HITECH Act Risk Assessment Frameworks Explained
Post Summary
The HITECH Act, passed in 2009, enforces stricter healthcare data security by mandating risk assessments for electronic protected health information (ePHI). These assessments are essential for HIPAA compliance and focus on identifying risks to ePHI confidentiality, integrity, and availability. Organizations, including healthcare providers, business associates, and subcontractors, must conduct these assessments annually or after major changes, ensuring patient data is safeguarded from threats like ransomware, system misconfigurations, or data breaches.
Key points:
- Who Must Comply: Healthcare providers, business associates (e.g., EHR vendors), and subcontractors handling ePHI.
- Requirements: Risk assessments must cover administrative, physical, and technical safeguards for all systems storing or transmitting ePHI.
- Frameworks: NIST SP 800-30, NIST SP 800-66, and HHS Security Risk Assessment Tool are common methods used.
- Documentation: Detailed records must be maintained for at least six years for audits and compliance checks.
- Common Pitfalls: Outdated assessments, incomplete inventories, and undocumented processes can result in costly penalties.
For long-term compliance, organizations should integrate risk assessments into daily operations, maintain updated documentation, and utilize tools like Censinet RiskOps™ to streamline processes.
HITECH Risk Assessment Requirements and Key Components
Regulatory Requirements for Risk Assessments
Under the HIPAA Security Rule (45 C.F.R. § 164.308(a)(1)(ii)(A)), HITECH requires covered entities and business associates to conduct thorough risk assessments of electronic protected health information (ePHI). These assessments aim to identify risks and implement security measures to reduce them to acceptable levels [7]. HITECH also extends these responsibilities to business associates and introduces stricter enforcement mechanisms.
In cases of unauthorized access or breaches involving unsecured PHI, HITECH mandates a documented risk assessment. This assessment evaluates key factors, such as the nature and extent of the PHI involved, the unauthorized party’s role, the extent of access, and efforts to mitigate risks [4][5]. If the assessment cannot confirm a low likelihood of compromise, the breach is presumed reportable, requiring notification to affected individuals, the Department of Health and Human Services (HHS), and, for incidents impacting 500 or more individuals, prominent media outlets [4][11].
While HITECH doesn’t prescribe a specific risk analysis method, it does require the process to be systematic, well-documented, and repeatable [7][6]. Enforcement by the Office for Civil Rights (OCR) has highlighted failure to conduct an enterprise-wide risk analysis as one of the most frequent and costly violations of HIPAA and HITECH, with penalties often reaching millions of dollars [11][14].
These stringent regulations establish the foundation for what constitutes a compliant risk assessment.
Core Elements of a Risk Assessment
To meet regulatory standards, a risk assessment must address all systems and data flows involving ePHI. This includes electronic health record (EHR) systems, clinical applications, network-connected medical devices, mobile devices, cloud platforms, third-party services, and health information exchanges [2][6]. Organizations need to create a detailed inventory of assets and map out where ePHI is stored, transmitted, and accessed, as well as how it moves across networks, vendors, and environments [2][7][14].
The assessment should evaluate risks across the three safeguard categories outlined in the HIPAA Security Rule: administrative, physical, and technical [2][10][7].
- Administrative safeguards focus on governance, policies, workforce training, incident response, contingency planning, and managing business associates [2][6][13].
- Physical safeguards address facility access controls, workstation/device security, and the handling and disposal of media [13].
- Technical safeguards include access controls, authentication, audit mechanisms, data integrity protections, transmission security (e.g., encryption), and ongoing system monitoring [2][6][13].
The assessment must also identify potential threats (e.g., ransomware, insider misuse, lost devices) and vulnerabilities (e.g., outdated software, weak access controls). Likelihood and impact should be evaluated and documented in a structured risk register [2][6][7]. This documentation should include the asset or process being assessed, identified threats and vulnerabilities, likelihood and impact scores, the inherent risk rating, and existing controls that reduce risk to a residual level [2][6].
