (ABAC) can factor in context, such as location, time of day, device type, or treatment relationship. For instance, ABAC might allow a social worker to view certain fields without granting edit rights or restrict access to sensitive behavioral health notes based on specific provider attributes.
For occasional administrative needs, grant time-limited or just-in-time elevated access, ensuring automatic revocation and detailed logging. Comprehensive session logs - tracking login times, device details, locations, and accessed systems - are invaluable for forensic investigations. These logs can also integrate with SIEM platforms to detect anomalies. Tools like Censinet RiskOps™ can help healthcare organizations benchmark their identity and access controls against industry standards while tracking remediation efforts across internal and third-party systems.
Third-Party Access and Advanced Identity Methods
Managing Vendor and Third-Party Access
In healthcare, third-party vendors like cloud providers, telehealth platforms, billing services, and medical device support teams introduce significant identity risks. Under HIPAA, any vendor handling PHI is classified as a business associate and must meet the same identity and access management standards as your organization [3][2].
Start by establishing Business Associate Agreements (BAAs) that explicitly outline identity-related requirements. These agreements should specify the use of unique user IDs, multi-factor authentication (MFA) for remote access, role-based permissions, and detailed activity logging. During onboarding, verify each vendor's identity and assign time-limited, task-specific access based on the project or contract scope. For instance, a technician troubleshooting a medical imaging system should only have access to that system's administrative console, with credentials that automatically expire once the task is complete.
Require MFA for all remote vendor access, particularly for privileged accounts like system administrators. Conduct quarterly access reviews, where managers assess the necessity of each vendor account, and promptly deactivate any that are no longer required. Include strict credential policies in vendor BAAs and monitor session logs to identify shared-account usage.
Platforms such as Censinet RiskOps™ simplify vendor risk assessments by enabling secure sharing of questionnaires and evidence. Terry Grogan, CISO at Tower Health, shared:
Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required. [1]
AI and Automation in Identity Governance
AI and automation are transforming identity governance by streamlining processes for both internal users and vendors. Behavior analytics can detect unusual access patterns - like a vendor account querying thousands of patient records, accessing systems outside approved hours, or logging in from an unexpected location. These anomalies can trigger automatic step-up authentication or alerts for security teams [8][4].
Automation also minimizes manual effort by creating and removing accounts based on events from HR systems, contract management tools, or ticketing platforms. For example, when a vendor contract ends or a support ticket is resolved, access can be revoked almost instantly, reducing the risk of orphaned accounts. AI can further optimize least-privilege access by analyzing actual usage patterns, flagging high-risk entitlements, and identifying dormant accounts during periodic reviews.
For AI systems that handle PHI - such as diagnostic tools or predictive analytics platforms - HIPAA's privacy and security rules still apply. Vendors must sign a BAA, and organizations should limit data inputs to the minimum necessary for the task. Strong access controls, encryption, and clear documentation of data flows, model training practices, and retention policies are essential [3][4].
AI-driven identity tools should follow privacy-by-design principles: use pseudonymous identifiers when possible, separate operational security data from clinical information, and regularly validate models to prevent biased or false alerts that could disrupt care or unfairly target certain user groups [8][3][4].
Zero Trust and Continuous Verification
Zero Trust takes identity security to the next level by assuming no implicit trust - even for users within the network. Every access request is continuously verified, based on user credentials, device status, and contextual information [2][3]. This identity-centric approach is essential for protecting ePHI across platforms like EHRs, imaging systems, billing applications, and cloud services.
Key principles of Zero Trust include: explicit verification using strong authentication, device checks, and behavioral analytics; enforcing least-privilege access with granular permissions; and preparing for breaches through micro-segmentation, thorough logging, and rapid containment [2][3]. For example, micro-segmentation can isolate your EHR system from lab and billing platforms, ensuring that a compromised vendor credential or workstation cannot access all PHI repositories [7].
Context-aware access adds another layer of security by factoring in variables like location, time of day, device type, and the user's relationship to the data. For instance, a social worker accessing behavioral health records during business hours from a hospital workstation might be granted access, while an attempt from a personal device late at night could prompt additional verification or be denied. Many healthcare breaches have stemmed from compromised vendor credentials or remote access tools, leading to ransomware attacks and large-scale PHI exposure [2][6].
