Top 7 Incident Response Templates for Healthcare
Post Summary
In healthcare, incident response templates are essential for managing cybersecurity threats like ransomware, EHR outages, and data breaches. These templates provide structured steps to protect patient care, ensure compliance with regulations like HIPAA, and reduce financial and operational risks. Here's a quick overview of the top options:
- CHIRP: Tailored for U.S. hospitals, integrates clinical workflows with emergency management.
- NIH Template: Focuses on system ownership and detailed documentation for large healthcare organizations.
- HICCouncil Guidance: Combines cybersecurity best practices with patient safety measures.
- CISA Template: A general framework requiring healthcare-specific adjustments, based on NIST standards.
- NIST Framework: A detailed, sector-neutral guide adaptable to healthcare needs.
- General-Purpose Templates: Basic structures that can be modified for clinical operations.
- Censinet RiskOps: A digital platform offering live workflows for healthcare-specific incident management.
Each template addresses the incident lifecycle - preparation, detection, containment, recovery, and post-incident review - but varies in focus and complexity. Choose one that aligns with your organization's size, systems, and compliance needs. Regular updates and training ensure your plan stays effective.
1. Coordinated Healthcare Incident Response Plan (CHIRP)
Framework Alignment
The Coordinated Healthcare Incident Response Plan (CHIRP), developed by the Healthcare and Public Health Sector Coordinating Councils, works seamlessly with existing frameworks. It aligns with the NIST incident response lifecycle while integrating into established healthcare emergency management systems like the Hospital Incident Command System (HICS) [3][7]. For U.S. hospitals, CHIRP fits naturally alongside NIST-based cybersecurity policies, HIPAA Security Rule requirements, and downtime procedures. This compatibility allows hospitals to adopt CHIRP without having to make major changes to their governance structures, making it a practical addition to healthcare-specific protocols.
Healthcare-Specific Features
Unlike generic IT-focused templates, CHIRP directly addresses the unique challenges of healthcare environments. It connects cyber incidents to real-world clinical issues, such as managing diversion status, handling delayed procedures, or switching to manual documentation workflows. These are the kinds of patient care concerns that are front and center during healthcare incidents. CHIRP includes sample language and planning prompts designed specifically for healthcare delivery organizations. It also provides guidance for coordinating responses across clinical leadership, emergency management teams, and executive staff [3][7].
Incident Lifecycle Coverage
CHIRP guides organizations through every phase of an incident’s lifecycle. This includes preparation (like governance, role assignments, training, and exercises), detection and assessment (with a focus on clinical impacts and patient safety), response and coordination (activating command structures and linking to business continuity plans), recovery (prioritizing systems critical to safe patient care), and post-incident activities such as debriefs and after-action reviews. These steps not only support HIPAA compliance but also ensure continuity of care. CHIRP also emphasizes the importance of validation exercises, such as tabletop scenarios and simulations, to strengthen response capabilities [3][7].
Practical Usability
CHIRP serves as a flexible reference template that requires customization before implementation. For a mid-size U.S. hospital without a well-developed incident response plan, CHIRP can be adapted by maintaining its overall structure while tailoring the sample language to fit local practices. It can also be aligned with specific systems, such as EHRs, clinical applications, and emergency management protocols. To ensure operational readiness, hospitals should supplement CHIRP with technical guidelines (like NIST SP 800-61), inventories, contact lists, and clearly defined escalation thresholds. This approach ensures the plan is tailored to the specific needs and demands of U.S. healthcare settings [3][7].
2. National Institutes of Health Cybersecurity Incident Response Plan Template
Framework Alignment
The NIH Cybersecurity Incident Response Plan template is built around the key components outlined in NIST SP 800-61. These include system ownership, incident detection and analysis, containment, eradication and recovery, and post-incident activities [4][6]. While it provides a solid foundation across these phases, U.S. healthcare organizations may need to enhance the template with specific workflows for breach notifications, such as informing the HHS OCR and notifying affected patients, to meet HIPAA requirements [6]. Its structured yet flexible approach makes it a useful starting point for healthcare organizations with diverse needs.