How Often to Conduct Risk Reassessments
To stay compliant, organizations must perform regular reassessments. An organization-wide security risk assessment should be conducted annually and after any major changes [2][3][7][14]. Regulators emphasize that risk management is an ongoing process, requiring continuous updates to risk registers and remediation plans as conditions evolve [2][6].
Certain events should trigger focused reassessments, such as significant system changes, the addition of network-connected devices, cloud migrations, vendor integrations, or security incidents [2][5][6]. These changes can significantly alter an organization’s risk profile, necessitating updates to risk analysis and documentation to reflect new assets, data flows, and controls [2][6].
Organizations are expected to maintain detailed documentation for at least six years. This includes risk analysis methodologies, results, mitigation plans, incident logs, and breach assessments. Such records are essential for demonstrating due diligence during OCR audits and serve as evidence that the organization’s risk management practices are thorough and informed by the assessment’s findings [2][9][4][7].
Frameworks and Methods for HITECH-Compliant Risk Assessments
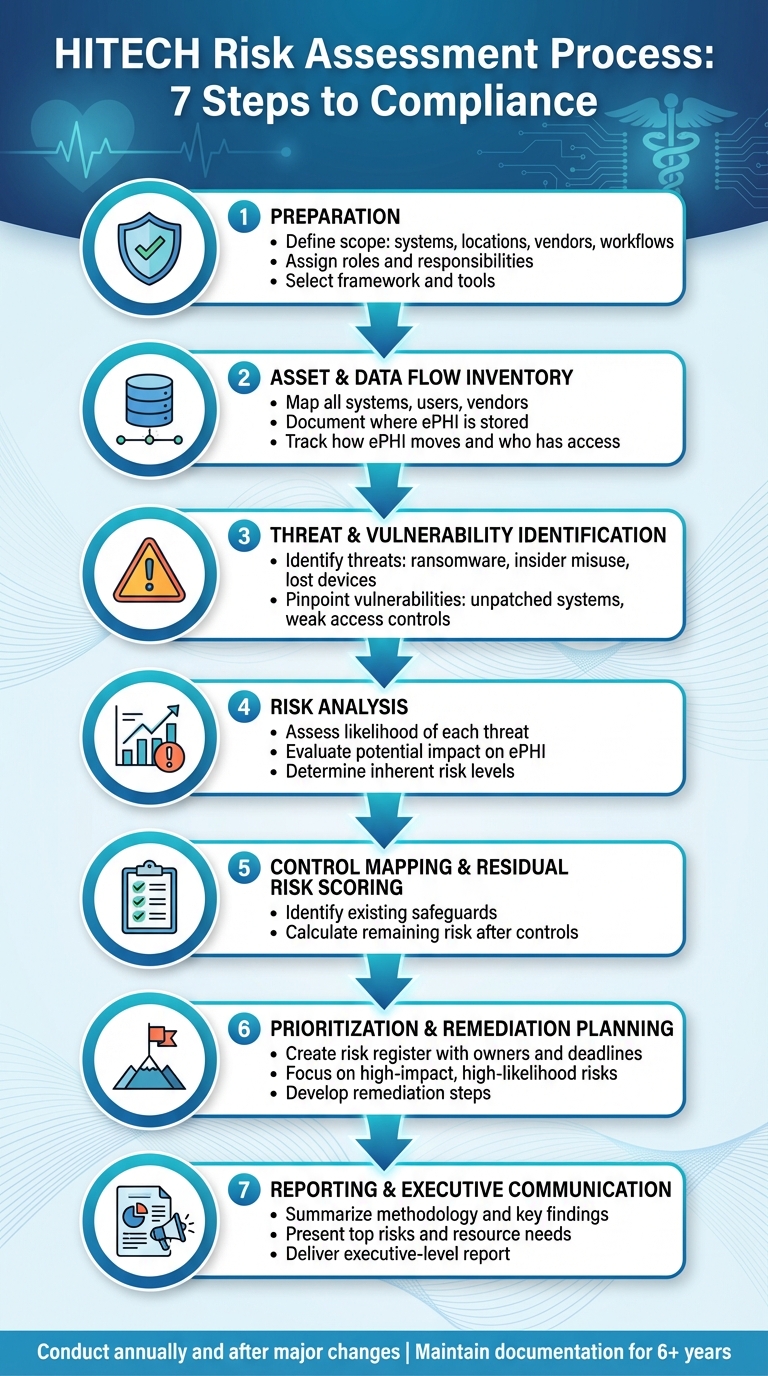
7-Step HITECH Risk Assessment Process for Healthcare Organizations
Common Risk Assessment Frameworks
The HITECH Act emphasizes the need for a systematic, well-documented, and repeatable approach to assessing risks and vulnerabilities associated with electronic protected health information (ePHI) [6][7]. To meet these requirements, the Department of Health and Human Services (HHS) points to NIST frameworks as reliable options for fulfilling both HIPAA and HITECH obligations. Commonly used frameworks in the U.S. healthcare sector include:
- NIST SP 800-30: A guide for conducting risk assessments.