In a Zero Trust framework, vendor sessions are restricted to specific applications, and combining MFA with device checks significantly reduces the risk of credential-only breaches. AI-driven analytics further enhance security by identifying and containing abnormal behaviors before they escalate [8][2][4].
Continuous monitoring and logging are crucial for meeting HIPAA's audit requirements and ensuring rapid incident response. These logs provide a clear record of third-party activities, such as those of medical device vendors or managed service providers [3][2]. Regularly test Zero Trust controls through tabletop exercises and technical assessments, focusing on vendor access paths and privileged accounts, to ensure your defenses remain effective.
sbb-itb-535baee
Governance and Ongoing Compliance for Identity
Once strong identity controls are in place, keeping up with HIPAA compliance means staying proactive with governance and conducting regular reviews.
Identity Risk Management Under HIPAA
The HIPAA Security Rule mandates a continuous risk management process to identify, evaluate, and address threats to electronic protected health information (ePHI). This includes risks tied to identity and access controls. Organizations are required to perform a risk analysis at least once a year or whenever significant system updates occur. These assessments should account for all systems housing ePHI, every user and service identity (including workforce members, clinicians, contractors, vendors, patients, and devices), and the authentication and authorization methods in use.
Key data points to collect include the number and type of privileged accounts, the use of shared or generic logins, whether multi-factor authentication (MFA) is in place for remote or high-risk access, the presence of orphaned accounts after terminations, and whether access rights align with role-based or least-privilege models. The frequency of access reviews should also be tracked. Identity risks must be documented in the enterprise risk register and assessed based on a consistent method that considers the likelihood of an event and its potential impact on clinical operations, patient safety, regulatory compliance, and financial outcomes.
Tools like Censinet RiskOps™ can help healthcare organizations continually monitor and mitigate identity-related risks across patient data, medical records, third-party access, and clinical applications. Brian Sterud, CIO at Faith Regional Health, highlights the importance of this approach:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." [1]
Policies, Training, and Awareness
HIPAA-compliant policies should address key areas such as access control, user account management, authentication requirements (including passwords and MFA), role-based and minimum necessary access, remote and vendor access, sanctions for violations, and incident reporting. These policies must clearly define roles, technical expectations, and audit procedures.
Training is another critical component. It should be tailored to specific roles, include practical scenarios, and be conducted regularly. All workforce members need foundational training on safeguarding ePHI, the importance of unique credentials, and the risks of password sharing. Clinicians and frontline staff, in particular, should learn best practices like avoiding shared logins, verifying identities before discussing PHI, properly using MFA tools, and recognizing phishing attempts targeting systems like patient portals or EHRs. Training programs should feature real-world examples of identity-related HIPAA breaches and offer short, focused updates - such as quarterly micro-learning modules or phishing simulations - alongside comprehensive onboarding. Keeping detailed records of attendance and completion is essential for audit purposes and to demonstrate compliance.
Audits and Continuous Improvement
Audits of identity and access controls should combine automated and manual reviews and occur at least annually. High-risk systems and privileged accounts may require more frequent checks. Core audit activities include verifying that user accounts are unique, active, and properly authorized; ensuring role definitions align with "minimum necessary" access principles; testing MFA and lockout policies; reviewing logs for unusual activity; and confirming timely updates and deprovisioning of accounts. Incident response plans should also be tested through tabletop exercises and technical drills, such as scenarios involving stolen credentials or compromised provider accounts, to ensure workflows and containment strategies are effective. Audit findings, remediation plans, and follow-up actions must be well-documented to prove ongoing compliance.
Continuous improvement depends on a feedback loop that incorporates risk assessments, incident reports, audit results, regulatory updates, and advancements in technology. Organizations should have a structured process to track changes in HIPAA guidance and related federal policies (like HHS/OCR advisories or new telehealth rules) and evaluate their impact on identity controls. Post-incident reviews should identify root causes of identity-related events, leading to updates in policies, training, and technical measures. Metrics to gauge effectiveness may include the average time to provision or deprovision accounts, the percentage of workforce access aligned with defined roles, the number of orphaned or dormant accounts found during reviews, MFA coverage for systems with ePHI, training completion rates by role, phishing simulation click rates, and confirmed violations tied to credential sharing or unauthorized access.