Healthcare-Specific Features
The template is tailored to the unique challenges of the healthcare sector. It emphasizes detailed documentation of systems and system ownership, which is crucial for managing electronic health records (EHRs), clinical applications, research databases, and other regulated data [6]. By identifying which systems store protected health information (PHI) and assigning responsible parties, the template helps prioritize incidents that could disrupt patient care. It’s particularly well-suited for large healthcare environments, addressing scenarios like compromised lab accounts, attacks on clinical systems, or breaches involving both patient and research data [6].
Incident Lifecycle Coverage
The NIH template addresses every stage of the incident response lifecycle with a moderate level of detail. It starts with identifying systems and assigning responsibilities, followed by clear steps for detection, analysis, containment, eradication, and recovery [4][6]. A post-incident review process ensures that lessons are documented and applied to improve future responses [4][6].
Practical Usability
The template’s level of detail makes it a good fit for large academic centers and research hospitals, while smaller facilities can adapt it to their needs [6]. Its focus on system ownership aligns well with the complexity of larger institutions, but smaller clinics may prefer a simplified version for easier implementation [6]. Many organizations use the NIH template as a reference, integrating its structure, role definitions, and lifecycle steps into their own plans. Additionally, the template is available as a downloadable Word document, making customization straightforward. Organizations can easily add their own agency names, contacts, and specific procedures [6][8].
3. Health Industry Coordinating Council (HICCouncil) Healthcare Cybersecurity Guidance and Templates
Framework Alignment
The HIC Council guidance builds on established frameworks to address the unique risks faced by the healthcare sector. As part of the Health Sector Coordinating Council (HSCC), the Health Industry Cybersecurity (HIC) Council brings together health systems, medical device manufacturers, IT vendors, and government agencies in a public-private partnership. This guidance aligns with key standards like NIST CSF, NIST SP 800-61, and the HIPAA Security Rule, providing U.S. healthcare providers with tools to demonstrate compliance during audits. By mapping incident response procedures to these established security practices, the guidance helps organizations meet HIPAA requirements for incident handling, reporting, and documentation. It includes role definitions, escalation paths, and checklists specifically designed to safeguard sensitive health information, ensuring the guidance aligns with clinical priorities.
Healthcare-Specific Features
Unlike general IT incident response plans, the HIC Council guidance focuses on patient safety and the uninterrupted delivery of care. The templates include healthcare-specific elements, such as workflows for managing electronic health record (EHR) downtime, addressing medical device connectivity issues, and maintaining clinical communication systems. These features reflect the operational realities of healthcare environments. The guidance also incorporates role structures that align with hospital incident command systems or clinical leadership hierarchies. It emphasizes coordination with public health authorities, regulators, and external partners, recognizing that cyber incidents can quickly escalate into safety-critical situations for patients.
Incident Lifecycle Coverage
The templates provide comprehensive coverage of the incident lifecycle, from preparation to post-incident review. During the preparation phase, the guidance encourages integrating cybersecurity planning with existing emergency management and business continuity strategies. Detection criteria are clearly defined to help identify incidents early, while containment procedures outline steps for activating downtime protocols. Recovery sections guide decisions on taking clinical systems offline and restoring services, ensuring data integrity is verified. After incidents, the guidance stresses the importance of conducting after-action reviews, capturing lessons learned, and updating response plans in alignment with NIST recommendations.
Practical Usability
Designed with flexibility in mind, the guidance can be tailored to fit organizations of varying sizes. Larger health systems can align template roles with their existing security operations, privacy offices, and emergency management teams, while adding detailed playbooks for specific technologies or multi-site coordination. Smaller organizations, such as community hospitals and physician groups, can simplify governance layers by combining roles - for instance, having a CIO double as the incident commander. Tools like role matrices and communication checklists can be seamlessly integrated into incident response plans. Call trees can be customized to match local on-call schedules, and job titles can be adjusted to suit smaller clinical settings. Additionally, platforms like Censinet RiskOps™ enhance this guidance by embedding templates, role structures, and incident data elements into digital workflows. This streamlines tasks like evidence collection, remediation tracking, and managing third-party risks when vendors or cloud services are involved. These adaptable tools strengthen incident response efforts and complement the detailed documentation provided in later sections.