- NIST SP 800-37: A comprehensive Risk Management Framework.
- NIST SP 800-66 Rev. 2: A resource that aligns NIST activities with the HIPAA Security Rule's administrative, physical, and technical safeguards [6][7].
Healthcare organizations often turn to the NIST Cybersecurity Framework, which is organized around five core functions: Identify, Protect, Detect, Respond, and Recover. This structure helps align risk management efforts with HIPAA requirements. For smaller providers, the HHS Security Risk Assessment (SRA) Tool serves as a practical checklist [12]. Additionally, the 2022 update to NIST SP 800-66 Rev. 2 underscores the importance of integrating HIPAA and HITECH risk analysis into a broader enterprise risk management (ERM) strategy [6].
These frameworks lay the groundwork for a structured process, which is outlined in the following steps.
Risk Assessment Process: Step-by-Step
Using these established frameworks, healthcare organizations can follow a clear process to assess risks to ePHI:
- Preparation: Define the scope of the assessment, including systems, locations, vendors, and workflows involving ePHI. Assign roles and select the appropriate framework and tools [7][12].
- Asset and Data Flow Inventory: Map out all systems, users, vendors, and data flows. This includes documenting where ePHI is stored, how it moves, and who has access, covering everything from cloud services to mobile devices and medical equipment [2].
- Threat and Vulnerability Identification: Pinpoint potential threats (e.g., ransomware, insider misuse, lost devices) and vulnerabilities (e.g., unpatched systems, weak access controls) for each asset and workflow [5][7].
- Risk Analysis: Assess the likelihood and potential impact of each threat exploiting a vulnerability. This helps determine the inherent risk to the confidentiality, integrity, and availability of ePHI [5][7].
- Control Mapping and Residual Risk Scoring: Identify existing safeguards for each risk and calculate the remaining risk after applying these controls [2][8].
- Prioritization and Remediation Planning: Develop a risk register that assigns ownership, deadlines, and remediation steps, focusing on risks with high impact and likelihood [2][8].
- Reporting and Executive Communication: Summarize the methodology, key findings, top risks, and resource needs in an executive-level report [2][5].
Risk Analysis vs. Risk Management vs. Breach Risk Assessment
To meet compliance requirements, it’s important to distinguish between Risk Analysis, Risk Management, and Breach Risk Assessment. While these processes are interconnected, each serves a unique purpose.
- Risk Analysis: This is a point-in-time evaluation required by the HIPAA Security Rule to identify risks and vulnerabilities to ePHI. The outputs typically include a documented process, an inventory of assets, threat and vulnerability lists, likelihood and impact ratings, and a prioritized risk register [2][5].
- Risk Management: Unlike risk analysis, this is an ongoing effort to implement and monitor security measures that mitigate identified risks. It involves updating policies, tracking control effectiveness, and revisiting assessments when operational or technological changes occur. Typical outputs include a risk management plan, remediation projects with timelines, updated procedures, and evidence of continuous monitoring [2][5][8][13].