Conclusion: Maintaining Secure and Compliant Digital Identity
Digital identity controls play a key role in ensuring HIPAA compliance. The Security Rule emphasizes the need for technical safeguards like unique user identification, automatic logoff, and audit controls to protect electronic protected health information (ePHI) effectively[2][3]. By implementing strong authentication measures, role-based permissions, and limiting access to the minimum necessary, healthcare organizations can reduce unauthorized access incidents and simplify internal investigations as well as OCR audits.
These technical safeguards are more than regulatory requirements - they directly impact patient trust. Surveys reveal that while 72% of patients are concerned about how their health data is shared among providers, 84% still want their doctors to have immediate access to complete medical records[8]. This highlights a critical balance: secure identity systems must allow for quick clinical access while protecting patient privacy and security. As Matt Christensen, Sr. Director GRC at Intermountain Health, aptly puts it:
Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare.[1]
Looking forward, identity governance must adapt to evolving technologies and threats. HIPAA’s risk-based approach demands continuous risk analysis, active monitoring, and regular updates to policies and training - not just one-off initiatives. Emerging tools like AI-driven anomaly detection, zero trust architectures, and continuous verification are helping healthcare organizations stay ahead as telehealth, cloud services, and AI-enabled care expand. Platforms such as Censinet RiskOps™ make this ongoing process manageable by enabling healthcare providers to monitor and address identity-related risks across patient data, third-party access, and clinical systems.
To put these insights into action, organizations should prioritize steps like conducting a thorough risk analysis of identity and access systems, extending multi-factor authentication (MFA) to high-risk systems, refining role-based permissions, and scheduling quarterly access reviews. Just as important is fostering a culture where privacy and security are seen as integral to patient safety rather than just regulatory requirements. After all, even the most advanced identity tools can fail if users are not properly informed and engaged.
Ultimately, maintaining a secure and compliant digital identity framework goes beyond avoiding penalties - it’s about earning and sustaining patient trust. Organizations that view identity as a strategic control and consistently balance security with usability will be best positioned to deliver safe, efficient, and patient-focused care well into the future.
FAQs
What are the main technical safeguards under HIPAA for managing digital identity?
HIPAA sets out several technical safeguards to protect digital identities and ensure the security of sensitive patient information. These measures include:
- Access controls: Limiting system access strictly to authorized personnel.
- Audit controls: Keeping a detailed log of system activity to monitor who accesses or uses data.
- Integrity controls: Protecting patient data from being improperly changed or deleted.
- Authentication mechanisms: Confirming the identity of users accessing protected health information (PHI).
These safeguards work together to uphold the confidentiality, accuracy, and accessibility of patient data, while also guarding against unauthorized access or potential breaches.
What does the 'minimum necessary' standard mean for role-based access in healthcare?
The 'minimum necessary' standard is a key principle in healthcare that limits access to patient data strictly to what’s needed for specific job duties. This policy plays a crucial role in reducing unnecessary exposure to sensitive information, ensuring HIPAA compliance, and protecting patient privacy.
By assigning access permissions based on individual roles, healthcare organizations can lower the chances of unauthorized access to protected health information (PHI). At the same time, this approach helps streamline workflows while keeping sensitive data secure.
Why is multi-factor authentication essential for meeting HIPAA requirements?
Multi-factor authentication (MFA) plays a key role in meeting HIPAA compliance standards by bolstering the security of patient data. It requires users to confirm their identity through multiple methods - like entering a password and providing a one-time code. This extra step makes it much harder for unauthorized individuals to gain access to sensitive information.
HIPAA regulations demand strict measures to safeguard protected health information (PHI). By incorporating MFA, healthcare organizations add an additional layer of security, reducing the risk of breaches and ensuring that only authorized personnel can access critical systems and data. Beyond compliance, this approach demonstrates a commitment to protecting patient privacy, reinforcing trust and confidence in the healthcare provider.