4. CISA Cybersecurity Incident Response Plan Template and Basics
Framework Alignment
The Cybersecurity and Infrastructure Security Agency (CISA) provides a Cyber Incident Response Plan (CIRP) template designed to help U.S. organizations manage incidents effectively at every stage - before, during, and after they occur. This template aligns with NIST SP 800-61 and ties directly to the NIST Cybersecurity Framework's core functions: Identify, Protect, Detect, Respond, and Recover [3][4]. For organizations undergoing audits or regulatory reviews, this built-in mapping to recognized standards serves as a solid foundation. Additionally, the template integrates best practices from the CIS Critical Security Controls, addressing areas like asset management, logging, and incident handling. These elements not only strengthen technical security but also support compliance requirements [3]. Each phase of the incident lifecycle is clearly outlined within the template, ensuring a structured and comprehensive approach.
Incident Lifecycle Coverage
CISA's template thoroughly addresses the key stages of incident management: preparation, detection and analysis, containment, eradication and recovery, and post-incident activities [3][4]. Preparation focuses on policies, tools, and training, while detection and analysis include logging, triage, and categorization. Containment and recovery involve technical response actions, and post-incident activities emphasize lessons learned and documentation.
For healthcare organizations, this lifecycle must extend to cover clinical systems and medical devices. For example, detection and triage should account for scenarios such as electronic health record (EHR) outages, PACS (Picture Archiving and Communication System) compromises, or ransomware affecting patient care. Containment and recovery plans need to align with hospital incident command systems and downtime protocols, ensuring patient safety remains the top priority [5][7]. The template also suggests maintaining separate but interconnected documents: a high-level plan for governance, detailed technical playbooks for incident types like ransomware or data theft, and communication resources such as contact lists and notification templates. This layered approach provides a strong foundation for tailoring the lifecycle to healthcare-specific needs.
Healthcare-Specific Adaptations
To make the CISA template more relevant for healthcare, organizations should integrate requirements from the HIPAA Security Rule (§164.308(a)(6)) regarding the detection, reporting, and response to incidents involving protected health information (PHI) [3]. Additional sections should address whether electronic PHI (ePHI) or PHI is involved, include decision trees for determining if an incident qualifies as a reportable breach, and outline workflows and timelines for HIPAA/HITECH notifications to affected individuals, the Office for Civil Rights (OCR), or state attorneys general, if necessary.
Healthcare-specific adaptations should also define incident categories and severity levels based on clinical impact and assign roles to appropriate stakeholders. For instance:
- The Chief Information Security Officer (CISO) or security director could act as the incident commander.
- The Chief Information Officer (CIO) would oversee technology coordination.
- Privacy officers and compliance teams would handle PHI assessments.
- Clinical leadership, such as the chief medical officer or nursing staff, would evaluate patient care impacts [3][5][7].
Practical Usability
CISA prioritizes usability by including concise checklists, well-defined roles, and actionable workflows [3][4]. For mid-sized healthcare organizations, a practical starting point is adopting the template's core framework and gradually building out detailed playbooks for high-priority risks like ransomware, PHI exfiltration, business email compromise, vendor outages, or medical device vulnerabilities [3][6][7]. Frontline staff can work with simpler checklist-based formats, while the full CIRP remains available for the incident response team and leadership.
Annual tabletop exercises are another key recommendation, ensuring executive leadership and operational teams are prepared [3][4]. Tools like Censinet RiskOps™ can further enhance the template's usability by centralizing key elements like incident documentation, evidence collection, and task workflows. These platforms can also link incidents to specific vendors, medical devices, or clinical applications, feeding insights from post-incident reviews back into risk management and remediation plans [3]. This approach helps healthcare organizations streamline documentation, improve collaboration, and maintain a cycle of continuous improvement while managing complex risks tied to third-party and enterprise-level operations.