- Breach Risk Assessment: Triggered by incidents like unauthorized access, this assessment determines whether there’s a low probability that PHI has been compromised. It evaluates factors such as the nature of the PHI involved, whether it was accessed or acquired, and the extent of mitigation efforts. The outcome is a documented decision on whether breach notifications are necessary, including communication with individuals, HHS, and possibly the media [2][4][5].
| Aspect | Risk Analysis | Risk Management | Breach Risk Assessment |
|---|---|---|---|
| Primary Purpose | Identify and evaluate risks and vulnerabilities to ePHI | Implement safeguards to reduce risks to acceptable levels | Determine if an incident qualifies as a reportable breach under HITECH |
| Timing | Conducted initially, annually, or after significant changes | Continuous process, revisited after each risk analysis cycle | Triggered by suspected or confirmed incidents involving PHI |
| Scope | Organization-wide: systems, processes, vendors, and data flows | Focused on mitigating identified risks with prioritized controls | Specific to individual incidents or related sets of incidents |
| Methods/Frameworks | NIST SP 800-30, NIST SP 800-66, OCR SRA Tool, HIPAA Security Rule crosswalks | NIST RMF, NIST CSF, internal risk registers, and governance processes | HHS four-factor test: nature of PHI, unauthorized access, acquisition, and mitigation |
| Typical Outputs | Asset inventory, threat/vulnerability listings, risk ratings, and methods | Risk register, remediation plan, control roadmap, and monitoring metrics | Incident documentation, four-factor analysis, and breach notification decisions |
How to Implement Risk Assessments in Healthcare Organizations
Steps to Implement Risk Assessments
To establish a risk assessment program aligned with HITECH, healthcare organizations need to start with clear security governance. This means appointing a Security Officer, defining decision-making roles, and creating a standing compliance or risk committee. This committee typically includes representatives from IT, security, privacy, compliance, legal, clinical operations, and the supply chain. The first step is to define the scope of the assessment, identifying which facilities, systems, workflows, and third parties handle electronic protected health information (ePHI). It’s also crucial to clarify whether the program will include both organization-wide security risk analysis and individual breach risk assessments.
Next, plan resources by assigning stakeholders, determining budgets, and selecting tools for conducting and documenting assessments. Smaller providers can use free tools like the HHS Security Risk Assessment (SRA) Tool to get started. With governance and scope set, the organization must create a comprehensive inventory of systems, users, vendors, and data flows that involve ePHI. This inventory typically includes electronic health records (EHRs), billing systems, imaging and lab systems, cloud applications, mobile devices, medical devices, on-premises servers, and remote access tools. Each item should detail where ePHI is stored, how it moves (e.g., through interfaces, APIs, or file transfers), and who has access.
For each system and workflow, identify potential threats like ransomware, insider misuse, or lost devices, and evaluate the likelihood and impact of these risks on ePHI. Document existing administrative, physical, and technical safeguards to determine the residual risk after controls are applied. The results are compiled in a risk register that includes risk descriptions, owners, current safeguards, residual risk ratings, recommended actions, deadlines, and statuses. From there, organizations can prioritize actions based on the severity of the risk, cost, and feasibility, implementing improvements through updated policies, new technologies, training, and continuous monitoring.
To ensure risk assessment becomes an ongoing part of operations rather than a one-time task, it should be embedded into key processes. For example, change management should include a risk analysis before approving new systems, major upgrades, integrations, or cloud migrations. This ensures the risk register and system inventory remain current. Similarly, procurement and contracting processes should incorporate security questionnaires, Business Associate Agreement (BAA) reviews, and risk scoring to evaluate vendors before engagement. Finally, any impermissible use or disclosure of PHI requires a breach risk assessment in line with the HIPAA Breach Notification Rule to determine if there’s a low probability of PHI compromise or if notifications are necessary.
Specialized platforms can simplify and streamline these processes, making risk management more efficient.
Using Censinet RiskOps™ to Simplify Risk Management
Advanced platforms like Censinet RiskOps™ can transform manual risk management processes into streamlined, automated workflows. This AI-powered platform is specifically designed for healthcare organizations, operating on a collaborative network that connects over 50,000 vendors and products across the industry [1]. It enables healthcare delivery organizations (HDOs) to securely share cybersecurity and risk data with third-party vendors.
The platform automates key workflows, reduces manual effort, and centralizes risk management documentation. For example, Terry Grogan, CISO at Tower Health, shared that using Censinet RiskOps™ allowed 3 full-time employees to return to their primary roles while enabling the organization to conduct more risk assessments with just 2 staff members. Matt Christensen, Sr. Director GRC at Intermountain Health, highlighted the importance of tools built specifically for healthcare’s complexity, while James Case, VP & CISO at Baptist Health, noted the elimination of spreadsheets and the collaborative value of engaging with the broader hospital community.
Censinet AI™ further accelerates third-party risk assessments by allowing vendors to complete security questionnaires in seconds. It automatically summarizes vendor evidence, captures product integration details, identifies fourth-party risk exposures, and generates risk summary reports. Additionally, the platform supports cybersecurity benchmarking, helping organizations measure their programs against industry standards and advocate for necessary resources.
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." – Brian Sterud, CIO at Faith Regional Health
HITECH Risk Assessment Use Cases
Applying these risk assessment strategies can address a variety of healthcare scenarios:
- Core EHR and clinical systems: Evaluate access controls, encryption, and logging to ensure compliance with HIPAA Security Rule requirements.
- Telehealth expansion: Assess video platforms, patient portals, and home-monitoring devices for secure ePHI transmission and proper identity verification.
- Cloud migration: Review shared-responsibility models, encryption key management, identity controls, and cross-border data flows to ensure compliance with HIPAA/HITECH guidelines.
- Medical device connectivity: Examine network-enabled devices like infusion pumps and imaging equipment for proper network segmentation, timely patching, and vendor support.
- Third-party vendor assessments: Maintain a register of business associates and subcontractors handling ePHI, ensuring signed BAAs and evaluating vendor controls with standardized security questionnaires.
- Post-incident breach risk assessments: Use the HHS four-factor test to evaluate breaches and determine if PHI compromise requires notification.
These strategies ensure healthcare organizations can manage risks effectively while maintaining compliance with industry standards and regulations.
sbb-itb-535baee
Governance, Documentation, and Common Mistakes to Avoid
Building Governance for Ongoing Compliance
Achieving and maintaining HITECH compliance requires a structured governance framework. Start by appointing a dedicated Security Officer tasked with overseeing risk management activities. In some cases, you may also need a separate Privacy Officer to manage policies related to the use and disclosure of PHI. These roles should come with clearly documented job descriptions outlining responsibilities, such as conducting risk analyses, maintaining risk registers, and presenting findings to leadership.
A cross-functional compliance or security committee is essential for ongoing oversight. This committee should meet quarterly and include representatives from IT security, privacy, compliance, legal, and clinical operations. Their agenda should cover the organization's risk posture, trends in incidents, vendor risks, progress on remediation, and funding requirements. Documenting these meetings is crucial to show regulators that decisions are deliberate and tied to both business and patient-safety considerations. Clearly establish decision-making authority for issues like risk acceptance, remediation approval, and breach escalation.
Assign specific risk owners who are accountable for assessments, controls, and audit evidence. Tools like RACI matrices (Responsible, Accountable, Consulted, Informed) can help clarify roles. For instance, they can define who conducts technical risk analyses, consolidates findings into the risk register, ensures documentation meets regulatory standards, and reviews risks that could affect patient safety, such as EHR outages or vulnerabilities in medical devices.
Strong governance naturally leads to consistent documentation practices, which are explored in the next section.