5. NIST Incident Response Plan Structure and Sample Templates

Framework Alignment
The National Institute of Standards and Technology (NIST) lays out a detailed standard for incident response planning in its Computer Security Incident Handling Guide (SP 800-61 Rev. 2). This 79-page guide introduces a four-phase structure: Preparation, Detection & Analysis, Containment, Eradication, and Recovery, and Post-Incident Activity. These phases form the foundation for many incident response templates used across U.S. healthcare organizations. They also align seamlessly with the NIST Cybersecurity Framework's core functions: Identify, Protect, Detect, Respond, and Recover [4]. This alignment not only simplifies integration with existing controls but also provides a clear, defensible audit trail - helpful for demonstrating due diligence during audits. By adopting this standardized framework, organizations can easily customize it to meet the unique demands of healthcare environments.
Incident Lifecycle Coverage and Healthcare Adaptations
NIST-based templates are designed to address the entire lifecycle of an incident through their four phases. Here's how they break down:
- Preparation: Establishing policies, tools, and training programs to ensure readiness.
- Detection & Analysis: Logging incidents, triaging events, and categorizing incidents based on severity.
- Containment, Eradication, and Recovery: Outlining technical steps to mitigate and resolve incidents.
- Post-Incident Activity: Focusing on lessons learned and detailed documentation requirements [4].
Healthcare organizations often adapt these phases to suit clinical realities. For example, preparation might include tabletop exercises simulating scenarios like electronic health record (EHR) downtime or patient diversion. During detection and analysis, clinical impact assessments become crucial - evaluating whether delays in lab results or imaging access could harm patients. In post-incident reviews, healthcare teams should examine any patient safety incidents or near-misses, ensuring their response plan aligns with the unique demands of patient care.
Healthcare-Specific Structural Components
While NIST's guidance is designed to be sector-neutral, healthcare organizations need to tailor their incident response plans to address their specialized needs. A well-rounded plan should include governance, roles, incident classification, detailed procedures, documentation, and coordination [4]. In healthcare settings, this means:
- Governance: Explicitly addressing EHR systems, medical devices, clinical applications, and third-party vendors managing protected health information (PHI).
- Roles and Responsibilities: Expanding beyond IT security to include clinical leaders like the chief nursing officer, compliance and privacy officers, and biomedical engineering teams.
- Incident Classification: Tying severity levels to patient safety and care disruption, rather than focusing solely on data loss.
- Documentation: Ensuring compliance with HIPAA breach notification thresholds and timelines.
- Coordination Protocols: Establishing clear processes for working with entities such as the HHS Office for Civil Rights, law enforcement, and state health departments.
Practical Usability
While NIST-based templates provide a comprehensive and structured approach, their depth can sometimes overwhelm busy clinical leaders and small IT teams. To address this, many organizations use a layered approach: maintaining a full NIST-aligned plan as a master reference, while creating quick-reference guides or one-page flowcharts for common scenarios. These simplified tools make it easier for healthcare teams to respond effectively during high-pressure situations.
Healthcare teams should prioritize addressing high-impact clinical threats, such as EHR downtime or ransomware attacks, and integrate these scenarios into training sessions and emergency drills. Additionally, platforms like Censinet RiskOps™ can embed NIST workflows into daily operations, minimizing the need to manually navigate lengthy documents during an actual incident. This approach ensures that even in the chaos of an incident, healthcare organizations can act swiftly and effectively.
sbb-itb-535baee
6. General-Purpose Incident Response Plan Templates for Healthcare Use
Framework Alignment
General-purpose incident response templates with modular structures can be tailored to meet the needs of healthcare organizations, especially when aligned with established standards. For example, the State of Michigan incident response template organizes its plan into key phases: preparation, incident detection and analysis, threat containment, eradication, and recovery, and post-incident activities [4]. These phases align seamlessly with healthcare workflows, such as clinical help desk operations, EHR downtime protocols, and on-call rotations. Similarly, the California Department of Technology provides a straightforward 17-step basic incident response procedure, which includes references to more detailed plans for specific incident types like system failures, malware, and intrusions [4]. Healthcare organizations can adapt these templates to address scenarios unique to their field, such as ransomware targeting EHRs, compromised medical devices, or network outages that disrupt patient care.
Healthcare-Specific Adaptability
While general-purpose templates offer a solid starting point, they often lack the depth needed for healthcare-specific challenges. A standout example is the PRIMA Incident Response Plan template, which explicitly identifies medical and health insurance information as sensitive data categories [2]. This makes it easier to modify for HIPAA-regulated environments. However, most generic templates require significant adjustments to meet healthcare's regulatory and operational demands. Customization should include sections for PHI exposure, HIPAA breach evaluation steps, clinical safety checks, and coordination with hospital incident command systems. Playbooks tailored for healthcare scenarios - like EHR ransomware attacks, lost devices containing PHI, or medical device security breaches - are essential. By incorporating steps for PHI handling and clinical safety protocols, these templates can better support patient care priorities.
Incident Lifecycle Coverage
Effective templates address every stage of the incident lifecycle, from initial detection to resolution. For instance, the Federal Select Agent Program template includes a tabular incident-type matrix with detailed procedures for medical and emergency scenarios [8]. This structured approach can guide healthcare organizations in creating runbooks for various cyber and safety incidents. Key elements like incident timing, detection methods, responsible personnel, and evidence documentation are invaluable for HIPAA investigations and reporting to the Office for Civil Rights [2][8].
Practical Usability
In high-pressure situations, usability is just as important as structure. Short, concise plans - ranging from 4 to 14 pages - with clear layouts are easier for teams to follow during emergencies [4]. Templates that include incident forms, logs, and step-by-step checklists help reduce cognitive overload and ensure consistent responses [2][4][8]. For healthcare organizations, it’s crucial to select templates with clear role definitions, such as mapping generic titles like "Incident Commander" to specific positions like CIO, CISO, Chief Medical Officer, or Privacy Officer. Templates should also define severity levels with corresponding response times and escalation protocols. When adapting a general-purpose template, replace generic references like "business applications" with healthcare-specific systems such as "EHR (Epic/Cerner)" and include steps for transitioning to paper charting and administering medications during system downtimes. These practical adjustments ensure the plan is both actionable and relevant to healthcare settings.
7. Incident Response Documentation and Workflow Structures Within Censinet RiskOps

Framework Alignment
Censinet RiskOps structures incident records around the NIST phases - preparation, detection and analysis, containment, eradication, and recovery. It uses predefined fields and steps that help security and compliance teams track actions and gather evidence, ensuring they meet NIST audit standards [3]. The platform also supports documenting HIPAA-related details for security incidents and potential breaches, such as affected PHI data elements, system ownership, and access logs. This approach aligns with templates used by organizations like NIH and other healthcare-focused frameworks [6]. Additionally, RiskOps workflows can be customized to reflect key elements from CHIRP and HICCouncil, such as clinical impact, operational status, and patient safety. This ensures cybersecurity incidents are documented with attention to care delivery and downtime procedures [3]. These structured workflows lay the groundwork for healthcare-specific documentation needs.
Healthcare-Specific Features
Censinet RiskOps builds on this foundation by capturing detailed information in incident records tailored for healthcare. These records include data types like PHI, medical record numbers, health insurance details, and billing identifiers, along with system ownership and the clinical application or medical device involved. They also track whether care delivery or diagnostic accuracy was affected [2]. For HIPAA/HITECH reporting, the platform logs key details such as discovery date and time, detection method, number of affected individuals, likelihood of compromise, mitigation actions, and supporting evidence like screenshots and time-stamped logs [2]. To address patient safety, the documentation flags disruptions in care, delays, or workarounds (e.g., switching to paper charting), following healthcare-specific incident response guidelines [5]. Organizations can also link incidents to vendor profiles and previous risk assessments, creating a comprehensive record. For example, a ransomware attack at a revenue cycle vendor can be documented in the context of related risk ratings and contractual obligations [3].