Documentation Requirements for Audits
Healthcare organizations must maintain a centralized repository for all compliance-related documentation. HIPAA mandates that covered entities and business associates retain required records for at least six years from the date of creation or the last effective date, whichever is later. During audits, regulators typically request several key documents, including:
- Comprehensive risk analysis reports detailing all ePHI assets, threats, vulnerabilities, likelihood and impact ratings, and residual risk levels.
- A current risk register that lists risk owners, due dates, and remediation statuses.
- Written risk management plans outlining how identified risks are being addressed.
Additional evidence often requested includes policies and procedures aligned with HIPAA Security Rule standards, signed Business Associate Agreements (BAAs) with vendors handling PHI, incident and breach logs, formal breach risk assessments under the HITECH Breach Notification Rule, workforce training records, access reviews, change-management logs, contingency plan tests, and backup/restore test results. Make sure all documents are date-stamped and include clear authorship and approval records. This level of detail allows organizations to demonstrate what controls were in place at any given time, even if an investigation looks back several years.
For every unauthorized use or disclosure of unsecured PHI, organizations must conduct and document a breach risk assessment. This evaluation should cover the type and amount of PHI involved, the identity of the unauthorized recipient, whether the PHI was accessed or acquired, and the extent of any mitigation efforts. If the analysis cannot demonstrate a low probability of compromise, notification is required unless a specific regulatory exception applies. Ensure these assessments are detailed, written, and include decision workflows, timestamps, containment actions, legal reviews, and final determinations about notifications to individuals, HHS, and potentially the media within the 60-day federal timeline.
Common Mistakes and How to Avoid Them
Even with strong governance and documentation practices, organizations often make errors that can lead to non-compliance. Recent enforcement actions by the OCR highlight the dangers of one-time assessments and incomplete documentation. One of the most frequent - and costly - violations is the failure to conduct an enterprise-wide risk analysis, which has resulted in penalties running into millions of dollars.
Below is a comparison of common mistakes and their solutions:
| Common Mistake | Why It's a Problem | Best-Practice Approach |
|---|---|---|
| Conducting a one-time risk assessment and not updating it | Outdated controls fail to address new systems or threats, leading to compliance gaps | Treat risk analysis as an ongoing process: update it annually and after major changes; revise risk registers and plans promptly |
| Focusing only on EHR systems and ignoring other ePHI sources | Leaves critical systems, cloud apps, medical devices, and vendors unassessed | Perform a comprehensive inventory that includes all ePHI sources, vendors, and mobile/cloud environments |
| Using undocumented or informal methodologies | Makes it difficult to defend findings during audits | Adopt a formal, repeatable methodology (e.g., NIST 800-30/800-66) and include assumptions, criteria, and scoring in reports |
| Identifying risks but not tracking remediation | Known risks remain unaddressed, increasing vulnerability and non-compliance | Maintain a risk register with assigned owners, deadlines, remediation steps, and evidence of completion; review progress in committee meetings |
| Minimal or missing documentation of breach risk assessments | Increases regulatory scrutiny and makes it harder to prove low probability of compromise | Always perform and document the HITECH four-factor analysis with detailed narratives and supporting evidence, not just numeric scoring |
To avoid these pitfalls, organizations should consider conducting internal or third-party "mock audits" to test their ability to retrieve specific documents quickly. Embedding documentation requirements into change-management processes - ensuring that every new system or vendor undergoes a risk assessment, has a signed BAA, and an updated data flow map - can also minimize surprises during audits. Platforms like Censinet RiskOps™ can streamline risk management documentation, automating workflows to ensure audit readiness while reducing manual workloads.
Conclusion
HITECH-compliant risk assessments aren’t just a regulatory checkbox - they’re legally required, operationally critical, and key to safeguarding patient data. The HIPAA Security Rule, strengthened by HITECH, requires an "accurate and thorough" evaluation of risks to electronic protected health information (ePHI). Regulatory actions often highlight the lack of enterprise-wide risk assessments as a frequent and costly violation. Beyond meeting compliance, thorough risk assessments help minimize the likelihood and impact of breaches, ensure system reliability, and build trust with patients, partners, and oversight agencies.