Incident Lifecycle Coverage
Censinet RiskOps supports a full incident lifecycle, which can be customized to include workflow stages such as initial triage and severity assessment, investigation and analysis, containment (e.g., isolating affected clinical systems or devices), eradication (e.g., malware removal or credential resets), and recovery (e.g., system validation and safe return to service) [3]. A post-incident review stage captures root-cause analysis, lessons learned, and updates to controls, promoting continuous improvement and refining response playbooks [3]. Notifications and approval checkpoints are integrated into each step, ensuring the workflow remains actionable and practical for everyday use.
Practical Usability
RiskOps workflows are built with diverse user roles in mind. For instance, clinicians can use simplified intake forms with straightforward prompts like "Is the EHR accessible?" or "Are lab results delayed?" [5]. Once submitted, security and IT teams access more technical fields for tasks such as log reviews, malware analysis, and network forensics [3]. Role-based views, conditional fields, and automated notifications ensure clinicians only provide information necessary for patient safety [2]. Additionally, organizations can establish incident types within RiskOps, such as playbooks for EHR downtime, medical device issues, phishing attacks involving PHI, lost or stolen devices, ransomware events, and third-party breaches. These playbooks come with pre-filled checklists and fields, making them useful for training and response drills [3].
Comparison Table
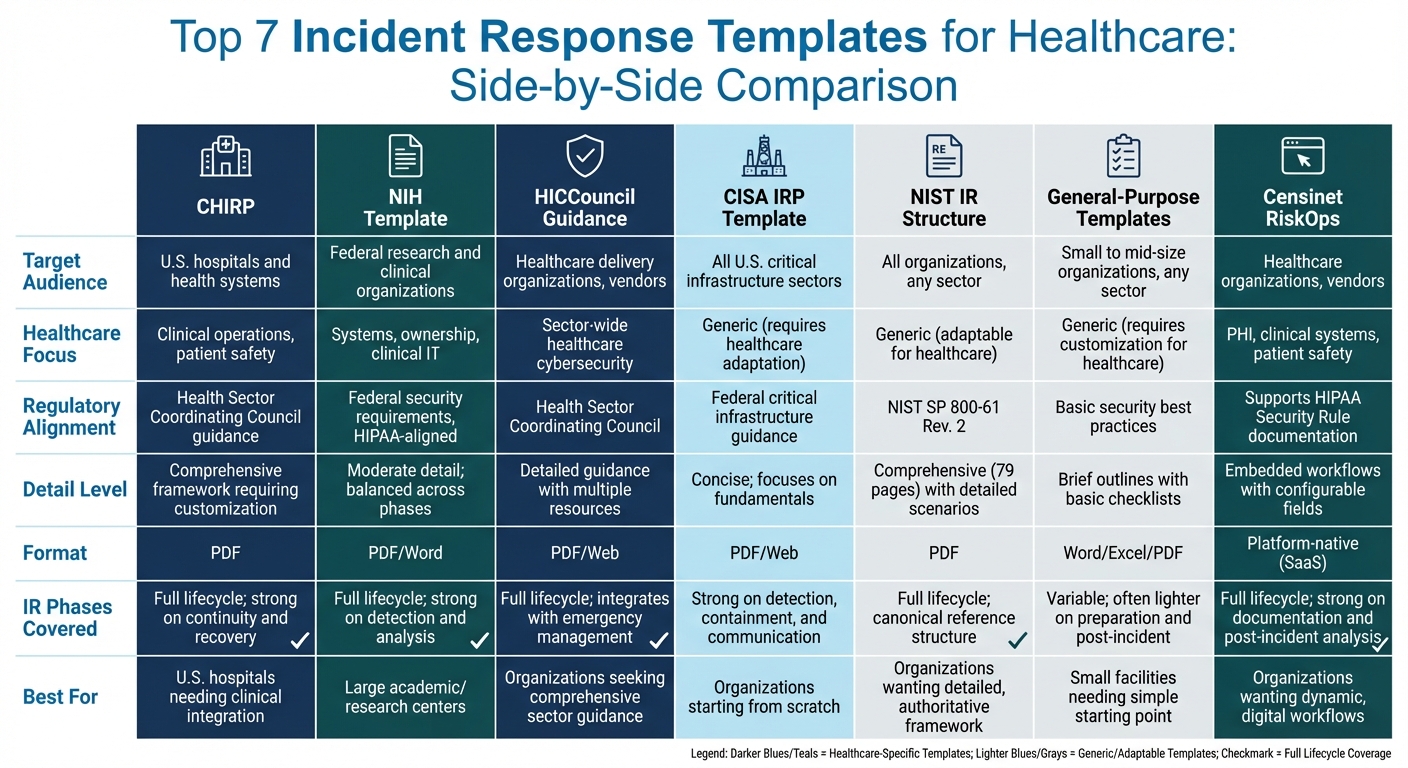
Comparison of Top 7 Healthcare Incident Response Templates
When it comes to incident response templates, they differ significantly based on their intended audience, focus within healthcare, usability, and how well they align with regulations. For example, CHIRP and the NIH template are specifically tailored for healthcare settings. CHIRP is designed to help U.S. hospitals and health systems integrate cyber incident response with existing clinical emergency management and downtime procedures. On the other hand, the NIH template is aimed at federal research and clinical organizations, offering a balanced approach across detection, analysis, and response phases, with a strong focus on system ownership. Meanwhile, HICCouncil resources provide broader guidance for healthcare delivery organizations and vendors, combining CHIRP with additional best-practice documents.
CISA and NIST templates, while not healthcare-specific, serve as foundational frameworks that require customization for clinical environments. CISA’s templates provide a straightforward starting point with basic steps and roles, but they need to be expanded to include clinical workflows, patient safety measures, and HIPAA-specific documentation. NIST’s SP 800-61 Rev. 2 delivers a detailed incident response lifecycle - covering preparation, detection and analysis, containment, eradication, recovery, and post-incident activities - which forms the basis for many healthcare-adapted templates. General-purpose templates, often created by state governments or security vendors, offer lightweight plans with simple checklists. However, these require significant adjustments to handle PHI and clinical operations effectively.