If you're looking to get started within the next 30–90 days, here’s what to focus on:
- Create or update a full inventory of systems, users, vendors, and data flows interacting with ePHI.
- Conduct a documented enterprise-wide security risk assessment that evaluates administrative, physical, and technical safeguards. Use NIST-based approaches or tools like the HealthIT.gov Security Risk Assessment Tool.
- Turn your findings into an actionable risk management plan with clear priorities, deadlines, assigned owners, and regular governance meetings to track progress and keep leadership engaged.
These initial steps set the stage for building a sustainable, long-term approach to risk management.
For long-term success, risk assessments should be integrated into the organization’s ongoing operations. This means triggering reviews during key events like system upgrades, cloud migrations, vendor onboarding, or major workflow changes. Aligning with frameworks such as NIST guidance ensures assessments are structured and repeatable - qualities regulators look for. Detailed documentation should clearly show how risks were identified, assessed, and addressed, meeting HITECH’s standards for protecting ePHI.
To simplify and scale these efforts, advanced tools are available. For example, Censinet RiskOps™ offers an AI-powered platform built specifically for healthcare. It centralizes risk assessments for third parties and internal operations, automates workflows, and supports continuous monitoring across vendors, medical devices, and clinical systems. Healthcare organizations using this platform report significant time savings, the ability to complete more assessments with fewer resources, and improved collaboration through a shared network of hospitals. By automating manual processes and maintaining audit-ready documentation, organizations can transform compliance from a challenge into a strategic advantage.
Make risk assessments a core part of your operations, ensure strong governance and documentation, and explore specialized tools to streamline compliance. With the right strategy, tools, and dedication, your organization can meet HITECH requirements, reduce risks, and uphold the trust of the patients you serve.
FAQs
What’s the difference between risk analysis, risk management, and breach risk assessment under the HITECH Act?
Under the HITECH Act, risk analysis is all about pinpointing weaknesses and identifying potential threats to protected health information (PHI). By doing this, healthcare organizations can get a clear picture of where their data might be exposed to risks.
Risk management takes this a step further by focusing on actionable solutions. It’s about putting safeguards in place to protect PHI and making sure all security standards are met to stay compliant.
Meanwhile, a breach risk assessment looks at the likelihood and potential impact of a data breach. This process helps organizations gauge the seriousness of possible incidents, plan effective responses, and minimize damage while ensuring a fast recovery.
What’s the best way for healthcare organizations to integrate risk assessments into their daily operations?
Healthcare organizations can seamlessly incorporate risk assessments into their daily workflows with tools like Censinet RiskOps™, a platform tailored for healthcare risk management. These advanced systems offer features like continuous monitoring, automation of routine assessments, and simplified workflows, all designed to minimize interruptions to everyday operations.
By integrating risk assessments into current clinical and operational processes, organizations can better manage risks related to patient data, medical devices, and supply chains. Allocating resources based on industry standards and cultivating a proactive approach to risk management also boosts efficiency and strengthens cybersecurity defenses.
What are the key pitfalls to avoid during HITECH-compliant risk assessments?
When performing risk assessments under HITECH guidelines, there are a few pitfalls that healthcare organizations should be mindful of. One common mistake is using a one-size-fits-all approach instead of tailoring the assessment to the specific needs of the organization. Another is relying on outdated tools, like spreadsheets, which can be cumbersome and prone to errors. Neglecting to maintain continuous risk monitoring is another oversight that can leave vulnerabilities unchecked.
A comprehensive assessment also requires input from all relevant stakeholders. Skipping this step can result in incomplete evaluations, leaving critical gaps. Similarly, failing to document processes thoroughly or disregarding established industry standards can lead to compliance issues that are easily avoidable.
Taking a detailed, collaborative, and forward-thinking approach not only helps meet HITECH requirements but also strengthens the protection of sensitive patient information and systems.