Most government-provided resources come in formats like PDFs or Word documents that are compatible with common office tools. For instance, NIST’s 79-page document includes detailed scenarios, while CISA offers concise, web-based guidance. General-purpose templates often include editable forms, like incident logs and contact lists, which make them easy to implement in both clinical and security settings.
Censinet RiskOps takes a different approach by embedding live, customizable workflows into a healthcare-specific platform instead of relying on static documents.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." – Matt Christensen, Sr. Director GRC, Intermountain Health [1]
This platform captures incident documentation, evidence, and follow-up actions within integrated workflows, shifting organizations from static policies to dynamic, measurable processes. It’s specifically designed with fields for PHI, clinical systems, and patient safety in mind.
Here’s a comparison table highlighting the key differences among these templates:
| Template | Target Audience | Healthcare Focus | Regulatory Alignment | Detail Level | Format | IR Phases Covered |
|---|---|---|---|---|---|---|
| CHIRP | U.S. hospitals and health systems | Clinical operations, patient safety | Health Sector Coordinating Council guidance | Comprehensive framework requiring customization | Full lifecycle; strong on continuity and recovery | |
| NIH Template | Federal research and clinical organizations | Systems, ownership, clinical IT | Federal security requirements; HIPAA-aligned | Moderate detail; balanced across phases | PDF/Word | Full lifecycle; strong on detection and analysis |
| HICCouncil Guidance | Healthcare delivery organizations, vendors | Sector-wide healthcare cybersecurity | Health Sector Coordinating Council | Detailed guidance with multiple resources | PDF/Web | Full lifecycle; integrates with emergency management |
| CISA IRP Template | All U.S. critical infrastructure sectors | Generic (requires healthcare adaptation) | Federal critical infrastructure guidance | Concise; focuses on fundamentals | PDF/Web | Strong on detection, containment, and communication |
| NIST IR Structure | All organizations, any sector | Generic (adaptable for healthcare) | NIST SP 800-61 Rev. 2 | Comprehensive (79 pages) with detailed scenarios | Full lifecycle; canonical reference structure | |
| General-Purpose Templates | Small to mid-size organizations, any sector | Generic (requires customization for healthcare) | Basic security best practices | Brief outlines with basic checklists | Word/Excel/PDF | Variable; often lighter on preparation and post-incident |
| Censinet RiskOps | Healthcare organizations, vendors | PHI, clinical systems, patient safety | Supports HIPAA Security Rule documentation | Embedded workflows with configurable fields | Platform-native (SaaS) | Full lifecycle; strong on documentation and post-incident analysis |
Choosing the right template is crucial to addressing both clinical and regulatory demands while ensuring your incident response strategy aligns with your organization’s unique needs.
Conclusion
Choose an incident response template that aligns with healthcare priorities, meets regulatory standards, and fits your operational realities.
Once you’ve picked a template, make it work for your specific environment. No template will fit perfectly out of the box - it needs to be tailored to your systems, roles, and contacts. This means embedding incident types into your technology stack, such as EHR systems, PACS, medical devices, and cloud services, while integrating it with your existing emergency management and downtime protocols.
Keep your plan fresh. Review and revise it annually, or whenever there’s a significant incident, system change, or regulatory update. Use insights from post-incident reviews and tabletop exercises to make continuous improvements. Organizations with well-documented and tested plans consistently respond faster and mitigate breaches more effectively than those relying on ad hoc methods.
Digital tools can make this process even smoother. Platforms like Censinet RiskOps™ help healthcare organizations manage complex risks by transforming static templates into dynamic workflows. These platforms centralize incident documentation, evidence collection, and follow-up tasks, focusing on healthcare-specific needs like PHI, clinical systems, and patient safety. This shift turns policy documents into actionable, measurable processes that adapt over time.
The best template is one that matches your organization’s size, complexity, and risk profile, while being practical enough for your team to execute in high-pressure situations. By prioritizing clarity and regularly updating your plan, you’ll be better equipped to protect patient care and meet evolving regulatory demands.
FAQs
What should I consider when selecting an incident response template for my healthcare organization?
When selecting an incident response template for your healthcare organization, aim for one that meets your specific needs. Choose templates designed to handle healthcare-related incidents, such as data breaches or issues with medical devices, and ensure they align with industry regulations like HIPAA.
Look for templates that emphasize fast response times, detailed documentation, and effortless teamwork between departments. It's also important to select options that work well with your current systems and workflows, allowing for thorough incident tracking and ongoing improvements.
How do healthcare-specific incident response templates differ from general-purpose ones?
When it comes to handling incidents in the healthcare field, specialized response templates are a must. These templates are crafted to tackle the unique hurdles healthcare organizations face, such as safeguarding sensitive patient information, adhering to strict regulations like HIPAA, and mitigating risks associated with clinical systems and medical devices.
On the other hand, generic templates often fall short. They typically lack the depth required for healthcare-specific scenarios and may overlook crucial elements like regulatory compliance or the high stakes of patient safety. Opting for templates designed specifically for healthcare ensures responses are not only more efficient but also align with industry standards and priorities.
How does Censinet RiskOps improve incident response for healthcare organizations?
Censinet RiskOps transforms how healthcare organizations handle incident response by delivering real-time risk assessments through advanced AI. This technology helps teams swiftly pinpoint and address potential threats, simplifying tasks like threat detection, vulnerability management, and compliance tracking. The result? Faster, smarter decisions when they matter most.
By automating critical tasks and fostering better collaboration among teams, Censinet RiskOps significantly cuts response times. It also helps safeguard patient data, protect clinical systems, and maintain seamless operations. This forward-thinking approach ensures healthcare organizations are better prepared to tackle the ever-changing landscape of cyber threats.


